
Never lose sight of your devices, recover and protect stolen data, and make sure your fleet stays manageable, no matter if it is on site, or out for remote work.
Track the whereabouts of laptops, tablets and mobiles, and make sure those that shouldn't be taken off site stay in their place with Geofences that alert exits or entries.
Actve tracking is Prey's default setting. It gathers locations when devices move, and in timed checks. If Active is disabled, you will have to locate by request.
Instantly know if a device leaves a designated area, or if it goes somewhere unsafe. Create geographic or radius safe perimeters to better monitor devices.
The GPS isn't active? Not an issue, we can triangulate it.
Easily see your entire fleet's location at once with the global map view.
Check for suspicious past positions, or find patterns when looking for a lost device.

When a device is lost and out of your reach, react with security actions to protect and recover your organization's assets, avoiding anyone from accessing it.
No stranger's hands will access your phone, tablet, or laptop if you remotely lock it.
Not all losses are theft, and not everyone's a thief. Try contacting the current device holder.
Your device will make a 30-second racket that can't be silenced to help you locate it.
Configure automatic actions, like the lock, alarm, and alert, for when a device enters or exits a specific Geofence.
Protect your own, and your organization's data with a set of data protection tools that's ready to wipe confidential information and usage data, or retrieve specific files.
Delete cookies, email data, documents, local cloud storage files, and custom directories on lost devices.
*Directory selection varies depending on the OS.
Select and retrieve specific files and avoid losing your work even after the device was stolen.
Activate Windows' full disk encryption tool remotely, BitLocker, to protect data, prevent filtrations, and meet security standards.
Press this emergency button for a quick defense. It will destroy the device's Master Boot Record, rendering the device unusable in a matter of minutes.
This feature remotely restores the device down to factory settings, removing all traces of use from the computer. It’s irreversible, it formats your hard drive and installs the OS all over again. It could take up to an hour.

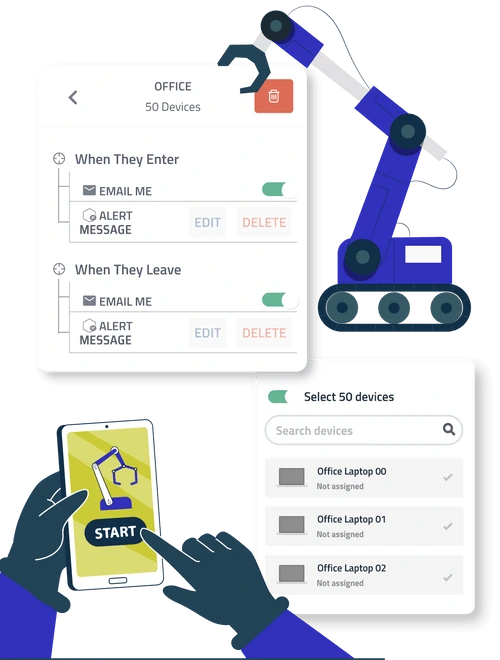
Manage fleets of any size and type. Handle laptops, tablets, mobiles. In the office or remote. You can automate swiftly locate, their security, and organize them in bulk.
Program recurrent, repeating, or one-time actions to streamline daily tasks, such as a curfew lock.
Quickly schedule and deploy our lock, wipe, alert, and alarm features to multiple devices.
Keep track and secure device loans, assign permanent users, see hardware changes, and maintain a record of all account activity for visibility.
Manage your devices with custom labels, with a robust search engine that can filter by hardware, OS, user, and a lot more. Use filters to create device Groups.
View your entire fleet's activity globally with graphic insights regarding their movements, recent reports, demographics, and checked-in status.
Silent and unattended installers for every OS, automatic updates, and custom APKs.
Consume data from your account, develop integrations with third-party platforms, and trigger changes/actions.
Create roles, groups and users, customize their permissions and edit them according to your preferences.
The recovery begins when you mark a device as missing in the panel. The Evidence Reports will activate and deliver crucial evidence for the police, in custom time-frequencies.
