Key Takeaways
- EDR (Endpoint Detection and Response) is a cybersecurity solution that continuously monitors endpoints like laptops, desktops, servers, and mobile devices to detect and respond to threats in real-time
- EDR goes beyond traditional antivirus by using behavioral analytics and machine learning to identify unknown threats and advanced persistent threats
- Core EDR capabilities include threat hunting, automated response, forensic investigation, and ransomware rollback features
- EDR works through a continuous cycle of data collection, threat detection, containment, investigation, and remediation
- Organizations need EDR because up to 90% of cyberattacks start at endpoint devices, and traditional security tools struggle with sophisticated threats
- EDR integrates with other security solutions like SIEM, SOAR, and XDR to create comprehensive defense strategies
In today’s rapidly evolving cybersecurity landscape, traditional antivirus solutions simply aren’t enough to protect against sophisticated threats. With up to 90% of cyberattacks starting at endpoint devices, organizations need more advanced protection that can detect, investigate, and respond to threats in real-time. This is where Endpoint Detection and Response (EDR) comes into play—a game-changing technology that’s reshaping how security teams defend against modern cyber threats.
EDR represents a fundamental shift from reactive to proactive endpoint security, combining continuous monitoring with intelligent analytics to identify threats that would otherwise slip past conventional defenses. Whether you’re an IT professional evaluating security solutions or a business leader trying to understand your organization’s cybersecurity needs, this comprehensive guide will help you understand what EDR is, how it works, and why it’s become essential for modern endpoint protection.
What is EDR? Definition and Overview
Endpoint Detection and Response (EDR) is an advanced cybersecurity technology that provides real-time and continuous monitoring, detection, investigation, and automated response to threats targeting endpoint devices. Unlike traditional antivirus software that relies primarily on signature-based detection, EDR solutions use behavioral analytics, machine learning, and threat intelligence to identify both known threats and emerging threats that have never been seen before.
Endpoints in this context include any device that connects to your network: laptops, desktops, mobile phones, servers, IoT devices, and virtual machines. These devices serve as both the first and last line of defense against cyber attacks, making them critical points of focus for any comprehensive security strategy.
The concept of endpoint detection and response was first defined by Gartner analyst Anton Chuvakin in 2013, emerging as a response to the limitations of traditional antivirus solutions in addressing new and more sophisticated attack methods. While antivirus software excels at blocking known malware signatures, it struggles with fileless attacks, zero-day exploits, and advanced persistent threats that use legitimate system tools and processes to hide their malicious activities.
EDR fills this gap by focusing on what attackers actually do rather than what they look like. Instead of just scanning files for malicious code, EDR systems monitor endpoint behavior patterns, analyze network connections, track process activities, and correlate events across multiple endpoints to detect suspicious system behavior that indicates a potential security incident.
Why Organizations Need EDR Solutions
The cybersecurity landscape has fundamentally changed over the past decade, and the statistics paint a clear picture of why traditional security approaches are no longer sufficient. Research shows that up to 90% of cyberattacks and 70% of data breaches now start at endpoint devices, making them the primary battleground in the fight against cyber threats.
Traditional antivirus solutions face significant limitations when dealing with modern attack techniques. Cybercriminals have evolved beyond simple malware distribution, now employing sophisticated methods like fileless attacks that operate entirely in memory, social engineering tactics that exploit human psychology rather than technical vulnerabilities, and zero-day exploits that target previously unknown software flaws.
These advanced threats often use legitimate system tools and processes to carry out malicious activities, making them nearly invisible to signature-based detection methods. An attacker might use PowerShell scripts to move laterally through a network, leverage Windows Management Instrumentation (WMI) for persistence, or exploit trusted applications to execute malicious payloads—all while appearing as normal system activity to traditional security tools.
The shift to remote and hybrid work environments has further expanded the attack surface that organizations must defend. Employees working from home, using personal devices, and connecting through unsecured networks create new vulnerabilities that perimeter-based security solutions cannot adequately address. EDR solutions provide the visibility and control needed to secure these distributed endpoints regardless of their location.
Additionally, the rapid proliferation of cloud workloads and unmanaged devices in corporate environments creates blind spots that attackers can exploit. EDR security solutions help organizations discover shadow IT assets, assess vulnerabilities across their entire endpoint ecosystem, and maintain comprehensive endpoint security even as their infrastructure evolves.
