Discover effective strategies to track and recover a stolen laptop, combining tech tools with practical steps to enhance your chances of retrieval.
Key Takeaways:
- You can use built-in or third-party tracking software.
- Employ remote locking and data wiping solution like Prey.
- Update passwords and report theft promptly.
- Explore preventive measures for future security.
In today’s cloud-based digital age, our laptops have become a very important tool for both personal and professional use. They store important information and data, making them critical assets for individuals and organizations alike, but sometimes it seems that our devices grew a pair of legs and disappeared. Knowing how to track a laptop and keep it safe goes beyond just protecting the device itself, it’s also a nice way to keep the information it contains safeguarded.
Having a stolen laptop can be a nightmare, and even more so for IT departments, as they must ensure that the confidential information stored in them remains confidential. In such cases, it becomes essential for IT departments to know how to recover the laptop, ensuring that important data and information remain secure. They must also be prepared for cases in which an employee simply refuses to return a borrowed laptop, like that time when an admin faked its death and fled with a borrowed device that contained confidential patient info subjected to HIPAA protection.
Oh, and by the way, the device was located using our tracking software, yay!.
How to track and recover a stolen laptop
The first thing you should know is that the best way to recover a stolen laptop is through a laptop tracking software. This way, you will be able to locate it accurately and in a timely manner. If necessary, you can ask the authorities for help to recover your computer safely.
How to recover a stolen laptop using Windows 10 or higher
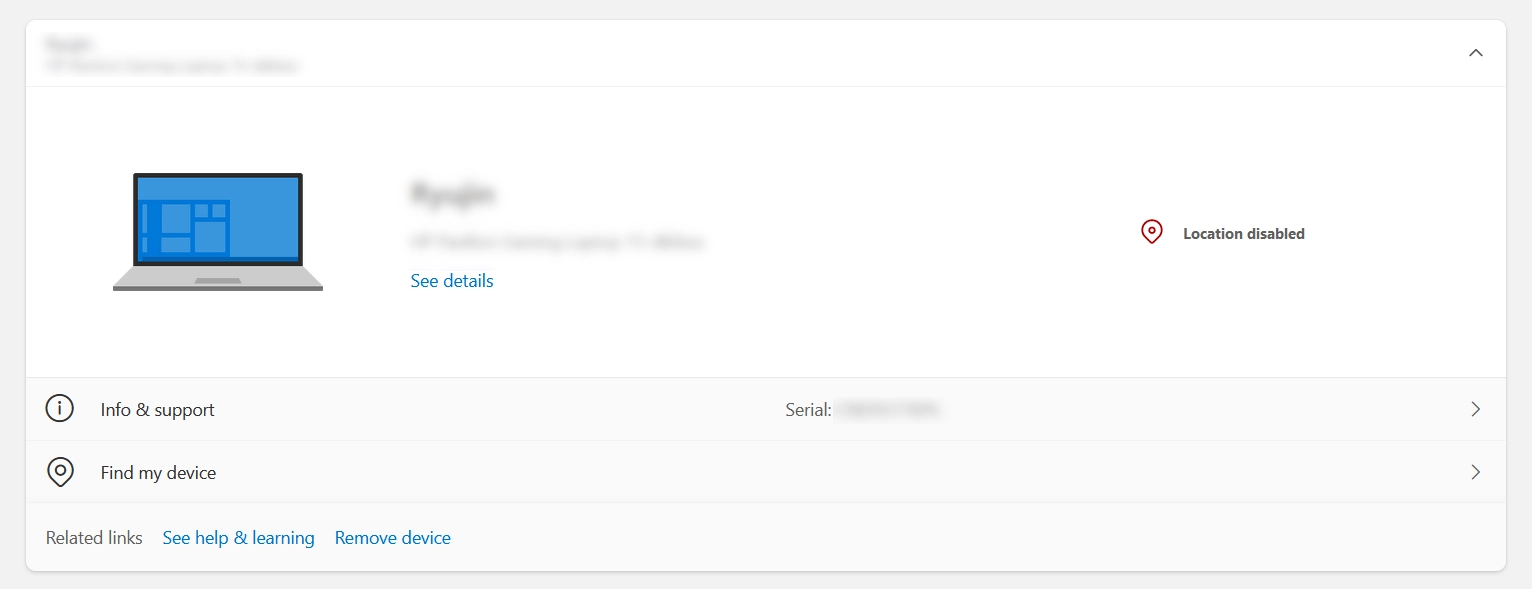
If you want to track a laptop running Windows 10 or higher, you can use the pre-installed "Find My Device" software to recover your laptop. Of course, you must have this service activated to use it to locate your device.
If you already have it activated:
- Go to Microsoft's device management page.
- Select the device you want to find.
- Click on "Find my device".
- You're done!
If you want to activate it:
- Press the "Start" key or press the key combination CTRL+S.
- Search for "Find My Device".
- Turn this option on.
- Try this option by performing the steps listed above.

