Data protection and security
Don't let a rogue device turn into a security breach
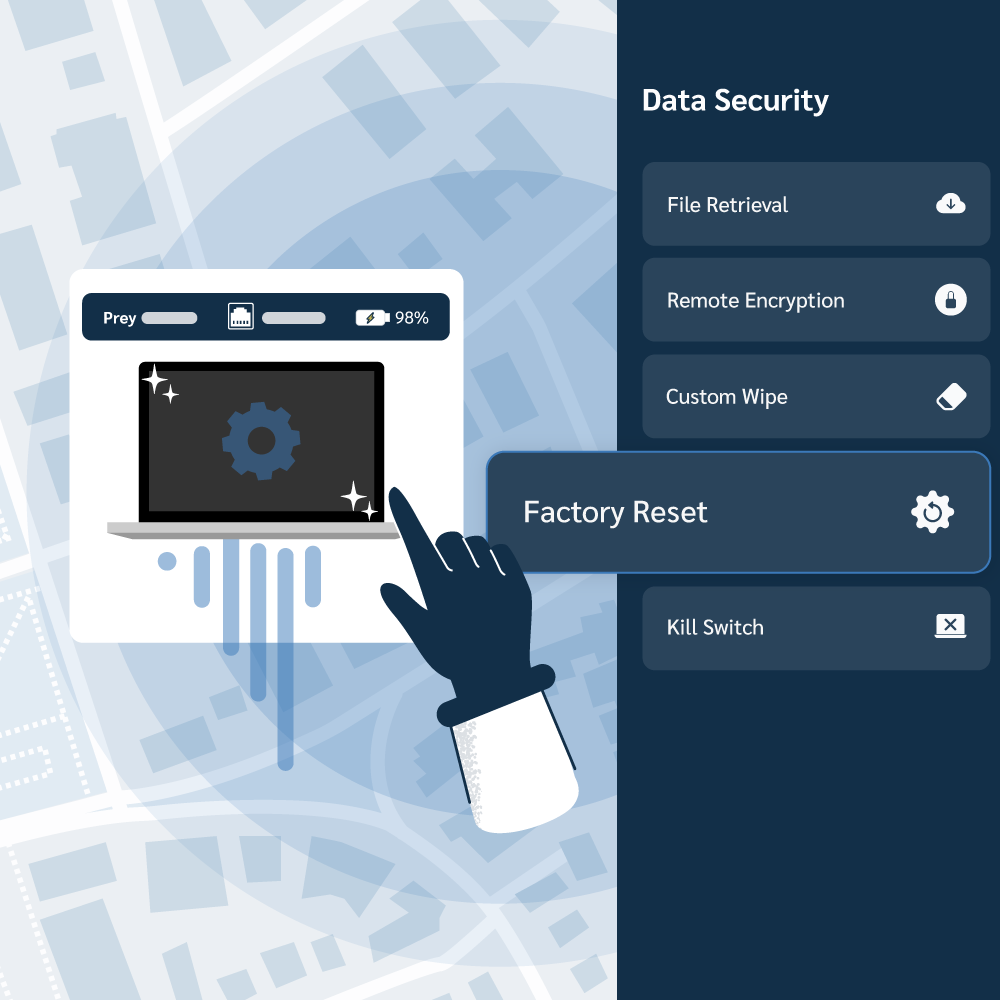
Prey's remote actions allow you to instantly lock screens and wipe sensitive data, safeguarding your business from theft and unauthorized access, preventing data breaches, and meeting compliance requirements.

The high cost of compromised data
Data breaches
Unauthorized access to a lost device can lead to the exposure of confidential client data, financial records, or intellectual property.
Compliance violations
Unprotected sensitive mobile data leads to severe penalties and reputational damage.
Operational disruption
Responding to security incidents, from client notification to forensic analysis, significantly drains business resources.
Credential theft
A stolen device can be a gateway for malicious actors to gain access to your network, employee accounts, and other critical systems.
The Prey solution:
Get proactive data security
Take back control, instantly
Prey's dashboard offers immediate control: see a device's location, wipe data, lock the screen, or generate a security report, all from one place to protect data and respond to threats whenever devices are connected to Prey servers. Most actions remain pending when devices are online, and resume once they are back online.
Explore more
Corporate laptop asset tracking guide for 2026. Learn how tracking works, key features, compliance requirements, and how to protect distributed teams.
Discover Prey’s 4-layer security approach: device tracking, remote protection, asset management, and dark web breach monitoring, all in one platform.
Frequently asked questions
Below, you'll find answers to commonly asked questions about our products/services. Feel free to reach out to us directly for further assistance. We're here to help!
