With the growing adoption of BYOD (Bring Your Own Device) and One-to-One Mobility Programs by educational institutions, there's a parallel surge in both the benefits and potential digital vulnerabilities they encounter. This transformation has undeniably enriched the learning environment, fostering a more interactive and tailored experience for students.
Yet, this progress doesn't come without challenges. Beyond the complexity of managing such a wide array of devices lies the even greater task of safeguarding them from threats. These threats span from external cyber-attacks, internal breaches, careless users, or thefts. This is precisely where Prey steps in to address these concerns.
Furthermore, it's worth noting that Prey can also assist educational organizations in locating misplaced or lost devices. In fact, there is a higher likelihood of students and staff misplacing their devices, with a rate approaching 64%, as revealed in our 2020 in-house study, the Mobile Theft & Loss Report.
But, how much money can a single missing device cost a company?
According to a 2014 Ponemon Institute study, the financial repercussions are substantial. On average, organizations incur losses of $3.44 million annually due to lost or stolen mobile devices. Bear in mind that these amounts are outdated, and as of 2023, the global average cost of a data breach amounts to 4.45 million U.S. dollars according to IBM’s Data Breach Report 2023 report.
Prey Capabilities:
Prey offers an integrated platform designed to manage and protect a vast range of devices regardless of their operating system. Given the diverse nature of device use in schools, where multiple operating systems and devices co-exist, Prey's multi-OS and multi-device readiness ensures a seamless management experience, making it an optimal choice for schools looking to safeguard their technological assets.
Prey's Continuous Tracking and Location Features
The ability to track and locate devices is crucial for schools. Not only does it protect the institution's investments, but it also serves a dual purpose of ensuring the safety of students and staff. With Prey's continuous tracking system, schools can monitor the whereabouts of their devices, helping them to respond to incidents of theft or loss swiftly.
In the event of an incident, Prey utilizes location tracking to pinpoint the specific geographic whereabouts of the devices, thanks to:
- GPS-based Tracking: The primary means of tracking, Prey uses the device's built-in GPS system to pinpoint the exact location of a device, providing high accuracy especially when the device is outdoors.
- Wi-Fi and Network Information: In situations where GPS might not be available or accurate, such as when the device is indoors, Prey uses surrounding Wi-Fi networks and their signal strength to triangulate the device's position.
- GeoIP Location Tracking: By examining the IP address a device is connected to, Prey can estimate its geographical location. This method is particularly useful when other more precise methods fail. However, the accuracy may vary as it depends on the IP address database and might only provide a general area or city-level accuracy.
While these two do not technically count as “continuous tracking” Prey also keeps track of these bits of information to locate devices:
Geofencing: Users can set up geographical boundaries using Prey. If a device crosses these predefined boundaries, Prey sends a notification alerting the user.
Location History: Prey maintains a record of the device's location history. This is beneficial in establishing a pattern of movement, which can aid in recovering a lost or stolen device.
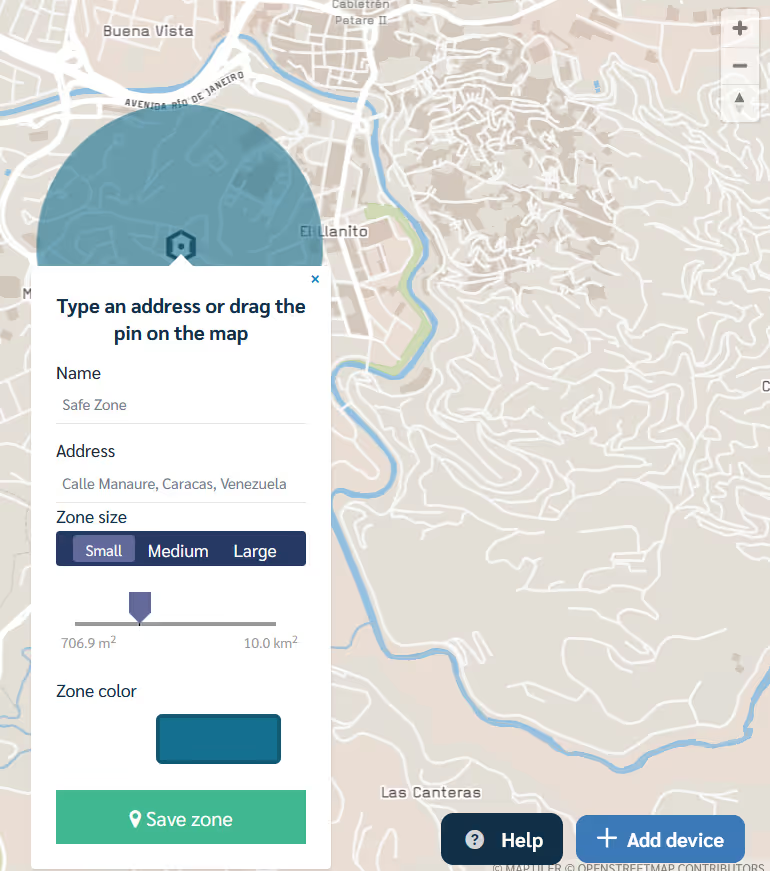
Geolocation monitoring with Control Zones
Prey's Geolocation feature, paired with our geofencing features, provides schools with the capability to set geographical boundaries for their devices. This means schools can receive alerts if a device enters or exits a designated area, ensuring devices remain within school premises and aiding in swift recovery if they don't.
