Location-based security response
Protect devices with automated location security
You can't be everywhere at once. Prey's location-based security gives you an extra layer of protection, ensuring devices stay where they belong and alerting you the moment they don't.

The risk of unmonitored mobility
Misuse of loaner devices
Devices assigned for specific locations, like a classroom or warehouse, could be taken off-site without permission, leading to potential loss or theft.
Compliance violations
For industries with strict data handling regulations, the inability to keep devices within a secured work area can lead to severe penalties and reputational damage.
Delayed incident response
Without ongoing, location-based alerts, a security incident can go unnoticed for hours or even days, dramatically increasing the risk of a data breach.
Lack of accountability
It's difficult to track who has which device and where it is, making it impossible to hold users accountable for device location and security protocols.
The Prey solution:
Proactive, location-based security
See your security goals in action
Prey transforms location data into a robust security tool. It offers a comprehensive map view of all your devices and their assigned Geofences, and provides immediate alerts for automated actions. This clear and actionable overview empowers you to manage your security status effectively, regardless of your devices' locations.
Explore more
Keep remote devices visible and secure. Learn why device tracking matters for remote teams, how it supports compliance, and how Prey helps protect endpoints anywhere.
Discover Prey’s 4-layer security approach: device tracking, remote protection, asset management, and dark web breach monitoring, all in one platform.
Frequently asked questions
Below, you'll find answers to commonly asked questions about our products/services. Feel free to reach out to us directly for further assistance. We're here to help!
A geofence is a boundary you draw on a map around a specific location, like your office, a classroom, or a construction site. When a Prey-protected device enters or exits your selected perimeter, it can trigger an automated action, giving you an extra layer of security without needing constant manual monitoring.
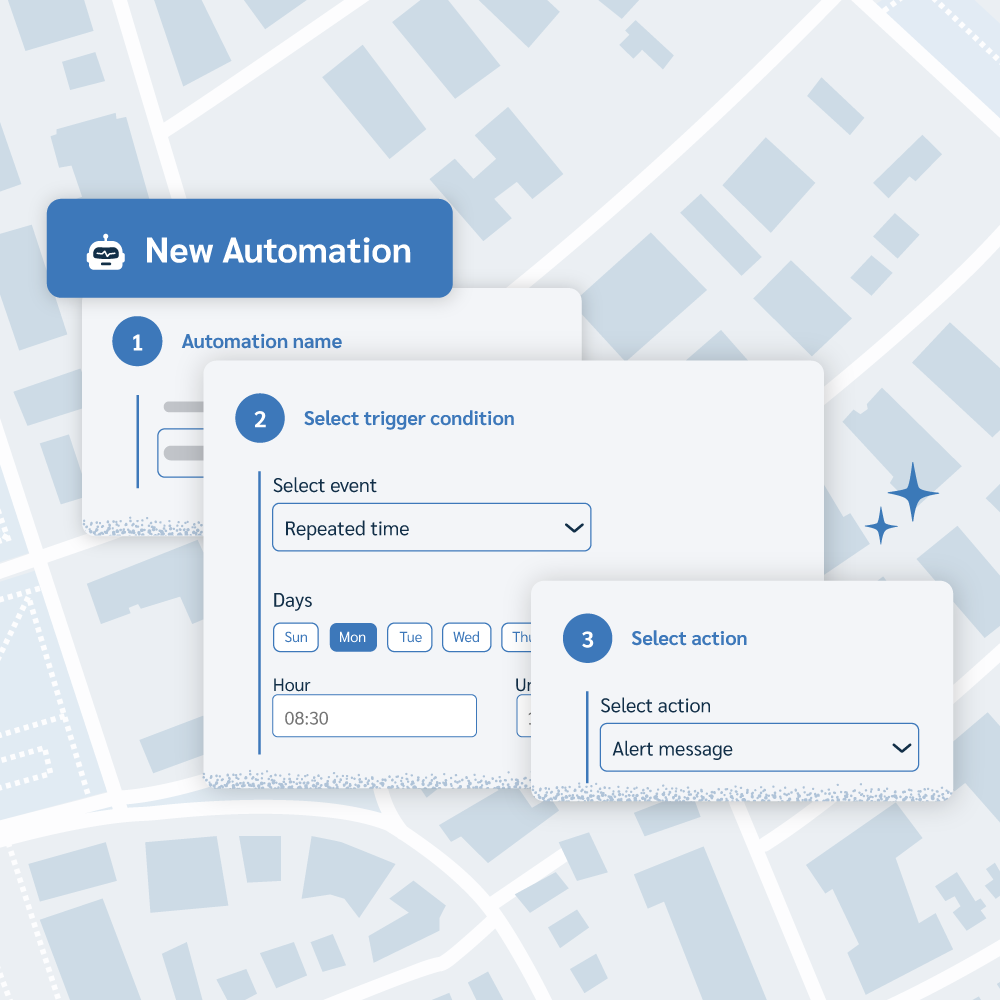
You can set up a variety of automated security responses. For example, you can configure a device to lock and unlock its screen automatically, trigger a loud alarm, or flag as missing to generate ongoing Missing reports the moment it leaves a safe zone. Your security protocols are enforced even when you're not watching.
