Compliance and enforcement
From policy to regulation, keep compliance in check
Compliance is about proving policy enforcement, not just writing policies. Prey automates security rule application across devices, providing audit evidence and reducing risks in dynamic environments.

The high stakes of non-compliance
Hefty fines and penalties
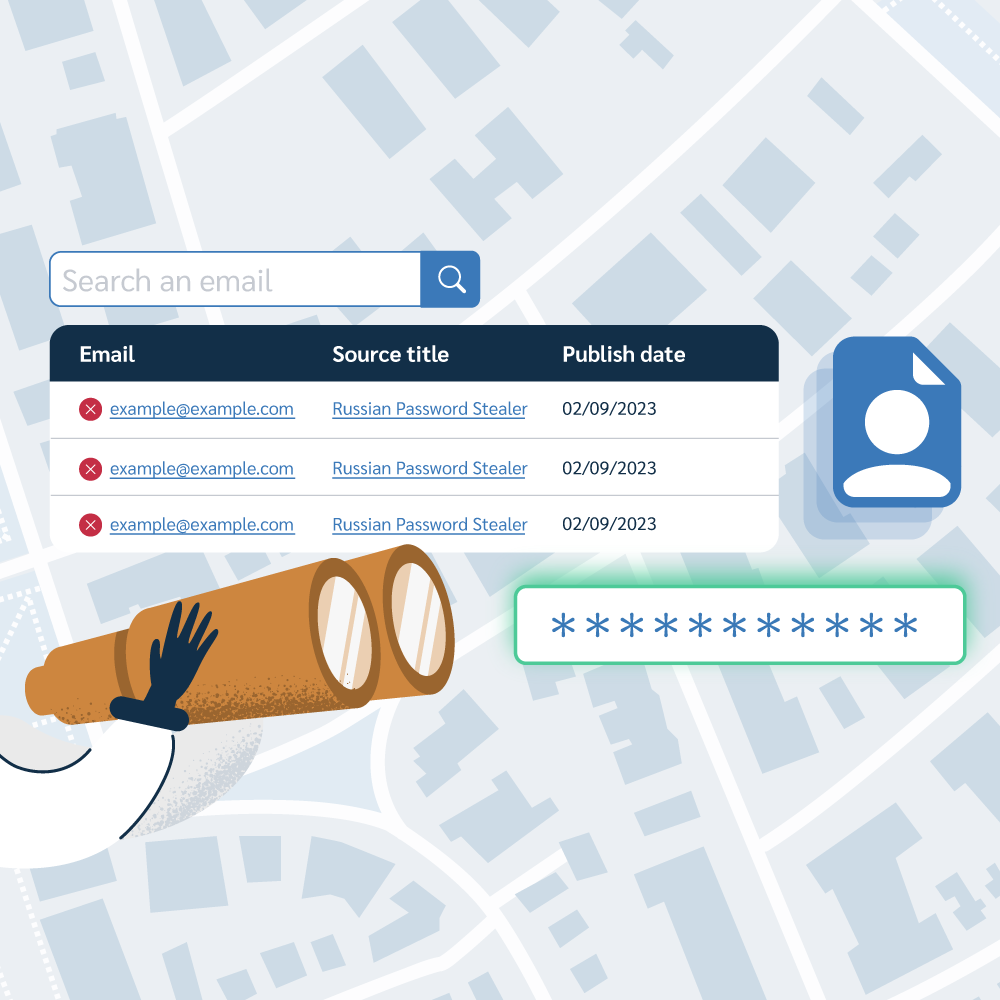
Regulatory bodies such as GDPR, HIPAA, and SOC 2 (to which Prey is compliant) can impose significant penalties if organizations fail to demonstrate that sensitive device data is secure and accounted for.
No audit trail
Manually gathering complete device history is slow and error-prone. The lack of objective evidence to prove compliance, risks audit failure and fines.
Weak accountability
Weak accountability: Without objective evidence, taking disciplinary action against misuse or lack of accountability is difficult, lowering performance and results.
Operational blind spots
Devices used outside approved locations or for unauthorized purposes create vulnerabilities that can expose sensitive data and lead to security incidents.