Here's how these features can be used to enhance the safety of both students and their devices:
- Real-time Tracking: By utilizing geolocation, educational institutions can track the real-time location of devices. This ensures that stolen or misplaced devices can be quickly located and recovered.
- Setting Boundaries with Geofences: The Control Zones & Alerts feature allows schools to create geofences. Schools can set up zones such as "School Premises" or "Library" and receive alerts when devices enter or leave these zones. This is especially beneficial for ensuring devices don't leave school grounds.
- Establishing Safe Zones: Control zones can be set up around the school or campus premises. These control zones can be used to monitor the location of devices, which in turn can help protect students through the use and assignation of safe zones.
- Emergency Alerts: Similar to devices, safe zones can be established for students, particularly those on field trips or off-campus activities. If a student steps outside a designated zone, immediate notifications can be sent to concerned authorities or guardians, ensuring rapid response in case of emergencies.
Automated Reports
Utilizing Prey's device marking feature, schools can easily label and categorize their devices. Moreover, regular reports can be generated to keep track of device activity. Regular reports and appropriate device marking are essential components of an effective device management strategy.
By consistently tracking device activity, organizations can ensure they are compliant with industry standards and regulations. This also significantly aids in streamlined audits, providing clear evidence of adherence to protocols and reducing the likelihood of non-compliance issues.
Importantly, these automated reports can be disabled as needed to comply with FERPA regulations.
Global Fleet Location Overview
Prey offers a global fleet location overview, allowing schools to view the location of their entire device fleet simultaneously. The Global Fleet Location overview feature offered by Prey gives schools an eagle-eyed view of all their devices' locations on one map. This holistic view is vital in maintaining control over large volumes of devices, especially in educational institutions where tracking individual devices can be cumbersome.
How Global Fleet Location Overview Helps in Tracking Missing Devices:
- Quick Identification of Device Location: At a glance, IT administrators can spot the precise location of a specific device. This is especially useful if a device is marked as missing or is not in its designated location.
- Time-Efficient: Instead of tracking each device individually, the Global Fleet Location provides an aggregated view, saving considerable time and effort.
- Optimized Resource Deployment: In case of a missing device, knowing its last location can help direct resources efficiently for recovery, rather than a blind search.
- Historical Data Analysis: The feature provides a history of device movements. If a device goes missing, analyzing its historical data can provide clues or patterns leading up to its disappearance.
Stop device recollection chaos
Managing a vast inventory of devices in schools is a daunting task. Proper inventory management can significantly reduce instances such as the end-of-the-year device recollection chaos. With tools that facilitate monitoring and categorizing checkout devices, IT admins can maintain better control over their tech resources.
Loans and Users Assignment
Prey's Loans and Users Assignment feature is tailor-made for institutions that lend devices to students or staff. It allows schools to set loan periods, activate security protocols when overdue, and designate users for each device, ensuring devices are returned on time and remain secure.
Managing educational devices often involves temporary allocation or long-term assignment to users. Ensuring device safety and tracking during these times is critical. With Prey, institutions can simplify the device loan process and maintain stringent accountability.
Here's how Prey's loan features can significantly help:
- Integrated Device Loan Manager: Seamlessly lend out devices, either temporarily or indefinitely, with complete traceability.