How EDR Works: The Detection and Response Process
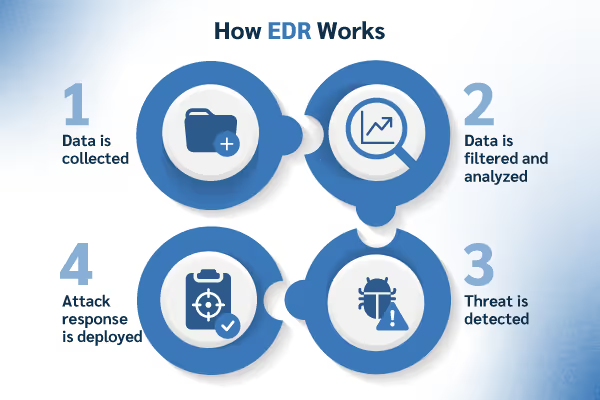
EDR systems operate through a continuous circular workflow designed to provide comprehensive endpoint security coverage. This process involves four main phases: detect, contain, investigate, and remediate. Understanding this workflow helps explain why EDR represents such a significant advancement over traditional security approaches.
The foundation of any EDR system is the deployment of lightweight software agents on each endpoint device. These agents serve as the eyes and ears of the security system, continuously collecting and transmitting telemetry data to a centralized platform for analysis. This architecture ensures that security teams maintain visibility into endpoint activities regardless of whether devices are connected to the corporate network or operating remotely.
The centralized platform serves as the brain of the operation, analyzing incoming endpoint data using a combination of threat intelligence feeds, behavioral analytics, and frameworks like MITRE ATT&CK to identify indicators of compromise (IOCs) and indicators of attack (IOAs). This analysis happens in near real-time, enabling rapid threat detection and response.
Continuous Data Collection and Monitoring
The data collection capabilities of modern EDR tools are comprehensive and sophisticated. Agents monitor and record a wide range of endpoint activities including process executions, file system changes, registry modifications, network connections, user behaviors, and memory activities. This endpoint data provides security analysts with a complete picture of what’s happening on each device.
Unlike traditional security solutions that might only capture specific events, EDR systems maintain detailed logs of all endpoint activities. This information is typically stored in cloud-hosted databases or data lakes that can handle massive volumes of data while providing fast query capabilities for both real-time analysis and historical investigations.
The efficiency of data collection is crucial for maintaining endpoint performance. Modern EDR solutions use advanced compression techniques, intelligent filtering, and optimized communication protocols to minimize the performance impact on endpoint devices while ensuring comprehensive coverage of security-relevant activities.
Real-time continuous monitoring enables immediate detection of suspicious behavior, while historical data analysis supports forensic investigations and helps security teams understand attack patterns over time. This dual capability is essential for both preventing active threats and learning from past incidents to inform future investigations.
Behavioral Analytics and Threat Detection
The heart of EDR’s advanced threat detection capabilities lies in its use of behavioral analytics and machine learning algorithms. Rather than relying solely on known threat signatures, these systems analyze patterns of behavior to identify activities that deviate from normal baseline operations.
Machine learning models trained on vast datasets of both malicious and benign activities can detect subtle indicators that might escape human analysis. These models continuously learn and adapt, improving their ability to identify new attack techniques and reducing false positives over time. The system looks for behavioral patterns associated with different stages of the cyber kill chain, from initial compromise through data exfiltration.
Event correlation across multiple endpoints is another critical capability that enables detection of sophisticated threats like advanced persistent threats and coordinated attacks. While individual activities on separate endpoints might appear benign, correlating these events can reveal patterns indicating lateral movement, privilege escalation, or coordinated data theft.
The integration of global threat intelligence services enhances detection accuracy by providing context about known attack campaigns, threat actor tactics, and emerging threats. This external intelligence is combined with internal behavioral analysis to create a comprehensive threat detection capability that can identify both known threats and as yet unknown threats using similar techniques.
Automated Response and Containment
When threats are detected, EDR systems can execute automated response capabilities to contain and neutralize threats before they can cause significant damage. These responses can range from simple actions like quarantining malicious files to more complex orchestrated responses involving multiple security tools.
