The educational sector is facing a surge in cyber threats, with a notable concern being school phishing and ransomware. There were over 1,600 cyber incidents targeting public K-12 schools between 2016 and 2022, with more than 50 publicly disclosed ransomware attacks reported per year. Most recently, an attack on a New Haven school stands as a glaring testament to the vulnerability of schools: cyber criminals siphoned off $6 million from the district, exploiting the email exchanges between the COO, the city’s budget office, and vendors, ultimately impersonating the COO for six separate fraudulent transfers.
The Federal Trade Commission plays a crucial role in reporting and combating phishing scams targeting schools.
Ransomware and phishing are serious issues confronting schools and school system administrators, as well as their IT departments.
The increase in school phishing attacks
Phishing attacks against schools are on the rise—and the numbers prove it.
According to IBM's 2023 X-Force Threat Intelligence Index, the education sector was the most targeted industry for cyberattacks in 2022, with phishing being the most common initial access vector. These attacks often serve as the entry point for more damaging threats like ransomware.
A report by Cybersecurity and Infrastructure Security Agency (CISA) further notes that 90% of successful cyberattacks in schools begin with a phishing email, often sent to unsuspecting teachers or administrative staff.
Even more alarming, the K12 SIX 2023 Annual Report found that:
- Phishing accounted for over 60% of all reported cybersecurity incidents in K-12 schools.
- Districts with fewer than 2,500 students were twice as likely to fall victim to email-based attacks compared to larger districts.
- Attackers are increasingly spoofing trusted platforms like Google Classroom or Microsoft Teams to trick staff and students.
Trends and implications
The rise in phishing attacks correlates with several broader trends:
- Increased digital dependency: As schools continue to integrate technology into every aspect of administration and learning, the potential points of vulnerability multiply. This digital expansion provides fertile ground for cybercriminals.
- Remote learning environments: The shift towards remote and hybrid learning models has expanded the attack surface dramatically. Home networks typically lack the robust security measures found in institutional settings, making them easier targets for phishing exploits.
- Phishing scams often target users on social media platforms, streaming services, and subscription services. These scams can impersonate well-known companies to deceive users into providing sensitive information.
- Low awareness levels: Often, the success of a phishing attack hinges on the level of cybersecurity awareness among staff and students. Unfortunately, regular and comprehensive training is not always a priority in educational settings, leading to a higher rate of successful attacks.
Most common types of school phishing attacks
Schools face an array of cyber threats. IT administrators must remain vigilant, understanding that cybercriminals are always devising new strategies to infiltrate systems.
- Email phishing: Email phishing is a deceitful tactic where cybercriminals send emails masquerading as trustworthy entities to extract personal information. These malicious emails often contain links or downloads that, once clicked, can infect systems or steal data. It is crucial for students to contact legitimate loan servicers for assistance with student loans to avoid scams.
- Spear phishing, or targeted email phishing: Spear phishing takes regular phishing up a notch. Here, the attacker carefully curates an email to target specific individuals or organizations. By personalizing the attack, the success rate becomes significantly higher, making it extremely dangerous.
- Whaling, or targeted emails impersonating a senior player at an organization: Whaling is a sophisticated form of spear phishing that zeroes in on top-tier executives. The previously mentioned New Haven crisis is an archetypal example where cybercriminals impersonated a senior executive, resulting in massive financial losses, and like this one, there are multiple examples of successful whaling attacks in schools.
- ”Vishing” or phone call phishing: Vishing is the telephonic counterpart of email phishing, where scammers pose as legitimate entities over the phone. Now, with AI-trained voices, cybercriminals are creating more convincing and deceptive calls, raising the stakes even higher.
- ”Smishing” or phishing by SMS text: Smishing employs text messages to deceive recipients. Cybercriminals send texts prompting recipients to click links or call numbers, leading to potential data theft or system compromise.
School phishing attacks on districts

