What is data encryption?
Data encryption consists of hiding information from malicious actors or anyone else with prying eyes.
Data is information. It can be an email message, the contents of a database, or a file stored on a laptop. This includes stored data, which must be protected from unauthorized access when it resides on devices, servers, or databases.
We encrypt data to keep it confidential. Data encryption is part of a broader class of cybersecurity countermeasures known as data security. Data security is all about keeping our data safe from unauthorized access, ransomware lockup (which is a malicious form of encryption), breach, or malicious corruption, i.e., changing data to make it useless.
How does data encryption work?
Modern data encryption is a form of cryptography, an ancient technique of hiding information by substituting one character for another. The word ‘encryption’ is a blend of English and Greek that means “in hidden” or, more loosely, “in hiding.”. Encryption works through a complex mathematical algorithm known as a data encryption cipher. Like the secret decoder ring found in your child’s cereal box, the cipher algorithm transforms normalized data (i.e., plaintext) into a sequence of ostensibly random, unrecognizable characters known as “ciphertext.”
The encryption process involves a series of steps where data is systematically converted into an encoded format using specific rules and keys, ensuring the security and complexity of the protected information.
The ciphertext is unreadable. For example, the phrase, “Hi, how are you?” might encrypt into a ciphertext that reads, “8363, 5017, 11884, 9546.” To get back to “Hi, how are you” requires a process of decryption.
Decoding information from ciphertext to plaintext is called decryption and involves the same algorithmic “key” that data encryption uses. The encryption and decryption processes work together, using symmetric or asymmetric encryption keys, to secure data during transmission and allow authorized recovery of the original information.
Who needs to use data encryption?
The answer is just about anyone. You don’t have to be a secret agent to want to keep your data confidential. In fact, you might be using encryption without even knowing it. Many technology services encrypt and decrypt your data so it will be safe when they use it.
Businesses should encrypt data that could damage their financial results if it were breached. Individuals should encrypt sensitive personal data like their medical histories and social security numbers. It is essential to use encryption to protect important data from unauthorized access and potential breach.
Benefits of data encryption
- Data Integrity: By seeing any changes or corruption in encrypted data, encryption helps maintain data integrity and enables a swift response to potential fraud.
- Device Protection: By reducing the risks involved with data transfer and adding an extra layer of security through sophisticated authentication procedures, encryption technology protects data across many devices.
- Remote Office Security: With increased remote work, encryption helps protect data from theft or unintentional loss.
- Regulatory Compliance: To ensure that customer data is handled and stored safely, encryption helps organizations comply with rules particular to their industry.
- Cloud Data Security: When data is transferred to cloud storage, privacy is guaranteed by encrypted storage.
- Intellectual Property Protection: Data encryption protects intellectual property like music or software by preventing unlawful use, duplication, or reverse engineering, especially when used with digital rights management systems.
Intellectual Property Protection: Data encryption protects intellectual property like music or software by preventing unlawful use, duplication, or reverse engineering, especially when used with digital rights management systems.
Threats to data security
Data security threats are constantly evolving, with attackers employing increasingly sophisticated methods to gain access to sensitive data. Brute force attacks, for example, involve systematically trying every possible combination of encryption keys in an attempt to decrypt data. As computing power grows, these attacks become more feasible, making it critical to use strong data encryption algorithms and long, complex encryption keys. Hacking is another major threat, where malicious actors exploit vulnerabilities in systems or software to bypass security controls and access confidential data.
Unauthorized access can also occur through weak access controls or human error, exposing sensitive information to those without permission. To protect data from these threats, organizations must implement comprehensive data security measures, including advanced encryption standard (AES) encryption, robust access controls, and continuous monitoring. By leveraging modern data encryption solutions and staying vigilant, organizations can significantly reduce the risk of data breaches and ensure their sensitive data remains protected.
Data encryption solutions
There are two basic kinds of encryption solutions: Those for data at rest and data in transit.
At rest, data is information that is stored such as on servers or a computer hard drive. Data in transit means that email or internal system-to-system messages that carry data around your network are transmitting the information.
Different solutions are available for data at rest versus data in transit. Systemically, each has its own impact.For data at rest, you have to configure any application that needs access to encrypted data with the means to decrypt it. There are quite a few data security solutions for this, such as encryption software like Bitlocker (for Windows) or Firevault (for macOS), which help protect data by encrypting the entire drive.