Common automated response actions include isolating infected endpoints from the network to prevent lateral movement, terminating malicious processes, quarantining suspicious files, and blocking network connections to known command-and-control servers. More advanced systems can also restore affected systems to a known good state, particularly valuable for ransomware attacks where rapid recovery is critical.
Integration with Security Orchestration, Automation, and Response (SOAR) platforms enables EDR systems to execute complex incident response workflows automatically. This integration reduces the time between threat detection and appropriate response, minimizing the potential impact of security incidents and reducing the manual workload on security teams.
The automation capabilities don’t replace human judgment but rather augment it by handling routine response tasks and providing security analysts with the information and tools they need to make informed decisions about more complex threats. This approach significantly reduces threat dwell time—the period between initial compromise and detection—which is crucial for minimizing the impact of successful attacks.
Key EDR Capabilities and Features
Modern EDR security solutions offer a comprehensive suite of capabilities designed to address the full spectrum of endpoint security challenges. These features work together to provide layered protection that goes far beyond what traditional endpoint protection platforms can offer. Understanding these capabilities helps organizations evaluate which features are most important for their specific security requirements.
The integration of these various capabilities creates a synergistic effect where the whole becomes greater than the sum of its parts. Threat hunting capabilities inform automated response rules, forensic investigation tools provide context for behavioral analytics, and ransomware detection feeds into overall threat intelligence. This interconnected approach is what makes EDR such a powerful addition to an organization’s overall security posture.
Real-Time Threat Hunting
Proactively hunt threats represents one of the most valuable capabilities that EDR brings to security operations. Unlike traditional reactive security measures that wait for threats to trigger alerts, threat hunting involves actively searching for hidden or unknown threats that may have evaded automated detection systems.
Threat hunters use EDR data to test hypotheses about potential attack scenarios, searching for subtle indicators that might suggest the presence of advanced threats. This might involve looking for unusual process execution patterns, suspicious network communications, or file system changes that don’t match normal operational baselines. The ability to query massive datasets of endpoint data enables hunters to validate or disprove their theories quickly.
Custom queries and advanced analytics allow experienced security analysts to dig deep into endpoint telemetry data, following leads and investigating anomalies that automated systems might overlook. This human-in-the-loop approach is particularly effective against sophisticated attackers who deliberately try to blend their activities with normal system operations.
The benefits of proactive threat hunting extend beyond just finding hidden threats. The process also helps security teams better understand their environment, identify gaps in existing detection rules, and develop new hunting hypotheses based on emerging threat intelligence. This continuous improvement cycle makes the entire security program more effective over time.
Forensic Investigation and Analysis
When security incidents occur, having comprehensive forensic capabilities can mean the difference between understanding what happened and remaining in the dark about the scope and impact of an attack. EDR platforms provide detailed forensic tools that enable security analysts to reconstruct attack timelines, trace the full extent of compromise, and gather evidence for compliance or legal purposes.
Root cause analysis capabilities help investigators understand how an attack began, what vulnerabilities were exploited, and how the attacker moved through the environment. This information is crucial for preventing similar attacks in the future and for understanding whether sensitive data may have been compromised.
Attack timeline reconstruction uses the detailed logging capabilities of EDR systems to create a chronological view of all activities related to a security incident. This timeline helps investigators understand the sequence of events, identify all affected systems, and assess the full scope of the compromise.
Evidence collection and preservation features ensure that forensic data maintains its integrity for potential legal proceedings or regulatory investigations. EDR systems can automatically preserve relevant data when incidents are detected, preventing evidence tampering or loss due to log rotation or system changes.
Ransomware Detection and Rollback
Ransomware has become one of the most significant threats facing organizations today, with attacks becoming more sophisticated and damaging each year. EDR systems provide specialized capabilities for detecting ransomware attacks in their early stages and responding quickly to minimize damage.
Behavioral indicators of ransomware activity include rapid file encryption patterns, suspicious process behaviors, and attempts to delete shadow copies or backup files. EDR systems can detect these patterns in real-time, often identifying ransomware attacks within minutes of the encryption process beginning.
Automated rollback capabilities can restore affected systems to a pre-infection state, effectively undoing the damage caused by ransomware. This capability requires the EDR system to maintain continuous snapshots of critical system states, enabling rapid recovery without relying on traditional backup and restore processes.
The speed of detection and response is crucial for ransomware defense. The faster an organization can detect and contain a ransomware attack, the less data will be encrypted and the quicker operations can return to normal. Integration with backup systems and disaster recovery processes ensures comprehensive protection against these particularly destructive attacks.
