Crises don’t wait for a convenient moment. A ransomware attack, system outage, or natural disaster can disrupt operations in minutes—and how your organization responds in those first moments makes all the difference.
That’s where three critical strategies come into play: incident response, disaster recovery, and business continuity. While these plans are often mentioned together, they serve very different purposes and activate at different stages of a disruption.
This guide explains the difference between an incident response plan, a disaster recovery plan, and a business continuity plan—and how they work together in real-world scenarios.
- Incident response focuses on detecting, containing, and eliminating active threats.
- Disaster recovery restores systems and data after an incident or outage.
- Business continuity ensures critical operations continue during disruption.
Understanding how these plans differ—and how they support one another—is essential for building a resilient organization. Whether you’re creating your first framework or refining an existing one, this article will help you make informed decisions that protect your operations, data, and reputation.
Which one comes first?
When something goes wrong, one of the first questions teams ask is: Which plan do we activate first?
The answer isn’t always the same—but the timeline of the incident provides a clear starting point.
In most scenarios, these three plans activate in a specific order, based on what the organization is facing at that moment.
1. Immediate threat → Incident response plan
If there is an active threat—such as a ransomware attack, phishing breach, or unauthorized access—incident response comes first.
The priority at this stage is to:
- Detect and confirm the incident
- Contain the threat to prevent further damage
- Eradicate malicious activity
Until the threat is under control, attempting recovery or restoration can make things worse. Incident response focuses on stopping the bleeding before anything else happens.
2. System and data restoration → Disaster recovery plan
Once the incident is contained or the disruptive event has passed, disaster recovery takes over.
This is where the organization focuses on:
- Restoring systems, applications, and infrastructure
- Recovering clean data from backups
- Reducing downtime and data loss
Disaster recovery is not about fighting the threat—it’s about bringing systems back online safely and in the correct order.
3. Sustained operations → Business continuity plan
While incident response and disaster recovery focus on security and technology, business continuity ensures the organization keeps functioning throughout the disruption.
Business continuity may activate:
- In parallel with incident response or disaster recovery
- When downtime extends beyond acceptable limits
- When people, processes, or locations are impacted
This plan addresses how teams work, how customers are supported, and how critical operations continue—even if systems are partially unavailable.
Why “which comes first” depends on the scenario
The order is not fixed—it depends on what triggered the disruption:
- Cyberattack (ransomware, breach): Incident response → Disaster recovery → Business continuity (as needed)
- Natural disaster or physical outage: Business continuity → Disaster recovery → Incident response (if security risks emerge)
- System failure with no security threat: Disaster recovery → Business continuity
The key takeaway is this: each plan has a different job, and activating the wrong one first can delay recovery or increase risk.
Understanding when to use incident response, disaster recovery, and business continuity—and how they sequence together—is what turns separate plans into a coordinated resilience strategy.
Key differences: incident response vs. disaster recovery vs. business continuity
When a disruption occurs, confusion often comes from treating incident response, disaster recovery, and business continuity as interchangeable. They are not. Each plan addresses a different problem, at a different moment, with different owners and outcomes.
The table below highlights the core differences between an incident response plan, a disaster recovery plan, and a business continuity plan:
What is a business continuity plan?
A Business Continuity Plan (BCP) is an organization-wide strategy designed to ensure that critical business functions continue operating during a disruption—even when systems, facilities, or normal workflows are unavailable.
Unlike disaster recovery or incident response, a business continuity plan is not primarily about technology. Its focus is on keeping the business moving by coordinating people, processes, communications, and external dependencies.
A strong business continuity plan typically includes:
- Identification of critical business functions and dependencies
- Defined roles and decision-making authority during disruption
- Alternative workflows and manual procedures
- Employee communication and escalation plans
- Vendor and third-party continuity considerations
Business continuity planning ensures that customers are supported, employees know how to operate under abnormal conditions, and leadership can make informed decisions while recovery efforts are underway.
What is a disaster recovery plan?
A Disaster Recovery Plan (DRP) focuses on restoring IT systems, applications, and data after a disruptive event such as a cyberattack, system failure, or natural disaster.
Disaster recovery does not address active threats. Instead, it begins after the incident is contained or the event has passed, providing a structured path to safely bring systems back online.
A well-defined disaster recovery plan outlines:
- Criteria for declaring a disaster
- Recovery sequencing for critical systems
- Restoration procedures for data and applications
- Testing and validation processes to ensure successful recovery
Two key metrics define disaster recovery success:
- Recovery Time Objective (RTO): How quickly systems must be restored
- Recovery Point Objective (RPO): How much data loss is acceptable
These objectives drive decisions around infrastructure design, redundancy, and recovery methods.