A phishing attack involves tricking the recipient of an email to download malware, visit a fraudulent website or open a file containing malware. Spear phishing, a variant on the attack method, personalizes the attack, making it seem as if an email is coming from a friend or colleague. Both have the same effect.
School districts are vulnerable to phishing attacks. One reason is that employees may have low levels of awareness of school phishing dangers. Also, district employees may not find it strange to get a PDF or Word document sent by an unknown person. "It could be from a parent of a student," they might think, so they open the document and then…problems. Phishing attacks can also have the victims filling out forms on fraudulent websites that lead to invoices and payments to entities that look legitimate but are, in fact, criminal enterprises.
Keith R. Krueger, chief executive of the Consortium for School Networking, a group that represents school technology employees, described the phishing risk exposure in the New York Times by noting, “Cyberattacks on school districts and other organizations begin when an employee — perhaps someone in the financial office, where a lot of sensitive information is stored — opens an email that appears to have come from a supervisor or even the district superintendent, but in fact carries malware that compromises the employee’s computer and the district’s network.”
Recent examples of school phishing attacks against educational institutions include:
- Spotsylvania Schools – the phishing attackers posed as contractors to the district and were able to defraud Spotsylvania, Virginia schools of over $600,000. Law enforcement has been able to recover about half the money.
- Lancaster University – this college experienced a data breach that began with a phishing attack. Attackers accessed college application data and sent fraudulent invoices to applicants.
The Impact of a successful phishing attack
A successful phishing attack can have devastating consequences for schools and educational institutions. The impact can be far-reaching, affecting not only the institution itself but also its students, staff, and the wider community.
Best practices to combat school phishing
Educational institutions house a wealth of sensitive data, making them prime targets for cybercriminals. To ensure the safety of this data and the uninterrupted functioning of the education process, it’s essential to establish comprehensive cybersecurity best practices.
Additionally, borrowers should be cautious when managing their federal student loans, ensuring they work with legitimate loan servicers and avoid fraudulent services that claim to offer assistance for a fee.
From ensuring robust email protection to creating backup protocols, schools need to adopt a 360-degree approach, addressing every vulnerability and fortifying every potential breach point. Recognizing and addressing cybersecurity threats for IT professionals in education is pivotal to safeguarding these valuable assets.
1. Deploy multiple-layered security controls defense

A multiple-layered security approach involves implementing several protective layers to deter potential breaches. Like a fortress with walls, moats, and guards, a digital system protected through a layered approach ensures that even if one line of defense is penetrated, others remain intact to provide ongoing protection. This strategy is highly effective as it ensures that systems are not overly reliant on a single security measure. The core idea is to create redundancy in security defenses, making it more challenging for an attacker to breach the system.
This approach implements multiple security measures at various levels:
- Network segmentation and monitoring: By splitting the network into distinct segments, schools can ensure that a breach in one segment doesn't compromise the entire system.
- Identity and access security: It's crucial to ensure that only authorized individuals can access specific parts of the network and sensitive data. By implementing role-based access controls, institutions can define who can view or modify particular resources.
- Endpoint security and advanced protection: Tools that provide advanced endpoint detection can monitor these devices in real-time, identifying and countering any malicious activities.
- Email security: Proper email security measures include advanced spam filters, malware scanners, and phishing detectors.
- Web security: With vast amounts of educational resources now online, ensuring web security is essential. This means having active firewalls in place and filters that prevent users from accessing harmful online content or malicious websites.
- Data security and backups: Regular data backups, stored both onsite and offsite, ensure that institutions can quickly recover critical information.
2. Establish clear policies and procedures