Enhanced Visibility and Monitoring
One of the fundamental challenges in cybersecurity is maintaining visibility into all the assets and activities within an organization’s environment. EDR solutions provide comprehensive visibility across all managed and unmanaged endpoints, helping security teams understand their complete attack surface.
Discovery of rogue devices and shadow IT assets is a critical capability that helps organizations understand what devices are connecting to their networks and accessing their resources. This visibility extends to personal devices used for work, contractors’ equipment, and other unmanaged assets that might not be covered by traditional security tools.
Vulnerability assessment capabilities integrated into EDR platforms provide ongoing visibility into security weaknesses across the endpoint environment. This information helps security teams prioritize patching efforts and understand where additional security controls might be needed.
Centralized dashboard and monitoring capabilities give security operations teams a unified view of endpoint security across their entire environment. Real-time alerts, trend analysis, and reporting features enable teams to respond quickly to threats and communicate effectively with management about security status and incidents.
EDR vs. Other Security Solutions
Understanding how EDR fits into the broader cybersecurity ecosystem requires comparing it with other security technologies that organizations typically deploy. While EDR provides specialized endpoint-focused capabilities, it works best as part of a layered security approach that includes complementary technologies with different strengths and focus areas.
The key to effective cybersecurity is not choosing between these different approaches but rather understanding how they work together to create comprehensive defense. Each technology has its strengths and optimal use cases, and the most effective security strategies combine multiple solutions to address different aspects of the threat landscape.
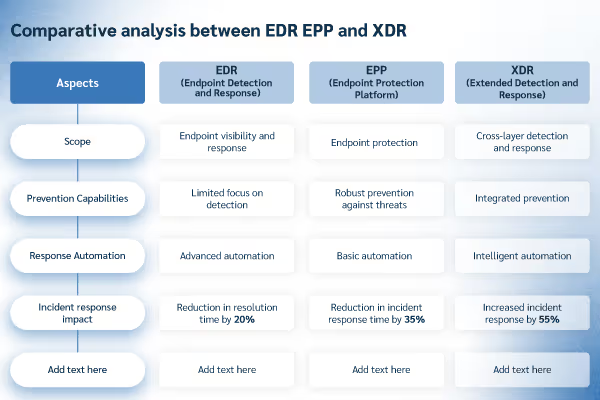
EDR vs. Endpoint Protection Platforms (EPP)
Endpoint Protection Platforms represent the evolution of traditional antivirus software, focusing primarily on preventing threats from executing on endpoint devices. EPP solutions typically include antivirus capabilities, firewalls, device control, and application whitelisting—all designed to stop threats before they can cause damage.
The fundamental difference between EPP and EDR lies in their approach to security. EPP focuses on prevention, using signatures, heuristics, and behavioral analysis to block known threats and suspicious activities. EDR, on the other hand, assumes that some threats will inevitably bypass preventive controls and focuses on detecting and responding to those threats quickly.
Modern endpoint security solutions increasingly combine EPP and EDR capabilities into unified platforms that provide both prevention and detection/response capabilities. This convergence makes sense because the same endpoint agents that collect data for EDR analysis can also enforce EPP policies, reducing complexity and improving efficiency.
The complementary nature of these technologies means that organizations benefit most from solutions that integrate both approaches. Prevention capabilities reduce the overall threat load that detection and response systems must handle, while detection capabilities provide a safety net for threats that bypass preventive controls.
EDR vs. Extended Detection and Response (XDR)
Extended Detection and Response (XDR) represents the next evolution beyond EDR, expanding visibility and correlation capabilities across multiple security domains including endpoints, networks, email, cloud applications, and other infrastructure components. While EDR specializes in endpoint-specific threats, XDR takes a broader approach to threat detection and response.
XDR platforms aggregate data from multiple security tools and use advanced analytics to correlate events across different domains. This broader perspective can help detect sophisticated attacks that span multiple attack vectors or involve both endpoint and network components.
The decision between EDR and XDR often depends on an organization’s maturity level, existing security infrastructure, and specific requirements. Organizations with well-established security programs might benefit from XDR’s comprehensive approach, while those focusing specifically on endpoint security might prefer the specialized capabilities of dedicated EDR solutions.