Geofences are perfect for managing devices that are meant to stay in or out of a specific location. You can create a geofence around a singular work site, or entire countries, your choice. If a device is taken outside your trusted parameter, you can set up notifications and automate security actions, protecting your valuables. You might also use geofences to delimit out-of-bounds areas, so when specific devices enter you get notifications and react accordingly.
When Prey detects that a device has crossed a geofence boundary, you can sign up to receive instant email alerts. This allows you to respond immediately and take control, knowing exactly when and where machines are located.
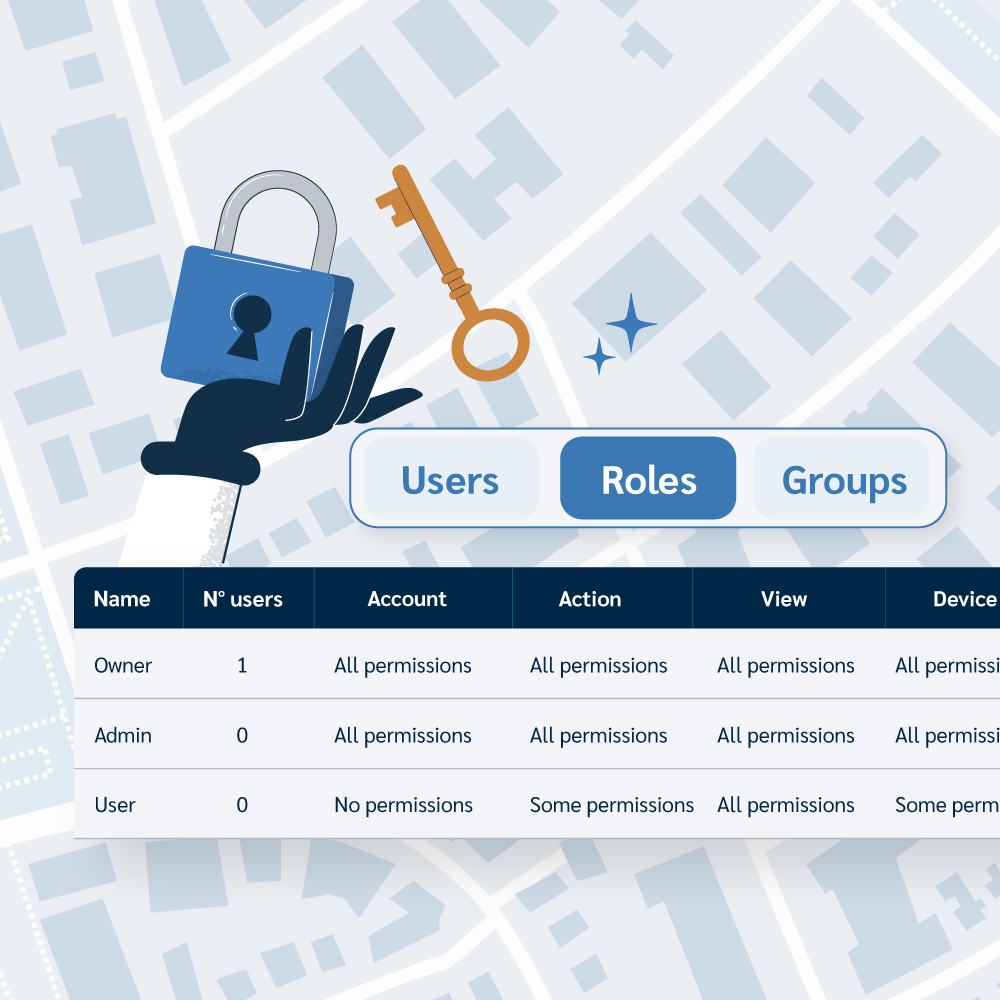
Yes, you can automate actions on selected devices and assign them to specific geofences. Additionally, you can define loan parameters when assigning devices to users, allowing you to tailor your security response to your unique requirements.
While location tracking shows you where a device is, geofencing provides proactive, automated security. Instead of manually checking a map, you can set up a rule once and trust that Prey will notify you and take action the moment a security event occurs, allowing you to prevent a breach before it escalates.