Cover all of your devices, from multi-os laptops, tablets, and corporate mobiles, under a single platform. Organize them in groups, assign them users, labels and automate their management.
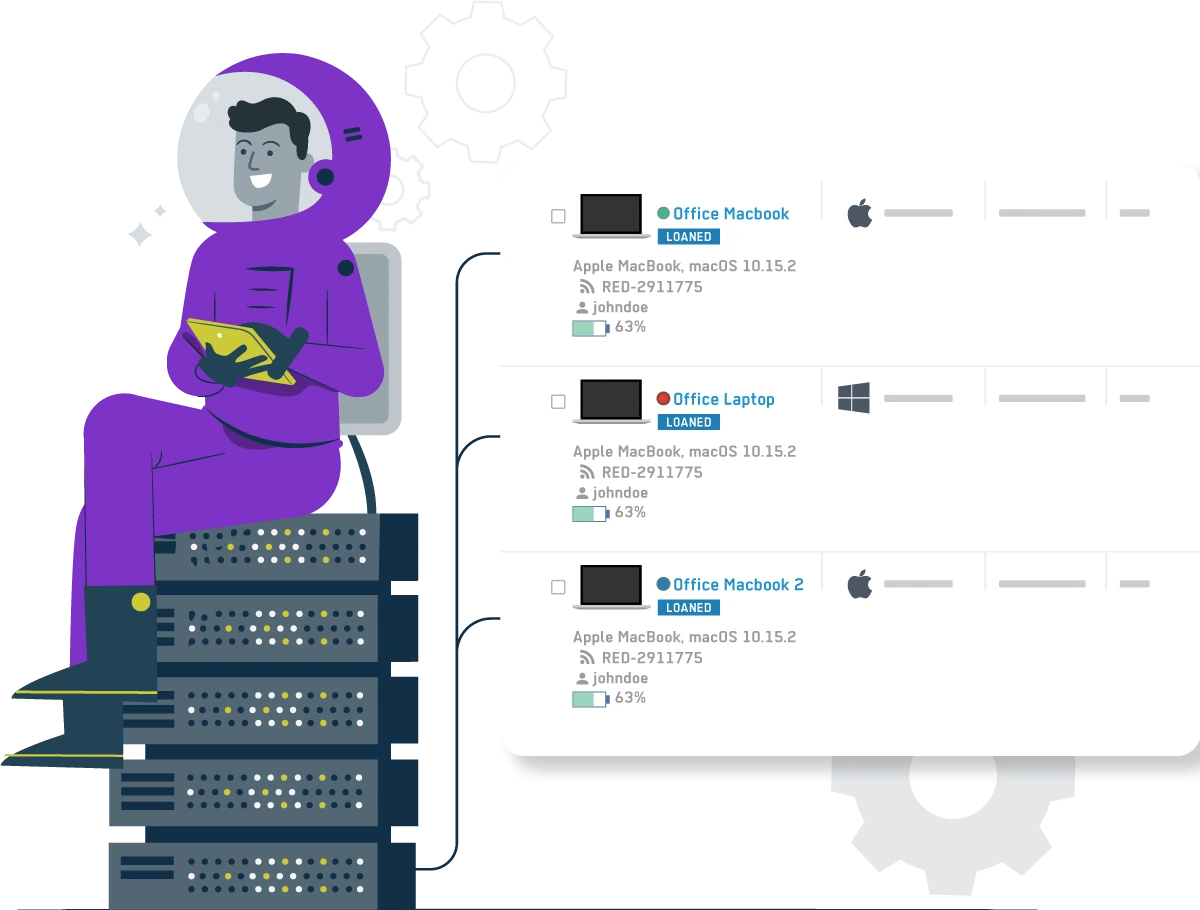

Have a thorough inventory of your on site and off site remote fleet, its hardware, assigned user, and activity.
View each device's hardware, operating system, and modifications carried out on these two.
Keep a tab on the user that has been assigned to the device, and connect it to an institution.
Check if the device is online or when it was last seen, see its active network, battery status, and which active user is currently logged in and using it.
Export your fleet's complete data for review, presented in a formatted csv file right to your account's email.
Maintain a registry of your account activity and all actions or modifications made by users for better accountability and auditing.

Deploy Prey in bulk and easily manage hundreds of devices by grouping and assigning them.
Create time-based rules, or event-triggered actions to automate security and device management.
Quickly schedule and deploy our lock, wipe, alert, and alarm features to multiple devices at once.
Silent and unattended installers for every OS, automatic updates, and custom APKs.
Lend and keep track of devices with or without a return date, send automatic 'time's up' alerts, or lock and track the equipment when not returned.
.webp)
Stay on top of your device fleet's security with custom risk detection alerts and information.
View your entire fleet's activity globally with graphic insights regarding their movements, recent reports, demographics, and checked-in status.
Configure Prey's notification settings regarding Geofence movement detection, missing device evidence reports, alerts for suspiciously offline devices, and more.
Review the device's triggered events in the platform, hardware modifications, and connections.
.webp)
Access a platform that's ready to adapt to your privacy policies and management needs.
Assign additional account admins or create as many user profiles as you need with customizable access privileges.
Prey's tracking and security tools are customizable and can be turned off comply with an enterprise's user privacy policies.
Access further iOS and macOS management capabilities by linking your Prey account to an MDM certificate by Apple.
Set up an extra layer of security in your account by adding 2-factor authentication.
Access new ways of using your account's data with Prey's API, enabling integrations and external developments.

Create users, implement existing roles or fabricate your own, assign permissions and groups according to your organizations' needs.
Easily create as many users as you require, you just need their organization email. Each user gets a setup API key.
Each user may have devices assigned to ensure they focus their efforts where they are needed most.
Select the degree of access you allow your colleagues. Amplify teamwork scaling action deployment, device access, account view and more.
Classify your devices creating custom labels that let you search by department, office, team, organization division, whatever works.
Use custom labels to create groups and break down your fleet to enhance administration using segmentation.