- Automated Alerts: Timely reminders are dispatched to users when the loan tenure nears its end. This proactive approach minimizes late returns and enhances accountability.
- Enhanced Security on Overdue Loans: Should a device loan exceed its tenure, Prey activates security protocols to safeguard the device's data and sends notifications to the administrator, ensuring prompt action.
- Diverse Loan Options: Prey offers multiple Loan options to IT administrators
- Open-ended Loan: Loan out a device without a predetermined return date, offering flexibility to users.
- Unsecured Timed Loan: Assign a device with a specified return date but without additional security measures.
- Secured & Timed Loan: Provide a device with a designated return date, paired with automatic security actions if the loan period expires.
- Accountability and Monitoring: Detailed logs and reports ensure administrators can quickly gauge the status of loaned devices, the users they are assigned to, and any pending actions or alerts.
Prey’s Device Lockdown Protocols
Theft deterrence isn't just about tracking; it's about making thieves think twice before stealing something. While these features are primarily available for Windows devices, they can drastically reduce the allure of stolen school property.
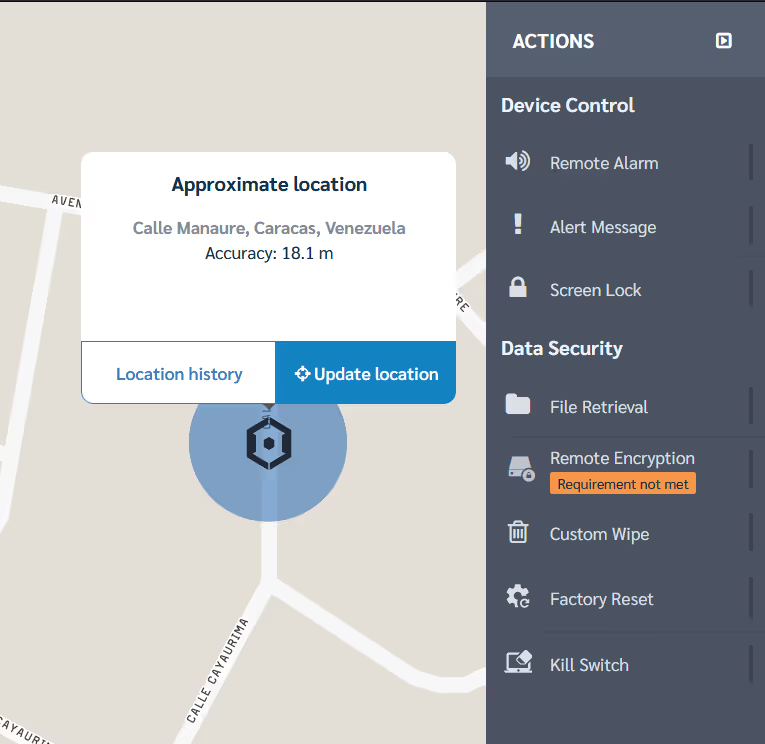
Remote Screen Lock
To further enhance device security, the option to remotely lock a device's screen is invaluable. If there's suspicion of unauthorized access or if a device is momentarily unattended, remote screen locking can act as an immediate safeguard. This prevents potential breaches and offers an additional layer of security while the situation is assessed.
With Prey's Screen Lock feature, schools can remotely lock any device, preventing unauthorized access and safeguarding sensitive data.
Remote Wipe and Factory Reset
In the event of a security breach or if a device is lost or stolen, having the ability to remotely wipe data or perform a factory reset is crucial. This ensures that sensitive data doesn't fall into the wrong hands, safeguarding both company information and user privacy.
If a device is deemed irrecoverable, Prey offers the ability to remotely wipe data or perform a factory reset, ensuring confidential school information remains protected.
Benefits of Prey in schools
Adopting Prey in educational settings comes with numerous advantages. From ensuring device security and accountability to streamlined device management and swift responses to theft or loss incidents, Prey emerges as an essential tool for contemporary schools. The benefits include:
- Centralized and Multi-OS device management
- Robust security measures
- Quick response to thefts and losses
- Streamlined inventory management
- Ensured compliance with regulations like FERPA
Elevating school security with prey
Confronting the device management and security challenges of today's educational institutions requires a holistic approach. With Prey, schools can navigate these challenges effectively, ensuring a secure and efficient learning environment. Serving as a comprehensive solution, Prey stands out as an indispensable ally in preventing device theft in schools.