Many organizations implement EDR as a foundation and then expand to XDR capabilities as their security programs mature and their integration requirements become more complex. This evolutionary approach allows teams to build expertise gradually while expanding their security coverage.
EDR vs. SIEM and SOAR
Security Information and Event Management (SIEM) platforms focus on aggregating and analyzing log data from across an organization’s entire IT infrastructure, providing broad visibility into security events and enabling correlation across multiple systems. While SIEM platforms provide breadth, EDR solutions provide depth—offering detailed, high-fidelity data specifically about endpoint activities.
The relationship between EDR and SIEM is typically complementary rather than competitive. EDR systems generate high-quality security events that feed into SIEM platforms, while SIEM systems provide the broader context needed to understand how endpoint events fit into larger attack patterns.
Security Orchestration, Automation, and Response (SOAR) platforms focus on automating incident response workflows and orchestrating actions across multiple security tools. EDR solutions integrate with SOAR platforms to enable automated response capabilities that can act on EDR detections using broader organizational response procedures.
The combination of EDR, SIEM, and SOAR creates a powerful security ecosystem where each technology contributes its strengths. EDR provides detailed endpoint telemetry, SIEM correlates this with other security data, and SOAR orchestrates appropriate responses based on the combined intelligence.
EDR Implementation Best Practices
Successful EDR implementation requires careful planning, thoughtful deployment strategies, and ongoing optimization to maximize the value of the investment. Organizations that approach EDR deployment systematically tend to achieve better outcomes and faster time-to-value than those that rush into implementation without proper preparation.
The complexity of modern IT environments means that one-size-fits-all approaches rarely work effectively. Instead, organizations need to tailor their implementation approach based on their specific environment, security requirements, and organizational capabilities.
Planning and Preparation
Environment assessment forms the foundation of any successful EDR deployment. This assessment should include a comprehensive inventory of all endpoint devices, understanding of existing security tools and processes, and analysis of current security gaps and requirements. Understanding the scope and complexity of the environment helps inform deployment timelines and resource requirements.
Security requirements analysis should consider both current threats and anticipated future needs. This analysis should take into account regulatory compliance requirements, industry-specific threat landscapes, and organizational risk tolerance. The goal is to ensure that the selected EDR solution can address both immediate needs and long-term strategic objectives.
Team roles and responsibilities must be clearly defined before deployment begins. This includes identifying who will be responsible for day-to-day monitoring and response, who will handle advanced threat hunting activities, and how the EDR team will integrate with existing security operations. Clear role definition prevents confusion and ensures accountability.
Integration planning with existing security tools is crucial for maximizing the value of EDR investments. This planning should identify how EDR will integrate with SIEM platforms, how alerts will be handled, and how response workflows will be coordinated across different security tools. Proper integration planning prevents silos and ensures that EDR enhances rather than complicates existing security operations.
Deployment Strategies
Deployment method selection depends on the size and complexity of the organization’s environment. Large enterprises might use group policy or enterprise software distribution tools to deploy agents across thousands of endpoints, while smaller organizations might opt for manual installation or cloud-based deployment methods.
Phased rollout approaches reduce risk and allow teams to learn and optimize their processes before deploying across the entire environment. A typical phased approach might start with a pilot group of endpoints, expand to critical systems, and then roll out to the broader environment. This approach allows teams to identify and resolve issues before they affect the entire organization.
Agent communication and connectivity requirements must be carefully planned to ensure that endpoints can communicate with the central platform regardless of their location. This is particularly important for remote workers and mobile devices that may not always be connected to the corporate network.
Monitoring and troubleshooting during deployment helps identify and resolve issues quickly. This includes monitoring agent installation success rates, verifying data collection, and testing alert generation to ensure that the system is working as expected.
Configuration and Optimization
Initial configuration should focus on establishing baseline detection rules and response actions that provide immediate value while minimizing false positives. Most EDR platforms come with pre-configured rules based on common attack patterns, but these should be reviewed and adjusted based on the organization’s specific environment and requirements.
Tuning to reduce false positives is an ongoing process that requires continuous refinement based on actual alert patterns and feedback from security analysts. The goal is to maintain high detection sensitivity while ensuring that alerts are actionable and relevant. Effective tuning significantly improves analyst productivity and reduces alert fatigue.