For data in transit, you have to arrange for both the sender and receiver to have to encrypt/decrypt capabilities. This type of encryption is known as end-to-end encryption or E2EE. These requirements create administrative burdens, and things can quickly become quite complex when you’re sending encrypted messages outside of your organization and so forth.
Developing a robust encryption strategy is essential to ensure comprehensive data security and regulatory compliance.

Common data encryption types
Let’s go over the most common data encryption types. The two most widely used methods for data encryption are public key, also known as asymmetric encryption, and private key, or symmetric encryption. Both rely on key pairs but differ in how the sending and receiving parties share the keys and handle the encrypt/decrypt process, with asymmetric encryption utilizing distinct decryption processes that involve a private key to securely decrypt data encrypted with a public key.
Public key encryption - asymmetric encryption
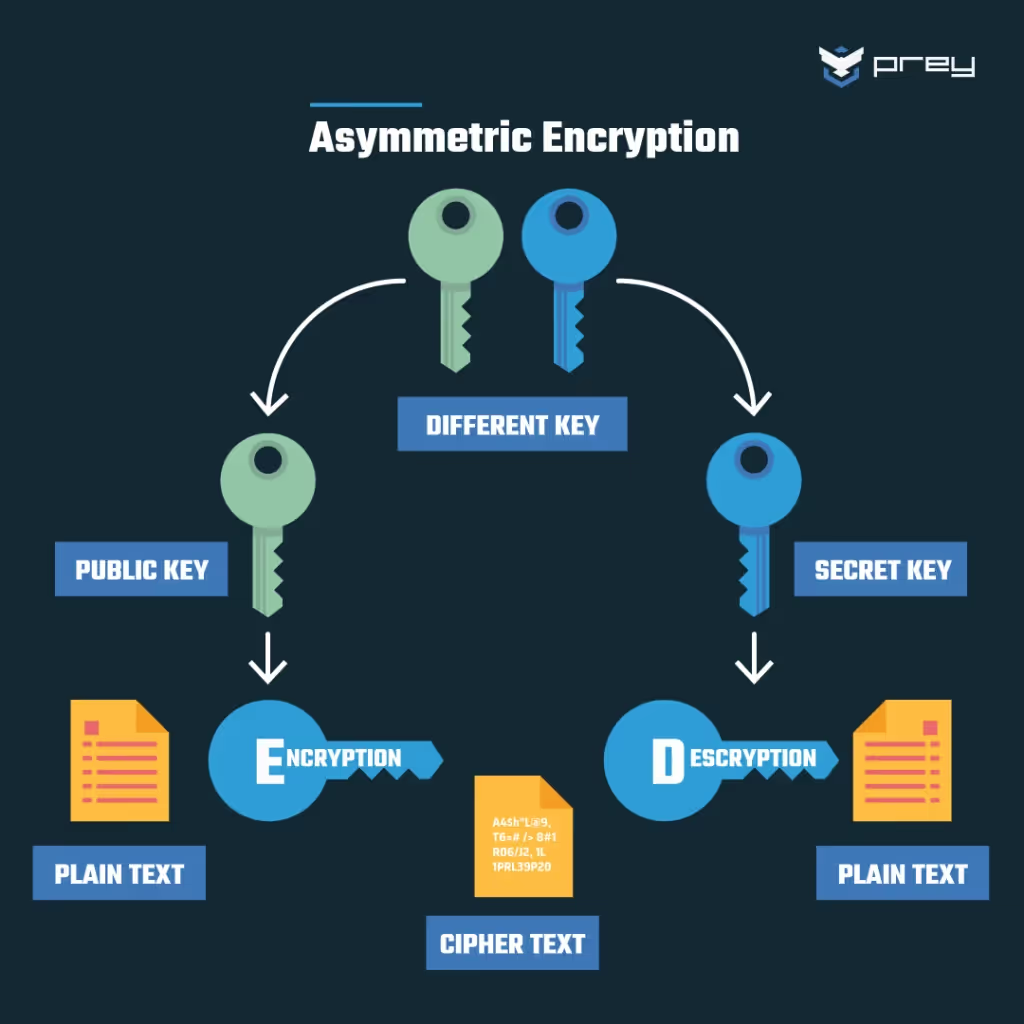
With public-key/asymmetric encryption, the sender uses a publicly known key to encrypt the data. The receiver has the private key that forms the other half of the public/private key pair. The receiver can decrypt the data by using the private key in combination with the public key.
