Remote workforce management & security
Manage a workforce that’s everywhere
Managing devices for a distributed team can become a complex logistical operation. Prey provides a powerful and effortless way to monitor devices to keep track of their deployment, giving you total visibility over your remote workforce. From onboarding to off-boarding.
The challenges of a modern, distributed workforce
No visibility
You have no insight into the location, status, or use of company devices, making inventory management and security audits nearly impossible.
On/Off-boarding chaos
Manually provisioning devices for new hires and securely wiping devices from departing employees is time-consuming, error-prone, and potentially vulnerable.
Security gaps
Unsecured remote devices are vulnerable to loss or theft, creating a high risk for data breaches and compliance violations.
Geographic blind spots
Unable to enforce different actions based on where devices are: office, remote sites, or in the field.
The Prey solution:
Maintain full visibility across your entire fleet
Your remote workforce, in one place
The Prey Panel is your command center for a distributed team. Visualize every device on a map, see its status, and take action with a single click. Manage your fleet with confidence.
Explore more

Remote work expands your attack surface. Learn the essential controls—MFA, encryption, endpoint protection, MDM, and lost device response—to stay secure.
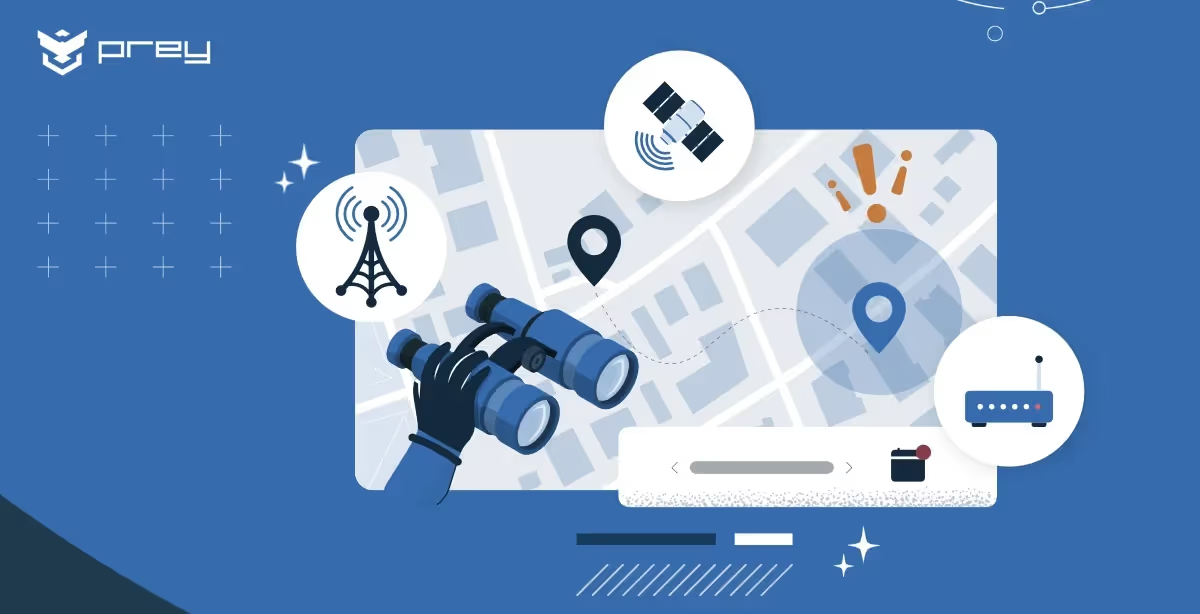
Discover Prey’s 4-layer security approach: device tracking, remote protection, asset management, and dark web breach monitoring, all in one platform.
Frequently asked questions
Below, you'll find answers to commonly asked questions about our products/services. Feel free to reach out to us directly for further assistance. We're here to help!
Prey is not focused on MDM features, but it provides the essential device management and security capabilities that a remote workforce needs. We focus on core functions like device tracking, security actions, and streamlined device management, making us an ideal, lightweight alternative for organizations that don't require the complexity of a full MDM.