Ongoing policy adjustments should be based on changes in the threat landscape, lessons learned from security incidents, and feedback from security teams. Regular review and updating of detection rules ensures that the EDR system continues to provide effective protection as threats evolve.
Performance monitoring and optimization help ensure that EDR agents don’t negatively impact endpoint performance while maintaining comprehensive security coverage. This includes monitoring resource usage, optimizing data collection parameters, and adjusting communication schedules to minimize impact on user productivity.
Common EDR Challenges and Solutions
While EDR provides significant security benefits, implementation and ongoing operation can present challenges that organizations need to address proactively. Understanding these common challenges and their solutions helps organizations prepare for success and avoid common pitfalls that can reduce the effectiveness of their EDR investments.
The key to overcoming these challenges is recognizing that they are normal parts of the EDR journey rather than insurmountable obstacles. With proper planning, realistic expectations, and continuous improvement efforts, organizations can maximize the value of their EDR investments while minimizing operational challenges.
Alert Fatigue and False Positives
Alert fatigue represents one of the most significant challenges facing security teams using EDR and other advanced security tools. When analysts are overwhelmed with too many alerts—particularly those that turn out to be false positives—they may become less effective at identifying and responding to real threats.
The causes of excessive alerts often include overly sensitive detection rules, lack of proper environmental tuning, and insufficient integration with other security tools that could provide additional context. Understanding these root causes is essential for developing effective solutions.
Tuning strategies should focus on adjusting detection sensitivity based on actual attack patterns observed in the environment while maintaining coverage of critical threat scenarios. This might involve creating environment-specific rules, adjusting thresholds for behavioral detection, and implementing risk-based scoring to prioritize the most critical alerts.
Automation for handling low-priority events can significantly reduce the manual workload on security analysts while ensuring that routine events are still properly processed. This might include automated responses for certain types of threats, automatic ticket creation for follow-up investigation, and integration with other security tools for additional context.
Integration with SIEM for alert correlation and noise reduction helps provide additional context that can help analysts distinguish between real threats and false positives. By correlating EDR alerts with other security data, teams can develop a more complete picture of potential threats and reduce the time spent investigating unrelated events.
Integration Complexities
Modern organizations typically operate complex security ecosystems with multiple tools from different vendors, each with its own APIs, data formats, and integration requirements. Integrating EDR solutions into these existing environments can be challenging but is essential for maximizing the value of security investments.
Challenges with incompatible APIs and data formats are common when trying to integrate EDR with existing security tools. Different vendors may use different data schemas, authentication methods, and communication protocols, making seamless integration difficult without additional development work.
Solutions using open APIs and middleware can help bridge these integration gaps. Many EDR vendors now provide comprehensive APIs and integration toolkits that make it easier to connect with other security tools. Additionally, middleware solutions and security orchestration platforms can help translate between different systems and data formats.
Custom scripting approaches may be necessary for some integration scenarios, particularly when connecting with legacy systems or specialized security tools. While this requires additional development effort, custom integrations can provide exactly the functionality needed for specific organizational requirements.
Vendor support and professional services can significantly ease integration challenges, particularly for complex environments or critical integrations. Many EDR vendors offer professional services to help with integration planning and implementation, which can be valuable for organizations with limited internal development resources.
Resource and Skill Constraints
The cybersecurity talent shortage affects many organizations’ ability to effectively implement and operate EDR solutions. Advanced threat detection and response requires specialized skills that may not be available within existing IT teams, creating challenges for organizations wanting to maximize their EDR investments.
Managed Detection and Response (MDR) services provide an alternative for organizations that lack the internal resources to operate EDR solutions effectively. MDR providers combine EDR technology with expert security analysts who monitor, investigate, and respond to threats on behalf of their clients. This approach allows organizations to benefit from advanced EDR capabilities without building large internal security teams.
Training programs for internal team development can help organizations build the skills needed to operate EDR solutions effectively. This might include vendor-provided training, industry certifications, and hands-on experience with the EDR platform. Investing in team development provides long-term benefits and helps organizations maintain control over their security operations.
Automation to reduce manual workload requirements can help smaller security teams manage larger environments more effectively. By automating routine tasks and responses, organizations can focus their limited human resources on high-value activities like threat hunting and strategic security improvements.
