Ransomware as a Service (RaaS) marks a significant evolution in cybercrime. These cybercriminal collectives have adopted subscription-based models akin to legitimate software-as-a-service platforms. RaaS operators have transformed ransomware from a complex undertaking reserved for elite hackers into a plug-and-play process just about anyone can use.
The outcome is an accessible criminal ecosystem that enables countless low-skill actors and gangs to commit complex ransomware attacks at scale. In 2025, the surge of RaaS-driven campaigns has both increased the sheer volume of attacks and amplified their sophistication and destructiveness, placing organizations of all sizes on constant alert.
The Wave of 2025 ransomware attacks
The first few months of 2025 have underscored just how dramatically ransomware has proliferated. In January alone, a leading cybersecurity observatory documented a 149% increase in ransomware incidents year-over-year across the United States, with nearly 1,200 distinct cases reported in just five weeks, a pace unseen in prior years. This dramatic spike aligns closely with the mainstreaming of RaaS platforms, with ransomware makes up 28% of malware incidents.
These incidents came to the fore in Spring 2025, when a wave of cyberattacks hit a series of high-profile targets and household name brands. Major retail chains and market leaders were hit by a series of critical cyberattacks that crippled supply chains and left shelves empty for months. It’s believed that most of these attacks have been fuelled by the DragonForce RaaS platform.
The RaaS model has expanded ransomware’s scope. Critical public services have increasingly become targets, particularly when it comes to state and local level infrastructures. Healthcare providers have likewise reported spikes in attack volumes, with patient-care systems encrypted across multiple sites, forcing costly manual overrides.
How RaaS is fuelling cyberattacks
RaaS has democratized the ability to launch attacks by removing technical barriers. Where once aspiring cybercriminals required deep expertise in cryptography, payload development, and command-and-control infrastructure, now all they need is a subscription, a basic workstation, and access to the hardened RaaS dashboard. Toolkits frequently include real-time dashboards, automated phishing campaign builders, and even AI-assisted vulnerability scanners, enabling affiliates to craft and deploy campaigns with minimal technical proficiency.