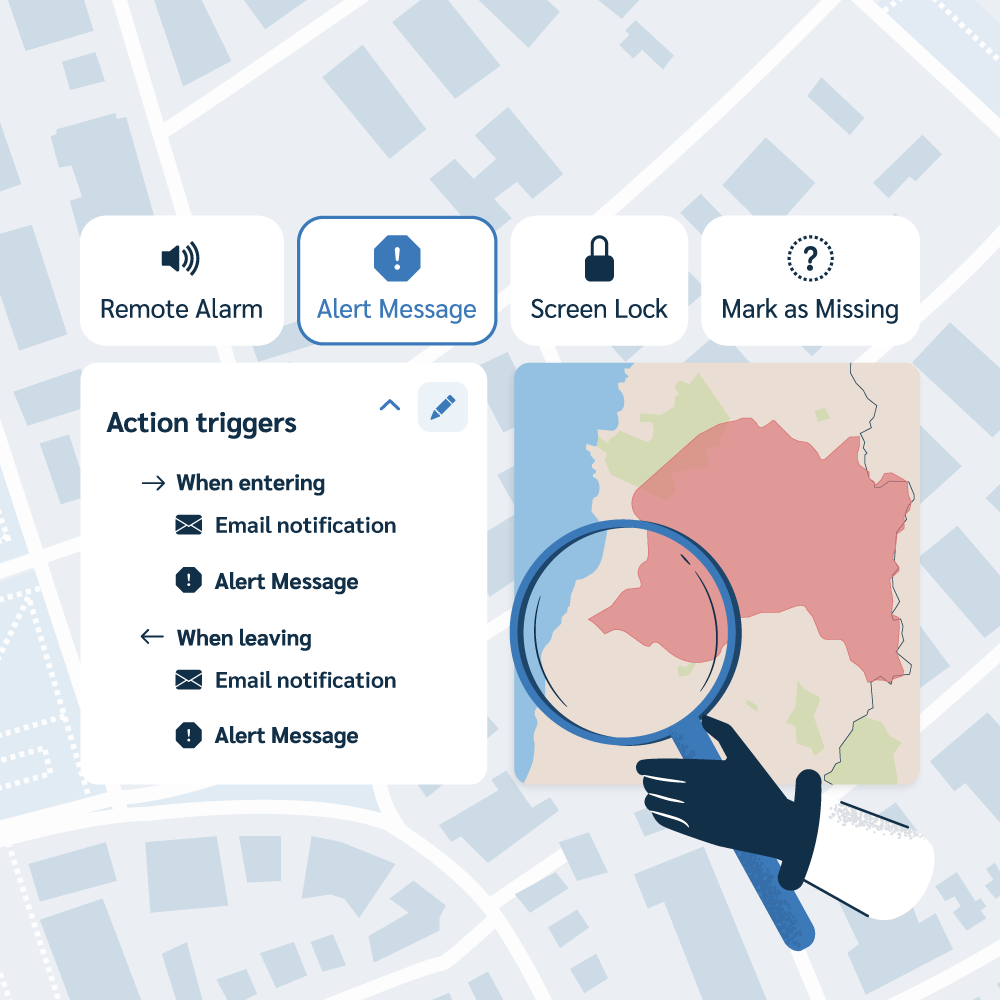
Prey goes beyond simple tracking. Our platform provides a suite of remote security actions, such as Screen lock, Custom wipe, and Remote encryption. These tools empower you to instantly secure a lost or stolen device and protect confidential information from falling into the wrong hands.
Yes. Prey helps organizations meet standards like GDPR, HIPAA, NIST, and ISO 27001 by providing audit logs, encryption, and rapid data protection measures for lost, stolen, or rogue endpoints.
Custom wipe offers a targeted approach, allowing administrators to selectively delete specific data such as files, downloads, photos, and contacts, without affecting the device's operating system. A Factory reset is a more thorough action. It remotely executes the operating system’s native factory reset, restoring the device to its original, out-of-the-box factory state.
Breach Monitoring is a proactive security tool that scans the dark web for any leaked credentials or personal data associated with your company. This gives you an early warning if a breach has occurred, allowing you to take action and change passwords before a stolen device is even used to access your accounts.
A:Yes and no. Prey allows you to remotely send instructions to initiate BitLocker encryption to compatible Windows devices. This ensures that even if the hard drive is physically removed from the machine, all data remains encrypted and unreadable to anyone without the decryption key. It provides a critical layer of defense against data theft, but it is dependent on Windows Bitlocker, so it is not available on other operating systems.
Missing reports are crucial in finding stolen or misplaced devices. They collect comprehensive evidence, including location coordinates, built-in camera photographs, screenshots, and network information, all vital for recovery.
Prey is designed for immediate action. As soon as you log into your Prey dashboard, you can remotely trigger a lock, or other security actions fast. These commands are executed the next time the device connects to the internet, ensuring your data is protected as quickly as possible.