Future of EDR Technology
The EDR market continues to evolve rapidly, driven by advances in artificial intelligence, changes in IT infrastructure, and the constantly evolving threat landscape. Understanding these trends helps organizations make informed decisions about their long-term security strategies and technology investments.
The future of EDR is likely to be characterized by greater automation, broader integration with other security technologies, and enhanced capabilities for dealing with sophisticated threats. Organizations that understand these trends can position themselves to take advantage of new capabilities as they become available.
AI and Machine Learning Integration
Artificial intelligence and machine learning are becoming increasingly central to EDR capabilities, offering the potential to significantly improve detection accuracy while reducing the manual effort required to operate these systems effectively. Advanced AI models can analyze vast amounts of endpoint data to identify subtle patterns that might indicate sophisticated threats.
Automated threat analysis and response decision-making capabilities are becoming more sophisticated, enabling EDR systems to make complex decisions about threat classification and appropriate responses. This automation helps reduce the time between threat detection and response while ensuring consistent application of security policies.
Predictive analytics for proactive threat prevention represents an emerging capability that could help organizations stay ahead of threats rather than simply responding to them. By analyzing patterns in attack techniques and threat intelligence, AI-powered EDR systems may be able to predict likely attack scenarios and proactively strengthen defenses.
Continuous learning from security incidents and threat intelligence helps EDR systems become more effective over time. Machine learning models can incorporate lessons learned from past incidents, threat intelligence feeds, and industry research to improve their ability to detect new and evolving threats.
Cloud-Native EDR Solutions
The shift toward cloud-native EDR solutions reflects broader trends in IT infrastructure and offers significant benefits in terms of scalability, management, and integration with cloud workload protection platforms. Cloud-native solutions can provide better performance, easier scaling, and reduced infrastructure overhead compared to traditional on-premises deployments.
Scalability advantages are particularly important for growing organizations or those with fluctuating endpoint counts. Cloud-native solutions can automatically scale to accommodate changing requirements without requiring significant infrastructure investments or complex capacity planning.
Reduced infrastructure overhead and maintenance requirements make cloud-native EDR solutions attractive for organizations that want to focus on security outcomes rather than infrastructure management. Cloud-based solutions typically include automatic updates, backup and disaster recovery, and professional management of the underlying infrastructure.
Integration with cloud workload protection platforms provides comprehensive security coverage for organizations operating in hybrid or cloud-first environments. This integration ensures that security policies and visibility extend consistently across traditional endpoints and cloud workloads.
Choosing the Right EDR Solution
Selecting the appropriate EDR solution requires careful evaluation of multiple factors including technical capabilities, organizational requirements, vendor characteristics, and total cost of ownership. The right choice depends on the specific needs and constraints of each organization, making a systematic evaluation process essential.
The evaluation process should balance current requirements with future needs, ensuring that the selected solution can grow and adapt as the organization’s security needs evolve. This forward-looking approach helps organizations avoid costly migrations and ensures better long-term value from their EDR investments.
Essential Evaluation Criteria
Detection accuracy and coverage of the MITRE ATT&CK framework should be primary considerations when evaluating EDR solutions. The MITRE ATT&CK framework provides a comprehensive taxonomy of threat techniques, and EDR solutions that provide good coverage of this framework are more likely to detect sophisticated threats effectively.
Agent performance impact must be carefully evaluated to ensure that EDR deployment doesn’t negatively affect user productivity or system performance. This evaluation should include testing in realistic environments with typical workloads to understand the actual impact on endpoint performance.
Investigation tools and forensic capabilities vary significantly between different EDR solutions. Organizations should evaluate these capabilities based on their specific investigation requirements, compliance needs, and the technical skills of their security teams.
Integration options with existing security infrastructure are crucial for maximizing the value of EDR investments. This evaluation should consider both current integration requirements and anticipated future needs as the security infrastructure evolves.
Vendor Assessment
Vendor reputation and market presence provide important context for evaluating EDR solutions. Established vendors with strong market positions are more likely to continue innovating and supporting their products over the long term, while newer vendors might offer innovative capabilities but with greater uncertainty about long-term viability.
Support quality and professional services availability can significantly impact the success of EDR implementations. Organizations should evaluate vendor support capabilities, response times, and the availability of professional services for implementation, integration, and ongoing optimization.
Pricing models and total cost of ownership considerations should include not just license costs but also implementation, training, and ongoing operational costs. Different pricing models (per-endpoint, consumption-based, etc.) may be more or less favorable depending on the organization’s specific situation.