This shift has escalated not just the number of attacks but their quality. RaaS developers invest heavily in evasion techniques, like rotating encryption keys, employing polymorphic code, and incorporating AI-driven anti-analysis routines to outpace security vendors. Affiliates can then launch multifaceted, stealthy campaigns that bypass legacy defenses.
Perhaps most worrying is the integration of generative AI into RaaS ecosystems. Some operators now provide AI-powered phishing frameworks that auto-generate hyper-realistic social engineering based on social media profiles, or constantly scan corporate networks for weak points. Attackers are even looking to exploit cloud-based foundational models to autonomously discover and exploit vulnerabilities post-breach.
These developments suggest that 2025 may be remembered as the year ransomware truly went industrial.
How RaaS operates and coordinates with cybercriminals
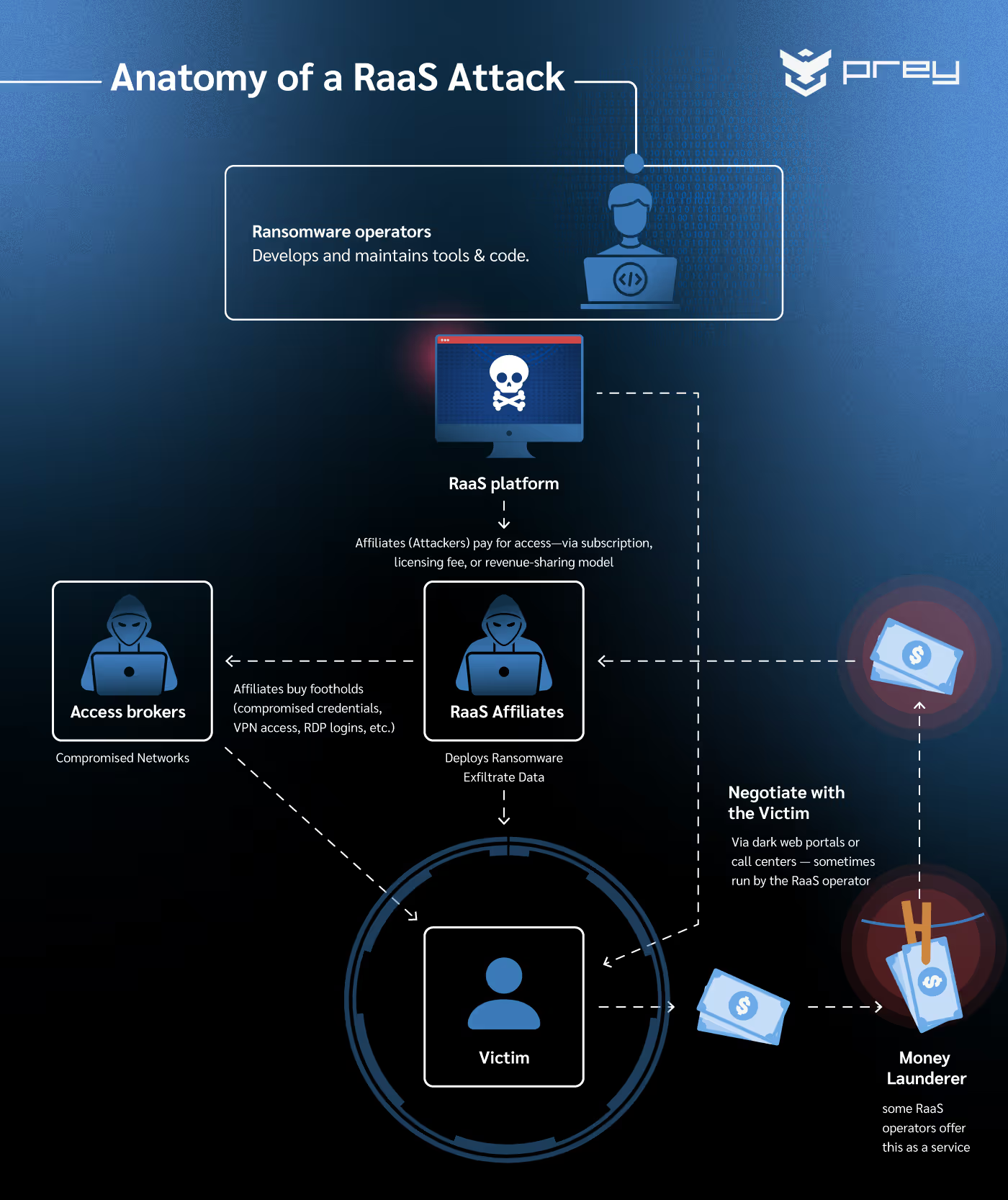
RaaS mirrors legitimate SaaS in every respect except purpose. At its core sits a small cadre of skilled developers who architect, refine, and maintain the ransomware codebase. These ‘product’ teams handle feature development, implementing encryption improvements, obfuscation layers, and secure payment portals, while affiliates serve as the ‘salesforce’, executing attacks and managing victim communications.
Registration on a RaaS platform often resembles signing up for a corporate service. Prospective affiliates visit darkweb marketplaces where operators advertise tiered subscription levels, paid using cryptocurrencies like Bitcoin: basic plans allow limited concurrent deployments, while premium tiers unlock advanced evasion modules, priority customer support, and extended negotiation toolkits.
Fees vary: some charge flat monthly rates, others require significant upfront licensing fees, and many adopt revenue-sharing models where affiliates remit 20%–40% of each successful ransom payout. DragonForce (the RaaS fueling many high profile attacks in 2025), for instance, is popular due to its particularly low profit share requirements.
Once onboarded, affiliates access a web-based control panel offering modules for building custom payloads, tracking deployment statistics, and initiating automated phishing lures. Some RaaS operations even maintain victim negotiation ‘call centers’ staffed with negotiators who specialize in maximizing payment amounts while preserving the integrity of cryptocurrency transactions. In more extreme cases, operators liaise with known money-laundering networks to ‘clean’ proceeds before distribution.