The Prey solution:
Automated compliance and enforcement
Your compliance command center
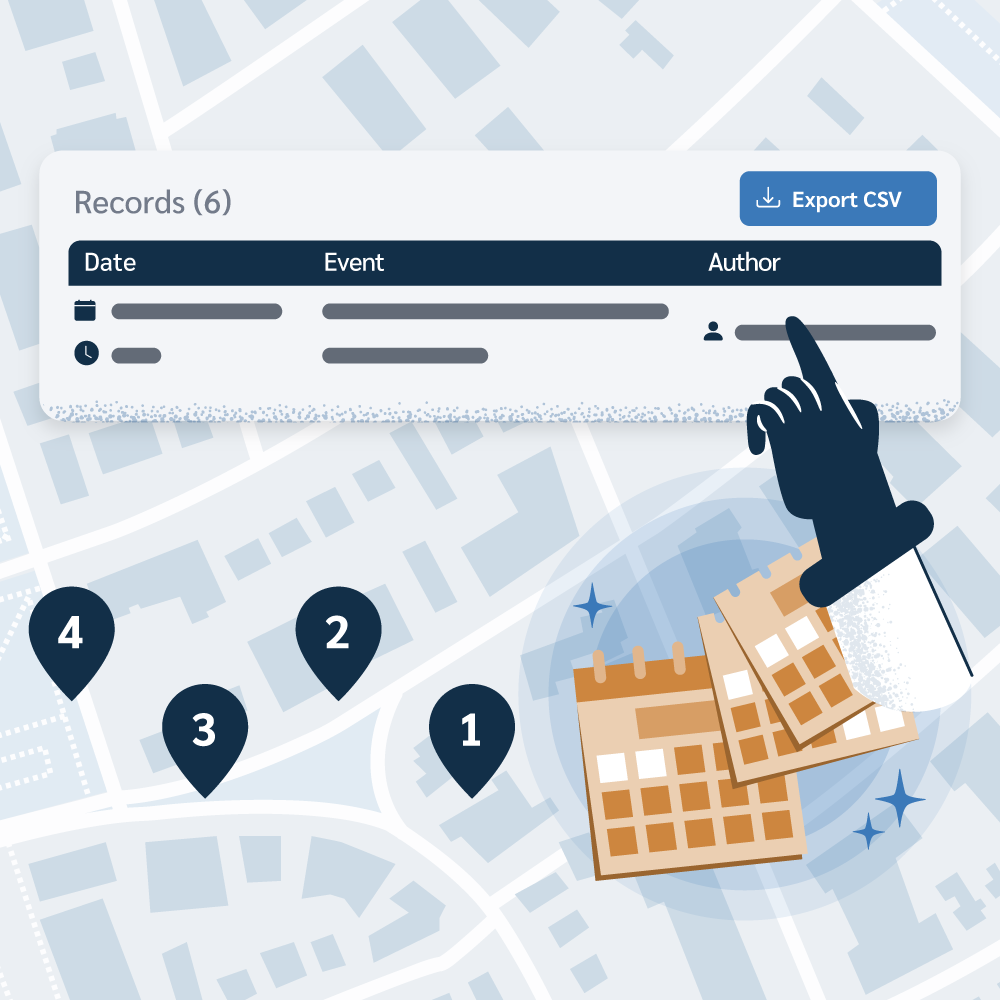
The Prey dashboard brings clarity to your compliance challenges. Track every device, user, and their adherence to your policies. Pull up a device’s location history, review your account’s Audit log, and check other activities to get a complete, auditable picture for total regulatory readiness.
Explore more

FERPA doesn’t care if your IT team is small. Prey helps you secure student data without burning out
Discover Prey’s 4-layer security approach: device tracking, remote protection, asset management, and dark web breach monitoring, all in one platform.
Frequently asked questions
Below, you'll find answers to commonly asked questions about our products/services. Feel free to reach out to us directly for further assistance. We're here to help!
Prey automatically generates Missing reports when a device is flagged as missing, offering critical evidence like location, user photos, activity screenshots, and network connection records. This objective data is crucial for audits and disciplinary actions. For regulations requiring devices in specific locations, Location history provides a timestamped record of movement, proving compliance within geofenced areas and offering objective evidence for auditors.
Prey helps enforce a wide range of policies, including device-in-use policies (who is using a device), location-based policies (where a device can be used), and device loaner return policies (ensuring these are returned on time). The automated features save you from having to manually enforce these rules.
Prey gives you the tools to maintain a comprehensive audit trail and enforce policies that are essential for regulatory compliance. Prey’s always-on location tracking and security features help you generate data to provide irrefutable evidence that your devices and users are adhering to industry regulations, helping you pass audits and mitigate risk.
Prey provides the objective, verifiable data that auditors require. By using features like our Audit log and Location history, you can easily generate and export reports showing a complete record of device activity, user actions, and device locations, proving your adherence to compliance policies and procedures.
By default, the plan includes 30 days of location history data. However, for organizations with stricter compliance requirements, we offer an add-on extension to store location data for 3, 6, or 12 months.
Our platform keeps an unalterable record of all system interactions. This includes: when devices were added or removed, users logged-in and out, specific actions (like a remote wipe), and who performed them, triggered security reports, feature use information, and much more. This provides a clear, defensible record of your compliance actions.
Yes. Regulations like HIPAA and GDPR require that you have controls in place to protect sensitive data. Prey's remote security actions, like Remote wipe and Encryption, give you the ability to instantly protect data on a compromised device, mitigating the risk of a breach and demonstrating your commitment to data security standards.
Prey is designed to provide the essential, high-impact features for compliance without the complexity and cost of a full enterprise platform. We focus on providing the core tools for accountability, policy enforcement, and audit readiness, making us a simple and effective solution for organizations that need to mitigate risk with a scalable tool.
Prey automatically generates Missing reports when a device is flagged as missing, offering critical evidence like location, user photos, activity screenshots, and network connection records. This objective data is crucial for audits and disciplinary actions. For regulations requiring devices in specific locations, Location history provides a timestamped record of movement, proving compliance within geofenced areas and offering objective evidence for auditors.