Trial period and proof-of-concept evaluation approaches allow organizations to test EDR solutions in their actual environments before making final decisions. These evaluations should include realistic testing scenarios that reflect the organization’s actual security challenges and operational requirements.
FAQ
Can EDR replace traditional antivirus software?
EDR and traditional antivirus serve complementary rather than competing purposes in modern endpoint security. While EDR excels at detecting unknown threats and providing detailed investigation capabilities, traditional antivirus (or modern Endpoint Protection Platforms) still provides valuable prevention capabilities for known threats. Most organizations benefit from solutions that combine both approaches, often integrated into unified platforms that provide comprehensive endpoint security.
What types of threats can EDR detect that antivirus cannot?
EDR can detect fileless attacks that operate entirely in memory, advanced persistent threats that use legitimate system tools, zero-day exploits that haven’t been seen before, and sophisticated social engineering attacks that bypass traditional signature-based detection. EDR’s behavioral analytics can identify suspicious patterns even when the specific malware variant is unknown, making it particularly effective against polymorphic threats and custom malware developed by advanced threat actors.
How does EDR impact endpoint performance?
Modern EDR solutions are designed to minimize performance impact through efficient data collection methods, optimized communication protocols, and lightweight agent architectures. Typical performance impact is less than 5% of system resources, but this can vary based on the specific solution and configuration. Organizations should test EDR solutions in their actual environments to understand the real-world performance impact before full deployment.
What is the difference between EDR and MDR services?
EDR refers to the technology platform that provides endpoint detection and response capabilities, while MDR (Managed Detection and Response) refers to a service model where external experts operate EDR technology on behalf of organizations. MDR services typically include 24/7 monitoring, threat hunting, incident response, and expert analysis, making advanced EDR capabilities accessible to organizations that lack internal security expertise or resources.
How much does EDR typically cost for small businesses?
EDR pricing varies significantly based on the number of endpoints, feature requirements, and vendor. Small businesses can expect to pay anywhere from $5 to $50 per endpoint per month, depending on the sophistication of the solution and level of service included. Cloud-based solutions often offer more flexible pricing models that can be more affordable for smaller organizations, and some vendors offer solutions specifically designed for small and medium businesses.
Can EDR work with existing security tools and SIEM platforms?
Yes, modern EDR solutions are designed to integrate with existing security infrastructure through APIs, standard log formats, and purpose-built integrations. Most EDR platforms can send alerts and data to SIEM systems, integrate with SOAR platforms for automated response, and coordinate with other security tools to provide comprehensive defense. However, the ease and sophistication of integration varies between vendors, making this an important evaluation criterion.
What skills do security teams need to effectively use EDR?
Effective EDR operation requires understanding of threat hunting techniques, incident response procedures, forensic analysis methods, and familiarity with attack techniques and tactics. Teams also need skills in query languages for searching EDR data, understanding of network protocols and system behaviors, and knowledge of threat intelligence frameworks like MITRE ATT&CK. Many organizations address skill gaps through training programs, vendor support, or managed detection and response services.
How long does EDR implementation typically take?
EDR implementation timelines vary based on environment size and complexity, but typical deployments range from 2-12 weeks. Small organizations with simple environments might complete deployment in 2-4 weeks, while large enterprises with complex requirements might take 2-3 months or longer. The timeline includes planning, agent deployment, configuration, tuning, and training phases. Phased rollout approaches can provide initial value more quickly while reducing implementation risk.
EDR represents a foundational element of modern cybersecurity, providing the advanced threat detection and automated response capabilities needed to defend against today’s sophisticated attack landscape. As cyber threats continue to evolve and become more complex, organizations need security solutions that can adapt and respond dynamically rather than relying solely on preventive controls.
The investment in EDR technology pays dividends not just in improved security outcomes but also in enhanced operational efficiency for security teams. By automating routine response tasks, providing detailed forensic capabilities, and enabling proactive threat hunting, EDR helps organizations build more mature and effective security operations that can stay ahead of evolving threats.
Whether you’re just beginning to evaluate EDR solutions or looking to optimize your existing deployment, understanding these key concepts and best practices will help you maximize the value of your endpoint security investments and build a more resilient defense against the cyber threats of today and tomorrow.