The ecosystem also relies on specialized service providers. Access brokers infiltrate corporate networks, often selling footholds for a few thousand dollars, while social engineers craft bespoke phishing kits targeting executive staff. After initial access, affiliates can pivot to the RaaS dashboard, launch encryption modules, and exfiltrate sensitive data under the double-extortion model: files are copied before encryption, then threatened with publication on dark web leak sites if ransoms go unpaid. Triple-extortion variants add layers such as DDoS attacks on customer-facing services or threats to notify regulatory and media outlets, intensifying pressure on victims.
This division of labor has fostered fierce competition among RaaS providers. Rivalries between groups (like DragonForce vs. RansomHub), drive rapid innovation in malware payloads and delivery techniques. Some operators have even compromised competitor affiliates, injecting backdoors into rival malware to siphon off ransoms before integration.
Defending against RaaS
Confronting RaaS demands more than traditional perimeter defenses; it requires a holistic, multi-layered strategy.
Patch management
First, rigorous patch management is non-negotiable. Automated patch deployment, prioritized by threat intelligence feeds, can close the window of exposure to known exploits. In 2025, 32% of cyberattacks start with an unpatched vulnerability, underscoring the criticality of timely updates.
Access control and Zero Trust
Access control is the next pillar. Multifactor authentication (MFA) must be enforced universally, especially on privileged accounts and remote access points. Organizations are adopting ****Zero Trust frameworks, segmenting networks into micro-perimeters to constrain lateral movement. Strong password hygiene, periodic credential audits, and deprecation of legacy protocols further shrink the attack surface.
Backup your data
Equally important are data backup strategies. Immutable, air-gapped backups, verified through routine restore drills, offer a secure recovery path without yielding to ransom demands. Advanced RaaS operators have begun targeting cloud backups, so you must audit your backup configurations to ensure redundancy and isolation from production environments.
Extended detection and response
Extended Detection and Response (XDR) platforms provide unified visibility across endpoints, networks, and cloud workloads. Combined with EDR and Network Detection and Response (NDR) tools, organizations can identify anomalous behaviors, such as mass file encryption or unusual outbound data flows, in near real time. Proactive threat-hunting teams can then investigate and disrupt nascent campaigns before encryption triggers.
Incident response plans
A robust incident response (IR) plan is indispensable. This living document should define roles, communication protocols (including backup channels if primary systems are compromised), and escalation paths. Your regular tabletop exercises test the playbook, revealing operational blind spots and improving coordination between your IT, legal, PR, and executive leadership.
Managed security and cyber insurance
Given the complexity of defending against RaaS, many companies turn to managed security service providers (MSSPs) and cyber insurance policies. However, insurers increasingly mandate proof of strong cybersecurity postures as prerequisites for coverage. Organizations failing to demonstrate these controls face higher premiums or outright denials.
Human defenses
Since ransomware often begins with social engineering, employee awareness programs are essential. Quarterly phishing simulations, interactive training modules, and real-time reporting channels help cultivate a vigilant workforce. Training should cover emergent threats, like voice-based scams, AI-generated lures, and deepfake-assisted deception, to keep pace with attackers’ increasing sophistication.
Lastly, cybersecurity must be viewed as a collective endeavor. Sharing threat intelligence through Information Sharing and Analysis Centers (ISACs), regulatory bodies, and direct law enforcement partnerships accelerates detection of emerging threats. Advocacy for stronger data-protection regulations and public-private collaboration can also yield more resilient national infrastructures, making it harder for RaaS operators to find low-hanging fruit.
Conclusion
The advent of Ransomware as a Service has irrevocably transformed the threat landscape. Adopting SaaS-style delivery models has industrialized ransomware, enabling quick deployment, sophisticated obfuscation, and relentless innovation. No longer the province of black-hat specialists, ransomware is now a mass-market tool that leverages AI-driven lures, double and triple extortion tactics, and professionalized affiliate support services.
Organizations can’t be complacent. Traditional, reactive defenses, relying solely on antivirus updates or occasional firewall rule tweaks, are no longer sufficient. Instead, you need to embrace a philosophy of cyber resilience: assuming that breaches will occur and preparing contingencies to limit damage. This shift demands continuous improvement, regular testing, and cross-disciplinary collaboration.