Clear and robust policies and procedures lie at the heart of any solid cybersecurity framework. They serve as the guiding blueprint, detailing how staff and students should interact with institutional systems and data. From detailing response plans in the event of a cyber incident to defining acceptable IT behaviors, these policies and procedures ensure that all users are aligned in their approach to cybersecurity.
3. Develop and implement a cyber incident response plan
A cyber incident response plan outlines actions to take in the face of a cybersecurity breach. The National Institute of Standards and Technology incident response life cycle involves four phases: Preparation, Detection and Analysis, Containment, Eradication, and Recovery, and Post-Event Activity.
Each phase is designed to mitigate the impact of an incident and facilitate a swift return to normalcy: Preparation readies teams with resources and directives; Detection and Analysis swiftly identify and assess threats; Containment, Eradication, and Recovery isolate, remove, and restore systems; and Post-Event Activity involves analysis and improvement for enhanced future defenses. If you want to know more about incident response planning, you can read it in our dedicated section here.
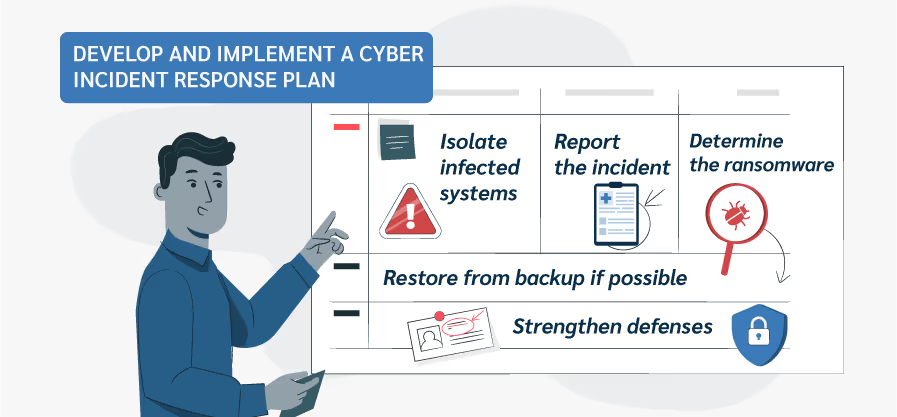
Having a clear procedure in place ensures optimal reaction. Here’s an example of a ransomware response procedure:
- Isolate infected systems
- Report the incident
- Determine the ransomware type
- Restore from backup if possible
- Strengthen defenses:
4. Create IT security policies for staff

IT and security policies for staff provide guidelines on acceptable behavior, device usage, and data handling. Password Policies mandate strong, unique passwords to reduce unauthorized access risks, often requiring regular password changes and prohibiting easily guessable passwords.
Acceptable Use policies outline permitted activities on company devices and networks, preventing misuse for personal tasks or accessing harmful websites. You can learn more about security policies for schools in our dedicated section here.
5. Implement ongoing monitoring and security testing procedures

Effective cybersecurity isn't just about the defenses in place but also about the vigilance to detect and respond to threats. Schools must embrace monitoring and testing as proactive measures to keep their digital environment safe. By regularly overseeing system activities and subjecting those systems to real-world simulated threats, institutions can unearth vulnerabilities, enhance security protocols, and ensure preparedness against evolving cyber threats.
- Log monitoring and analysis: Regularly monitoring and analyzing these logs allow IT professionals to understand patterns, detect inconsistencies, and respond to threats in real-time.
- Backup testing: By testing backups, schools can identify potential issues, like data corruption or incomplete backups, and take corrective measures before an actual disaster strikes.
- Simulation exercises: Simulation exercises, like mock phishing campaigns or controlled ransomware attacks, are helpful to test the team's response time, effectiveness, and coordination.
- Continuous threat hunting: This involves proactively seeking signs of malicious activity within a system rather than waiting for automated alerts.
6. Train your staff