Unattended installation allows you to deploy the Prey agent to multiple devices in a near zero-touch manner. You can use your preferred deployment tool to install the agent. Prey also has app packages available for mass MDM deployment without any manual intervention from the employee. This streamlines the onboarding process, ensuring that every new device is secured and managed from day one.
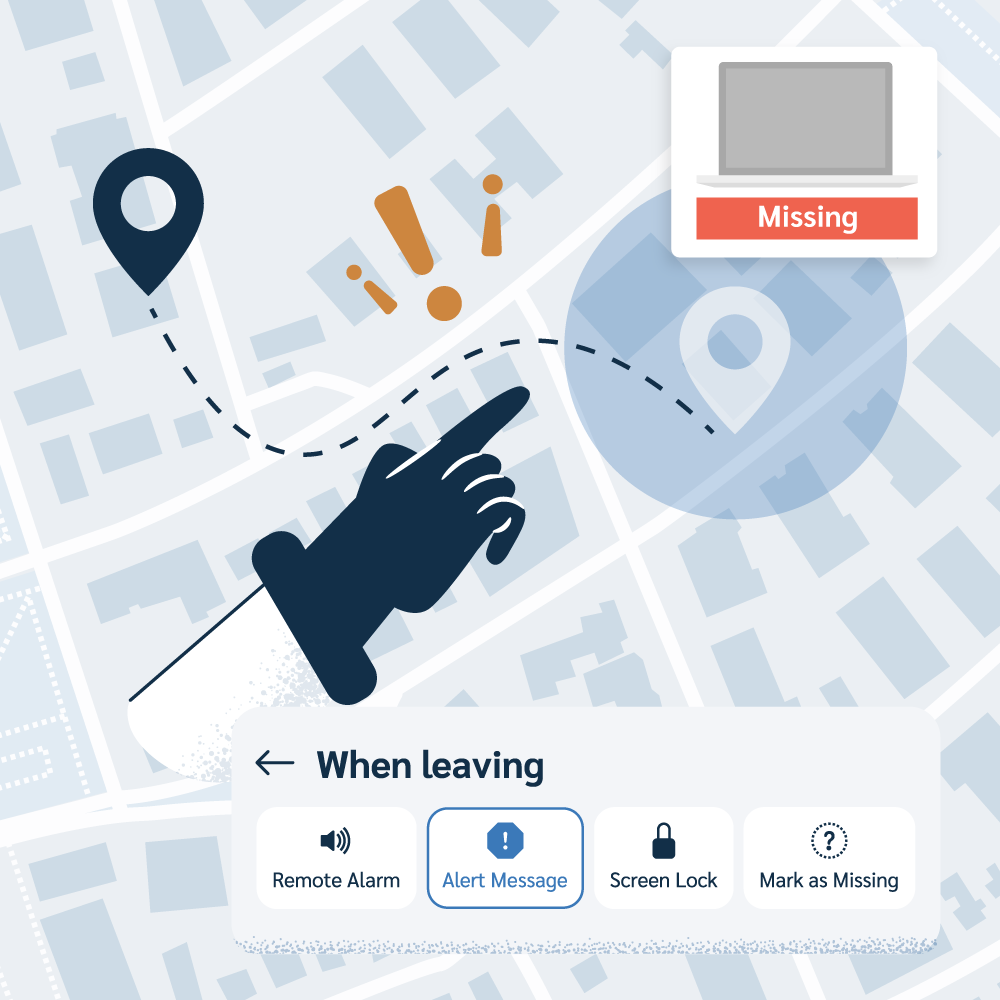
Geofencing allows you to create boundaries around specific locations, like your office, campus, or a client's site. You can then set up automated actions based on a device's location. For example, you can have a device automatically locked when it leaves the office and marked as missing when it leaves town, so you automatically get location reports, helping you enforce policies remotely.