How to recover a stolen Mac laptop
To track a stolen Mac laptop you must follow similar steps to those for Windows computers. Apple devices come with a factory-installed application for tracking devices. Of course, you must also have activated it beforehand.
If you have already activated it:
- Launch the Find My app on another Apple device, then select the Devices tab.
- On the Internet, log in to iCloud.com/find, then click "All Devices".
- Select the MAC device you need to find to view it.

If you want to activate it:
- On your Mac laptop, open the Apple menu, then "System Settings" and click your profile at the top of the sidebar. If you don't see your name, click Sign in with your Apple ID to enter your Apple ID or to create one.
- Click "iCloud" on the right.
- Click "Find My Mac", click Enable and click "Allow" when asked if you want "Find My Mac" to use your Mac's location.
- Test your settings by following the steps above

How to track and recover a stolen laptop using Prey
Through the Prey app, you can track Apple devices such as laptops and mobiles, Windows devices, and Android mobile phones. Please note that, as with the previous apps, you need to install the app and add your devices beforehand to be able to track an associated laptop.
If you already have Prey installed:
- Log in to the Prey Panel.
- Select the "Devices" tab in the right-hand menu
- Select the device to track.
- Mark as Missing and go to the missing reports tab
- Follow the device’s steps through the location history data

If you want to activate it:
- Create a Prey account
- Install the application on the device you will be using it on.
- Once installed, add the device to the dashboard
- Verify the correct configuration of the device by following the steps in the list above.
Additional actions you can do with Prey tracking capabilities
Track compatible Android, iOS, MacOS, and Windows devices
You can track multiple devices using our software, this way, you can locate and generate reports for fleet management. This is very useful for IT departments that want to keep track of fleets composed of laptops and smartphones with sensitive information and locate borrowed devices.
Keep an eye on the location history of devices
Prey can generate location history reports, so employers and IT departments can keep an eye on where certain devices have been. This can help in recovery cases, as said information can be used to create a list of possible places where a device can be found.
Activate automatic actions such as alerts and messages for specific geographic areas
Our software can be used to create a geofence zone, which can be used to designate safe or unsafe location zones. This in turn can be used to alert device owners about taking their devices out of a safe zone and message them to return the device or take extra precautions with it.
Disable the device with a Kill-Switch or delete its data with a remote wipe
You can use our kill-switch feature to remotely disable a stolen laptop that cannot be recovered. You can also use Prey to delete sensitive information stored in a device, which can be used to remove confidential information for a lost laptop or to wipe the data of a previous employee to lend the device to a new one.
Create reports including photos, screenshots, and device location data
Prey can generate customized reports that can help in recovery scenarios. Said reports include pictures taken from the lost laptop’s camera, screenshots of the device while it’s being used, location history, Wi-Fi data, and even changes done to the device’s hardware. These reports are very useful, as they can be used to identify who is using the device, where it is, and what it's being used for.
What to do after tracking your stolen laptop
Now that you've found your computer, you need to ask yourself the question: "Can I get it back without help? If you have located your laptop in a safe place, such as your work office or a hotel, you can probably go and get it without any problems.
But if it turns out that your laptop is in an unknown or potentially dangerous area, chances are that someone has taken it. In this case, the best thing to do would be to ask the local authorities for help, just make sure you have all the relevant information and witnesses who can identify your laptop as yours and help them recognize it.
As we already said, the reports that our software generates are very useful for these kinds of scenarios, as they can help the local authorities identify the person that took your laptop and verify that you’re the real owner of the device.
What to do if you can't recover your stolen laptop
If you can't recover your device, you can still take action to protect the data you have on it. The first thing you should do is use the same software we mentioned above to lock it down.
Microsoft
- Select the missing device.
- Use the "Lock" option.

MacOS
- In the "Find my" app, activate "Mark as Lost".
- Select the "Lock" or "Erase" option.