Disaster recovery answers the question: “How do we restore our systems and data safely, within acceptable limits?”
What is an incident response plan?
An Incident Response (IR) Plan is a structured approach for detecting, containing, and eliminating active cybersecurity threats.
It is activated the moment a security incident is suspected and focuses on limiting damage and preventing further spread, not on system restoration.
A mature incident response plan follows a defined lifecycle:
- Preparation – Roles, tools, and playbooks are established
- Identification – The incident is detected and confirmed
- Containment – The threat is isolated and controlled
- Eradication – Malicious elements are removed
- Recovery – Systems are stabilized and monitored
- Lessons learned – Gaps are documented and improvements made
Examples include isolating compromised devices after a phishing attack or blocking lateral movement during a ransomware incident.
Scope comparison: people, processes, technology, and governance
While incident response, disaster recovery, and business continuity are often grouped together, their scope inside the organization is very different. Understanding who owns each plan—and what it actually covers—is critical to avoiding confusion during a crisis.
This breakdown shows how each strategy maps across people, processes, technology, and governance.
Incident response: security-led and threat-focused
Incident response is primarily owned by security and IT security teams. Its scope is narrow but urgent, focused on identifying and containing active threats.
- People: SOC analysts, security engineers, incident response leads
- Processes: Detection, containment, eradication, forensic analysis
- Technology: Endpoints, identity systems, network controls, security tools
- Governance: Playbooks, escalation paths, breach notification requirements
Ownership is clear and centralized. Decisions need to be made fast, often under pressure, with minimal ambiguity.
Disaster recovery: IT-owned and infrastructure-driven
Disaster recovery sits squarely with IT and infrastructure teams. Its job is to restore systems and data after an incident or outage has been stabilized.
- People: IT operations, infrastructure engineers, cloud or platform teams
- Processes: Backup restoration, system failover, recovery sequencing
- Technology: Servers, cloud services, applications, data backups
- Governance: Recovery objectives (RTO/RPO), testing schedules, DR runbooks
Disaster recovery is measured by how quickly and safely systems can be brought back online, not by how threats are handled.
Business continuity: leadership-driven and organization-wide
Business continuity has the broadest scope and typically requires executive ownership. It extends beyond IT to ensure the entire organization can continue operating during disruption.
- People: Executive leadership, operations, HR, communications teams
- Processes: Alternative workflows, remote work plans, vendor continuity
- Technology: Collaboration tools, access management, critical business systems
- Governance: Continuity policies, crisis management structures, compliance
Unlike incident response or disaster recovery, business continuity spans multiple departments and depends heavily on coordination and communication.
Why ownership clarity matters
When ownership is unclear:
- Security teams may try to manage operational decisions
- IT teams may restore systems before threats are contained
- Leadership may lack visibility into what’s actually happening
Clear accountability ensures each plan does its job—without overlap, delays, or conflicting actions. That clarity is what turns three separate plans into a cohesive resilience strategy.
A comparison of BCP, DR, and IR
In summary, while BCP, DR, and IR strive to reduce the effect of unexpected occurrences, each plan has a distinct emphasis, strategy, and scope. All three plans should be in place for organizations to ensure their preparedness and resilience in the face of disruptions and crises. Integrating response and disaster recovery plans is crucial, as both are necessary to effectively manage incidents and ensure swift recovery, enhancing overall organizational resilience. Additionally, many industries are subject to regulations that require robust continuity and recovery planning to maintain compliance and avoid penalties.
When to use each plan: real-world scenarios
Knowing the difference between incident response, disaster recovery, and business continuity is helpful—but knowing when to activate each one is what truly matters when the clock is ticking.
Here are real-world examples that show how these plans come into play, often working together:
1. A ransomware attack locks your files
- Incident Response kicks in first: Your security team isolates the affected devices, stops the spread, and begins investigating the breach.
- Disaster Recovery follows: Once contained, your IT team restores clean backups to minimize downtime.
- Business Continuity may be triggered if customer service or operational systems are affected long enough to disrupt day-to-day functions.
2. Your main office catches fire
- Disaster Recovery steps in: Systems and data are restored from offsite backups or cloud platforms.
- Business Continuity ensures employees can work from a secondary location, access critical resources, and communicate with clients.
- Incident Response might play a small role if the fire led to device theft or triggered a physical security breach.