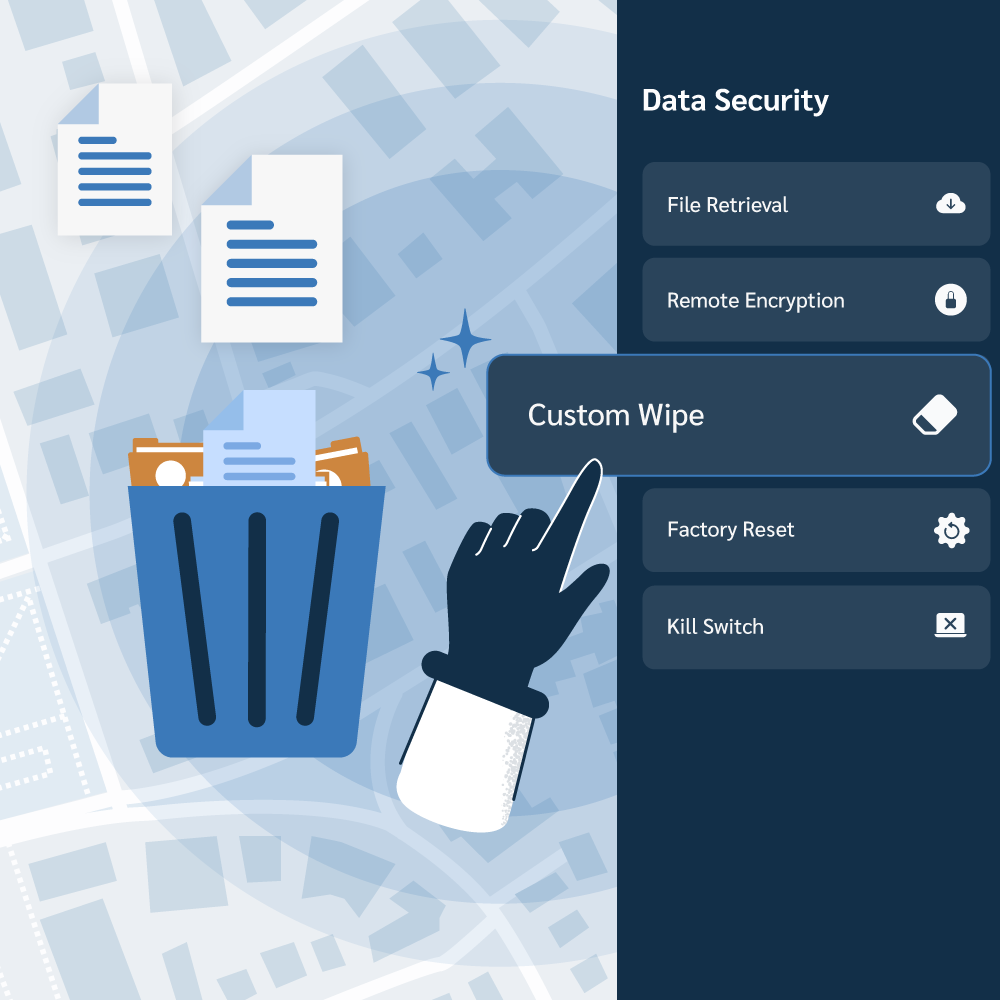
When an employee leaves, Prey gives you tools to control their company-assigned device. You can easily remove access to the device and remotely trigger security actions to securely erase data. This way, if you can’t recover the hardware, you’ll at least remove all company data to protect your assets and disable the machine entirely.
When a device is offline, you will see its last known location and status in your panel. Any actions you trigger, such as a remote lock or data wipe, will be queued. The moment the device reconnects to the internet, these commands will be executed automatically, ensuring your security policies are always enforced as soon as possible.
Yes. Prey is GDPR compliant. We take data security very seriously. All data transmitted between your devices and our platform is encrypted. We also have robust security protocols in place to ensure that your device information and any data gathered through security actions are protected and accessible only to authorized users within your organization. Read more about our Security and Compliance standards.