Prey
- Select your device
- Select the "Factory Reset" or "Custom Erase" option on the dashboard and follow the steps to erase the data
- Select the "Kill Switch" option on the panel and follow the steps to disable the device
Protect your information
If you can’t recover your laptop, you can still protect your information. Even if you don’t have physical access to its files, you can take some actions to reduce the potential damage that you can suffer from losing your device.
Recover your important data
If your laptop has access to software that allows you to back up your files to the cloud, then you should start uploading any important files to your cloud storage as soon as you lose them. The following steps involve deleting most of your files and information from your lost laptop, so you might want to quickly save your data before erasing it.
Delete your lost files
The next thing you should do is wipe your lost data. While Microsoft’s Find My Device doesn’t allow you to delete files, you can use Prey to remotely delete your files on windows devices. Macs are also compatible with our software, and you can also use Apple's Find my Mac to remotely erase your files.
Change your passwords and close your active sessions
Closing your active sessions to online services and platforms is the second thing you should do as soon as you lose your laptop. Doing this will prevent whoever has it from accessing critical services, such as your social media accounts, emails, or your bank accounts. You can do this by logging in from another device, such as your mobile phone, to close active sessions on other devices.
You should also change all of your passwords, this usually closes any active sessions of most online services and platforms, but even if it does you should still close your other active sessions. Some web browsers, like Firefox, allow you to wipe sync data like your saved passwords, which is something that you should do.
Notify your banking services
If you had your cards saved in your preferred e-commerce sites or their data stored in a document on your lost laptop, then you should notify your bank. This way you can save yourself from suffering additional financial losses from unauthorized purchases.
Remotely kill your laptop
You can use Prey’s Kill-Switch to remotely kill your device. This feature works by destroying the Master Boot Record of your computer, rendering it unusable. You can use this to get the last laugh, even if you didn’t recover your laptop.
Keep in mind that our Kill-Switch doesn’t permanently destroy the laptop, as any IT tech can apply some software magic to restore the device to its factory settings. This makes the kill-switch feature a very useful tool for IT teams that want to close unauthorized access to unruly employees, recover the device, and then restore it to make it work again.
How to recover a stolen laptop without tracking software
How to recover a stolen laptop without tracking software
Losing your mobile devices can be an incredibly nerve-wracking experience. It's even more stressful if you didn't install any tracking software, which can make it incredibly challenging to locate your lost or stolen device. However, there are several clever tricks and techniques you can use to find your missing item without relying on installing tracking software.
Call or text the device
Calling or texting a lost or stolen device can be an effective way of tracking it down. In many cases, simply calling the device will allow the person who has it to answer and provide its current location. Even if they don't answer, leaving a message with contact details could lead to them getting back in touch. If this doesn't work, sending a text message is another option. This can include information about how to return the laptop and any reward you’re willing to offer for its safe return.
Check with local authorities to report a stolen device
It's important to report a stolen device as soon as possible to increase the chances of recovering it. When reporting a stolen device, provide as much information about the laptop as possible. This should include its make and model, serial number, and any identifying marks or features that are unique to it. Be sure to also provide full contact details and a detailed description of when and where the laptop was last seen.
If you suspect that someone may be using your stolen device for criminal activity such as identity theft or fraud, notify your bank or credit card company right away so they can take appropriate action. They may block any transactions related to your account until further notice.
Consider a reward to find a device
When all other methods of locating a lost or stolen laptop without third-party tracking software have failed, considering a reward for its return can be an effective way of getting it back. Offering a reward can provide some incentive for anyone who may have found the device to report it in, as well as providing financial compensation for their time and effort.
If you decide to offer a reward, make sure that you advertise this widely and clearly state any conditions surrounding its collection. Advertising on social media can be an effective way of spreading the message far and wide, while also providing contact details so that anyone with information about the device's whereabouts can reach out directly. You could also print posters or leaflets about the lost laptop and post them up around your local area – this will help spread awareness and increase the chances of someone finding it and getting in touch with you.
How to secure your new laptop against theft
Protecting your data and your device is all about being proactive, as it is much easier to track a laptop and protect its information using already installed tracking and data security software. Preparing a new computer with security software will increase the chances that both your computer and your data will stay in your hands, even if you lose sight of them.
Here is a short list of security solutions you can apply:
Install tracking software
Using tracking software is simply the best way to recover a stolen laptop. Our tool not only offers device tracking solutions, but it also offers a few security extras that will allow you to generate reports for multiple devices, so you can identify criminals that steal them through screenshots of your desktop and webcam photos that you can take remotely.
Install data security software
Losing your laptop can result in losses beyond the value of the equipment itself. If you have saved your social media, work, bank, and cryptocurrency accounts on your web browser, then there’s a high chance that that information will be used to cause you even more harm. This is why you should install software that can remotely delete files and block access to your data and recover files by sending them to the cloud. Our solution in addition to device tracking also offers these solutions.
Avoid using pirated software
We understand that the cost of some work and everyday software can be very high. Nevertheless, using pirated software can be much more expensive than it seems. Avoid installing pirated software at all costs, as there is a good chance that it is compromised with spyware, cryptocurrency mining software, or ransomware.
Frequently Asked Questions
How can I locate a lost or stolen laptop without tracking software?
One way to try and locate a lost or stolen device is by offering a reward for its return, as this could provide some incentive for someone who may have found it. Additionally, you can advertise the fact that your laptop has gone missing on social media and/or print posters and leaflets about it to spread awareness around your local area.
What measures should I take if my laptop gets lost or stolen?
It’s important to take extra precautionary measures to protect any personal data that may be stored on the device. This includes changing all passwords associated with the computer, securing other devices connected to the same network, contacting banks and credit card companies linked to the device, enabling two-factor authentication for online accounts associated with it, and deleting sensitive information from cloud storage services.
What happens if someone finds my laptop and I can’t locate it?
Depending on how they find it, they may offer to return it out of kindness. However there are no guarantees that this will happen. Offering a reward might increase their chances of being found.