3. An employee clicks a phishing link
- Incident Response is the priority: The team identifies the compromised account, locks it down, and scans for lateral movement or data exfiltration.
- Disaster Recovery isn’t always needed, unless files or systems were damaged or encrypted.
- Business Continuity is rarely impacted, unless the phishing incident affected essential communication or operations.
4. A natural disaster disrupts infrastructure
- Business Continuity leads the response: Pre-established protocols ensure your team can keep working (remote tools, alternative suppliers, etc.).
- Disaster Recovery supports the effort: Critical systems are restored as soon as connectivity or access is possible.
- Incident Response may not be required—unless the disaster was used as a distraction for a cyberattack (yes, it happens!).
How these plans work together: building an integrated strategy
Incident response, disaster recovery, and business continuity aren’t just checkboxes on a compliance list—they’re parts of a bigger puzzle. When designed in silos, these plans can lead to gaps, delays, or even conflicting actions during a crisis.
That’s why integration matters.
To see how these three plans interact with one another, we may generate the following table:

A layered, sequential flow
Think of your resilience strategy as a flow:
- Incident Response contains the immediate threat.
- Disaster Recovery restores systems and data to resume operations.
- Business Continuity ensures people, processes, and communication don’t stop while the other two plans are in motion.
Each plan supports the next—working in parallel when needed or stepping in sequentially depending on the scenario.
Why siloed planning fails
Without coordination:
- Teams duplicate efforts or overlook responsibilities.
- Communication breaks down across departments.
- Recovery takes longer than it should—and customers notice.
Use a RACI matrix to clarify ownership
To avoid confusion, map out responsibilities using a simple RACI matrix:
This helps eliminate the “who’s doing what?” problem during high-stress events.
Metrics that define success: RTO, RPO, MTTR, and containment time
Understanding how incident response, disaster recovery, and business continuity work together is only part of the equation. To know whether these plans are actually effective, organizations need the right metrics—and those metrics are not the same for every plan.
Each strategy is measured differently because each one solves a different problem.
Incident response metrics: speed of detection and containment
Incident response is about how quickly a threat is identified and stopped. The most important metrics here focus on time and control.
Key incident response metrics include:
- Time to detect (TTD): How long it takes to identify a security incident
- Containment time: How quickly the threat is isolated to prevent spread
- Mean time to respond (MTTR – response): How fast teams act once an incident is confirmed
Success in incident response is not measured by uptime or recovery speed—it’s measured by how effectively damage is limited.
Disaster recovery metrics: RTO and RPO
Disaster recovery is measured by how well the organization can restore systems and data after an incident or outage.
The two most critical disaster recovery metrics are:
- Recovery Time Objective (RTO): The maximum acceptable time to restore a system
- Recovery Point Objective (RPO): The maximum acceptable amount of data loss
These metrics define how much downtime and data loss the business can tolerate—and they directly shape backup frequency, infrastructure design, and recovery strategies.
Business continuity metrics: operational resilience
Business continuity focuses on the organization’s ability to continue critical operations, even when systems are degraded or unavailable.
Common business continuity metrics include:
- Maximum tolerable downtime for key processes
- Time to resume critical business functions
- Communication and response time across teams and stakeholders
These metrics are less technical and more operational, reflecting how people and processes adapt during disruption.
Why mixing metrics leads to failed recoveries
One of the most common planning mistakes is applying the wrong metrics to the wrong plan.
For example:
- Using RTOs to judge incident response performance
- Restoring systems (DR) before containment metrics are met (IR)
- Measuring business continuity success solely by IT uptime
When metrics are mixed:
- Threats may resurface after recovery
- Systems may be restored into an insecure environment
- Operations may resume without proper coordination
Clear, plan-specific metrics ensure that incident response stops the threat, disaster recovery restores systems safely, and business continuity keeps the organization running—in the right order and for the right reasons.
How to implement these 3 plans (broken down by stages)
Preparation stage
- BCP: The organization defines essential business operations and creates a strategy to maintain their continuation during and after an interruption.
- DR: The organization installs backup methods for its IT infrastructure and systems and creates a disaster recovery strategy.
- IR: The organization assesses its cybersecurity risks regularly and produces an incident response plan to identify, contain, eliminate, and recover from a cybersecurity event or breach.
Crisis stage
- IR: The organization recognizes a cybersecurity event and launches its incident response strategy to control and remove the assault.
- BCP: By adopting the BCP, the incident response team guarantees that vital business functions continue during the cybersecurity crisis.