The human element is often the weakest link in cybersecurity. Staff, unless informed and updated, can inadvertently expose systems to risks. Regular cybersecurity training sessions help bridge this knowledge gap. These sessions, encompassing workshops, webinars, and seminars, equip staff with knowledge about the latest threats, safe online practices, and response strategies. Such ongoing education fosters a culture of cyber-awareness, transforming staff from potential vulnerability points into active defenders.
Teach the importance of identifying school phishing attempts
Phishing is a major cyber threat, and detecting it is crucial. Despite its apparent simplicity, school phishing attacks are growing more sophisticated. It is also important to recognize warning signs of fraudulent messages related to student loan forgiveness, as scammers often falsely promise immediate debt relief. Here are signs to help distinguish genuine communication from phishing attempts:
- Suspicious attachments: Hackers often send unexpected emails with harmful attachments. Treat such attachments with caution. They can install malware or lead to harmful sites.
- Unusual requests, especially financial: Phishers mimic trusted sources to ask for money or sensitive data. Be cautious of unusual, urgent, or secretive requests. Verify through another channel before responding.
- Check links: Hover over links to see the real URL. Mismatched URLs or slight misspellings indicate phishing.
- Sensitive information requests: Legitimate entities won’t ask for passwords or PINs via email. Treat such emails with suspicion.
Provide information about safe online practices to follow
Online security is a mix of tools, defenses, and user habits. Practicing good digital hygiene can significantly bolster your safety. Here's a concise list of risky online behaviors to avoid:
- Weak passwords: Sharing passwords jeopardizes data and opens doors to broader breaches. Using one password across multiple accounts is risky.
- Public Wi-Fi risks: Avoid sensitive tasks on public Wi-Fi due to its insecurity. Use a VPN for encryption.
- Unverified software: Download from trusted sources. Check reviews and certifications, and stick to official app stores.
Suspect email attachments: Beware of email attachments, even from contacts. Scan with antivirus software before opening.
Bonus: additional measures

To fortify their digital infrastructure, educational institutions must go beyond traditional security protocols. Advanced measures tailored to the unique needs and challenges of the educational sector can provide an extra layer of protection.
Cyber insurance
Just as we insure our cars and homes, we need to think about insuring our digital presence, too. Enter Cyber Insurance. It's a specialized insurance coverage designed to safeguard businesses against the financial repercussions of cyber threats and attacks, like the damages caused by ransomware or DDoS attacks. Whether it's a sophisticated hack or a misplaced laptop, cyber insurance can be a financial lifesaver.
External security audits
Imagine going for a routine health check-up but for your organization's cybersecurity system. That's essentially what an external security audit is. External experts dive deep into your systems, identifying vulnerabilities and weak points. These audits provide an unbiased review of the organization's security posture, ensuring that all aspects are up to par.
Limiting third-party access
While collaboration and integration are the backbones of many successful businesses, there's a hidden risk that often goes unnoticed: third-party access. By giving third-party apps or vendors extensive or unprotected access to organizational systems, you're opening doors to potential security threats.
These are some of the most recent examples of third-party data breaches:
- U.S. School Districts: Illuminate Education breach exposed data in major school districts like NYC and Los Angeles. Chicago Public Schools saw 495,000 student records exposed through an attack on a third-party provider.
- Microsoft: HAFNIUM attacks compromised on-premises Microsoft Exchange Servers of 30,000 global organizations. A subsequent breach exposed 38 million records through a vulnerability in Microsoft Power Apps.
- Uber: A third-party breach compromised the email addresses and data of over 77,000 Uber employees. A similar breach targeted DoorDash via a connected vendor's stolen credentials.
Asset inventory for risk assessments
At the heart of robust cybersecurity lies an intimate understanding of what you're protecting. Asset inventory is a thorough accounting of all organizational assets, be they physical or digital. Once you know what's at stake, risk assessments step in, analyzing the likelihood of threats to these assets and the potential damage they can cause. Together, these tools give organizations a clear roadmap of where their defenses need to be strongest.
These are the main benefits of implementing asset inventory tools:
- Full visibility of devices for security operations
- Mitigating shadow IT
- Enhancing incident response
- Resource allocation and budgeting
- Meeting compliance requirements

Takeaways
School phishing and ransomware threats are serious and will likely continue until they are stopped by stronger security countermeasures. There is a lot at stake! Student and family privacy is at risk. Schools cannot fulfill their educational missions and state-mandated requirements if their systems are locked up.
Defense is possible, however. With a focus on cybersecurity basics, an advisory from experienced third parties, and perhaps reliance on MSSPs, schools, and school districts can reduce their exposure to ransomware and phishing risks.






