1:1 device program management
Remote and automated management for 1:1 programs
Prey streamlines device distribution, reinforces accountability, and automates device recovery, freeing up valuable IT team hours. This ensures students consistently have access to the devices they need.

The challenges of managing student and faculty devices
Device loan chaos
Without an automated and dedicated system, tracking who has which device and its current status becomes an impossible task. This leads to inaccurate records and wasted staff time.
Unreturned or stolen laptops
Devices for loan programs are frequently lost, stolen, or simply not returned on time, draining resources for departments and preventing them from providing resources to other students.
Device returns pile up
Manual check-ins create a backlog. Returned devices need condition checks, inventory updates, and data wipes before redeployment. Devices that sit idle make students wait, and your team scramble.
No proof, no accountability
Holding students and faculty accountable for devices is difficult without data. Unmatched records lead to disputes over returned devices. Device management becomes conflict resolution.
The Prey solution:
Time-saving device management for schools
A command center for school devices
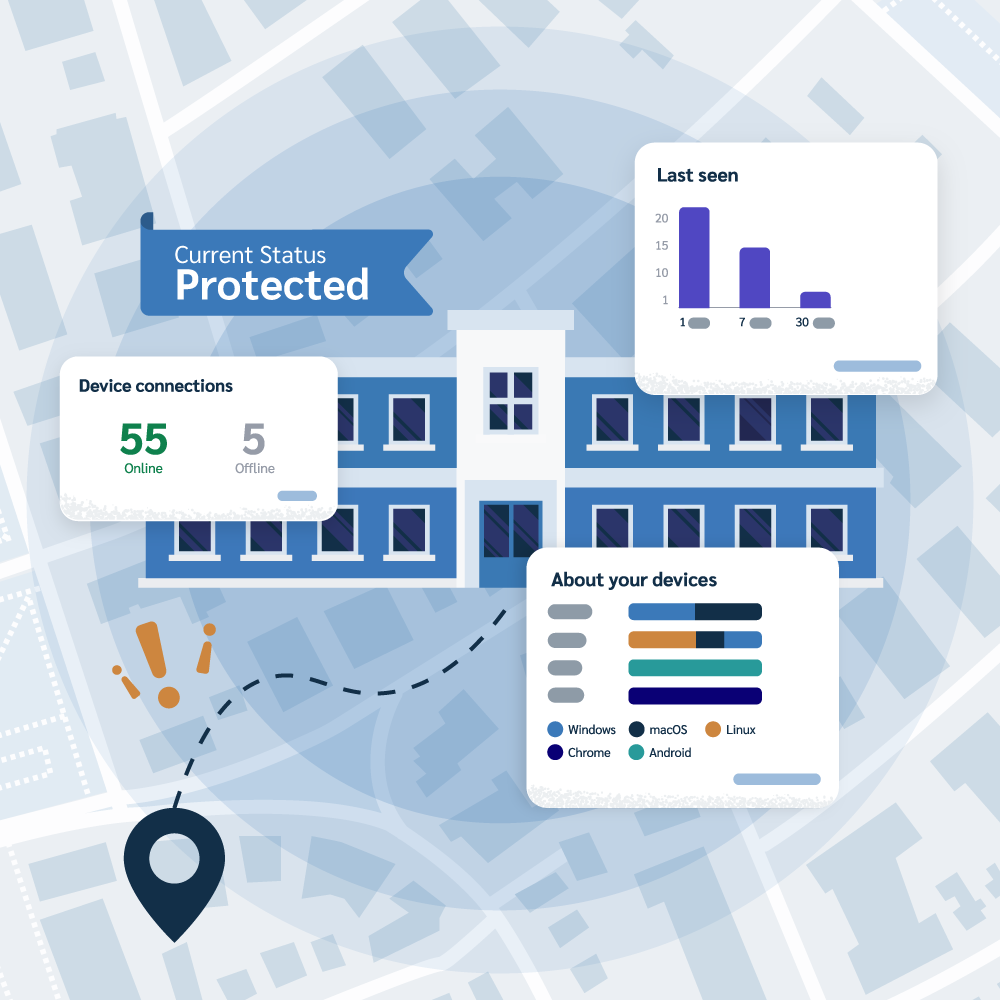
Prey is a proactive security assistant, tracking and reacting to potential threats. Our panel offers an overview of loaned devices, including assigned users, loan status, and last known locations, streamlining your operations and ensuring smooth organizational fleet management. See for yourself!
Explore more

Learn how Rock Valley College revolutionized device management: From losing laptops to achieving 95% recovery rates with Prey's tracking solution

Stop back-to-school 1:1 device chaos: audit, automate & secure every K-12 laptop with Prey
Frequently asked questions
Below, you'll find answers to commonly asked questions about our products/services. Feel free to reach out to us directly for further assistance. We're here to help!
Our Loan Manager feature is a dedicated tool for tracking devices assigned to a specific student, faculty, or company member. You can easily see who has which device, when it was loaned out, and its status, all from one centralized panel. This replaces manual spreadsheets and gives you a single source of truth for your entire loaner program.
Yes. Our Labels and Groups features allow you to easily organize your devices in any way that works for your school. You can create groups for specific grades (e.g., "7th Grade Laptops"), classrooms, or departments (e.g., "Library Laptops"), which makes inventory audits and day-to-day management a breeze. The same goes for companies lending devices to associates from different teams and offices.
Yes. Our Labels and Groups features allow you to easily organize your devices in any way that works for your school. You can create groups for specific grades (e.g., "7th Grade Laptops"), classrooms, or departments (e.g., "Library Laptops"), which makes inventory audits and day-to-day management a breeze. The same goes for companies lending devices to associates from different teams and offices.
When a device is returned, you can quickly locate its record in the Prey dashboard to verify its status. Our system provides a clear record of its movements and a full inventory of its hardware. This simplifies the intake process and helps your team get the device ready for the next loan quickly and accurately.
Absolutely. Location tracking is critical even on campus. You can use it to pinpoint a misplaced device in a specific building or room. A remote alarm is great for locating a device stored in forgotten locations. You can also set up Geofences around the campus to get an alert if a device is taken off-site without permission, providing an extra layer of security and accountability.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Yes. Prey is a flexible solution that can be used to manage devices for your entire institution. You can use Labels and Groups to separate your student loaner devices from those assigned to staff, ensuring that each group is managed with its own set of security rules.