- DR: Once the situation has been stabilized, the DR plan is implemented to restore the impacted IT infrastructure and systems.
Recovery stage
- DR: The firm restores its IT infrastructure and systems, including data backup and recovery, to limit downtime and data loss.
- BCP: The organization is still putting in place the BCP to ensure that critical business processes continue throughout recovery.
- IR: The corporation conducts a post-event analysis and adjusts its incident response plan and risk assessment based on the lessons learned.
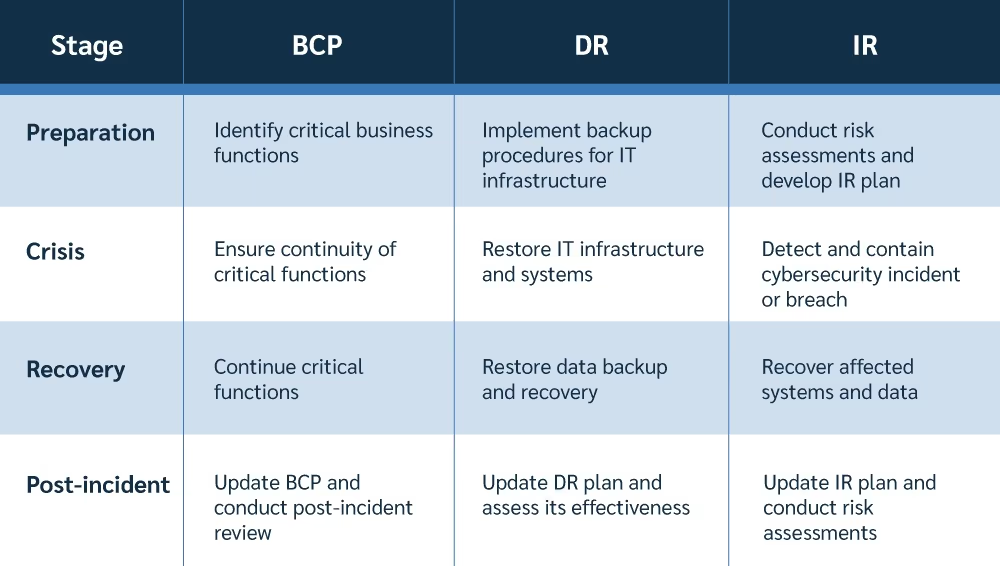
By sticking to this timeline, the business is well-prepared to cope with any interruption or crisis, as it has a strategy in place for each phase and ensures that BCP, DR, and IR work together to minimize the impact of the incident.
Addressing cyber attacks and data security
A disaster recovery plan aims to minimize downtime and data loss, ensuring that business operations can resume as quickly as possible after an event.
Incident response plans are equally crucial in the face of cyber attacks. These plans provide a clear, step-by-step framework for responding to and containing the impact of a security incident, such as a data breach or ransomware attack. By having well-defined incident response procedures, organizations can efficiently detect, respond to, and recover from security incidents, reducing the risk of prolonged operational downtime.
Business continuity plans play a vital role in maintaining business operations during any disruption. By identifying critical business functions and outlining strategies to keep them running, business continuity plans ensure that essential services continue with minimal interruption—even in the midst of a crisis.
A key element of disaster recovery planning is data backup and secure storage. Regular data backups enable organizations to restore lost data and resume normal business operations quickly, whether the disruption is caused by a cyber attack, hardware failure, or natural disaster. By prioritizing data security and integrating comprehensive backup solutions, organizations can protect their most valuable assets and ensure a swift recovery from any event.
The role of data backup and storage in continuity
Data backup and storage are foundational to effective business continuity planning. In the event of a disaster or cyber attack, the ability to recover critical data and systems is what enables organizations to maintain business operations and minimize losses. A robust disaster recovery plan should include regular, automated data backups and a clear process for restoring data and systems to ensure business continuity.
Cloud-based services have become an increasingly popular solution for data backup and storage. These platforms offer secure, reliable, and scalable options for protecting critical business data, allowing organizations to access and restore information from virtually anywhere. This flexibility is especially valuable for organizations with remote workforces or multiple locations.
Incident response plans should also address data backup and storage procedures. By ensuring that critical data is regularly backed up and securely stored, organizations can quickly recover from a security incident and restore normal business operations. This proactive approach not only supports disaster recovery but also strengthens overall data security.
Business continuity plans must prioritize data security to prevent data breaches and cyber attacks from compromising critical business operations. By integrating secure data backup and storage solutions into continuity and recovery strategies, organizations can safeguard their operations and ensure resilience in the face of any disaster.
Maintaining business operations during disruption
Maintaining business operations during a disruption is essential for minimizing downtime and protecting an organization’s reputation. Business continuity plans should begin by identifying critical business functions and developing targeted strategies to keep these functions running, even when normal operations are interrupted.
Incident response plans play a key role in this process by outlining clear procedures for communicating with stakeholders and maintaining transparency during a security incident. Effective communication helps manage expectations, reduces confusion, and preserves trust with customers, partners, and employees.
Disaster recovery plans should focus on the rapid recovery of critical systems and data, enabling organizations to resume normal business operations as quickly as possible. Prioritizing the restoration of essential services ensures that the most important business functions are up and running first, reducing the impact of the disruption.
Regular testing and updating of continuity and recovery plans are vital for ensuring that organizations can respond effectively to disruptions. By routinely evaluating and refining these plans, businesses can identify gaps, improve response times, and maintain seamless business operations—even in the face of unexpected events.
Testing and updating continuity and recovery plans
This is crucial for ensuring that organizations remain prepared to respond to disruptions and maintain business operations. Regular testing of disaster recovery plans helps identify weaknesses and areas for improvement, ensuring that critical systems and data can be recovered quickly and efficiently.
Incident response plans should be updated frequently to reflect changes in the organization’s security posture and to address emerging cyber threats. As the threat landscape evolves, so too must the strategies and procedures for responding to security incidents.
Business continuity plans also require ongoing review and updates to remain relevant and effective. Changes in business processes, technology, or personnel can all impact the effectiveness of continuity strategies, making regular assessments essential.
Organizations should conduct regular risk assessments to identify potential vulnerabilities and develop strategies for mitigating these risks. By integrating risk assessments into the testing and updating process, businesses can proactively address new threats and ensure that their continuity and recovery plans remain robust and effective.
Common challenges and mistakes in continuity planning
Organizations often face several challenges when developing and maintaining continuity plans. Common obstacles include inadequate funding, limited resources, and insufficient testing and training. These issues can undermine the effectiveness of business continuity and incident response plans, leaving organizations vulnerable during a crisis.
Mistakes in continuity planning frequently involve failing to identify critical business functions, neglecting proper data backup and storage, and lacking clear communication with stakeholders. Overlooking these key elements can result in prolonged downtime, data loss, and reputational damage.
To avoid these pitfalls, organizations should prioritize continuity planning and allocate sufficient resources to ensure that plans are comprehensive and up-to-date. Integrating incident response plans with business continuity plans creates a unified approach to managing disruptions, ensuring that all aspects of response and recovery are covered.
Regular review and updating of continuity and recovery plans are essential for identifying and correcting mistakes before they become costly problems. By committing to ongoing improvement, organizations can strengthen their ability to respond to disruptions and protect their business, data, and reputation.
Where Prey fits in
Prey supports all three pillars:
- In incident response, Prey helps you locate, lock, and wipe compromised or lost devices.
- For disaster recovery, our tools enable quick device status checks and secure recovery actions.
- In business continuity, Prey ensures device visibility and mobility even when your team is dispersed.
Takeaway: Don’t think of these plans as separate binders. Think of them as a single, connected strategy—built to keep your organization secure, operational, and resilient no matter what comes your way.
Takeaways
It is critical to have a Business Continuity Plan (BCP), Disaster Recovery Plan (DRP), and Incident Response Plan (IR) in place to protect an organization's operations, data, and reputation. Each strategy has its own set of goals: The BCP plan focuses on ensuring that critical business functions continue during and after a disruption; the DR plan focuses on quickly restoring IT infrastructure and systems following a catastrophic event; and the IR plan focuses on identifying, containing, eradicating, and recovering from a cybersecurity incident or breach.
Planning for all three strategies is vital since each one is critical in protecting an organization's operations, data, and reputation. In addition, by implementing all three strategies, businesses may guarantee they are well-prepared to deal with any disruption or disaster.
All three plans rely heavily on regular testing and maintenance. Frequent testing ensures that the plans are functional and relevant, while maintenance identifies and addresses possible flaws. Testing and maintenance regularly might be the difference between a successful and a disastrous reaction.
Businesses must prioritize developing and testing business continuity, disaster recovery, and incident response strategies to ensure their success and relevance. As a consequence, they will be well-prepared to handle any disruption or crisis that may occur. Remember that failing to plan is planning to fail.