Elliptic curve cryptography (ECC) is a modern asymmetric encryption method that employs complex mathematical curves for secure data encryption, offering greater efficiency and strength compared to traditional methods like RSA.
Private key encryption - symmetric encryption
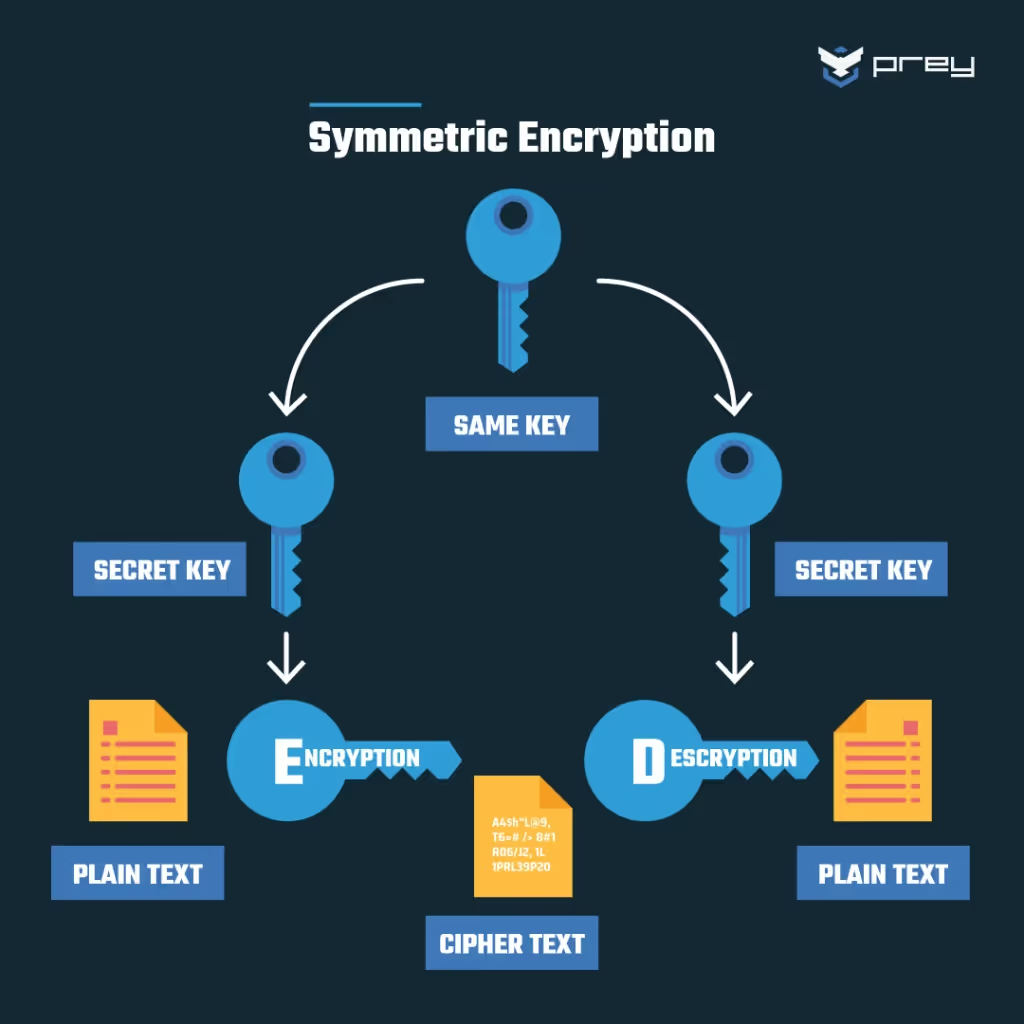
In Private key/symmetric encryption, both sender and receiver have the same, secret key. As you might imagine, there’s a lot of management overhead involved in storing and transmitting secret keys.
Data encryption made easy
How complicated is data encryption? It depends on how sophisticated your needs are. You can buy a simple encryption app for your laptop. That’s easy if it’s just for you. Managing encryption for a Fortune 500 corporation is a job for a team of people and some pretty powerful, expensive tools.
Encryption best practices should align with your broader security policies. It makes no sense and is too complicated and expensive to encrypt everything. Data encryption requires specialized software tools, including encryption software that can help manage encryption keys and support Bring Your Own Encryption (BYOE) in cloud environments.
You usually have to purchase keys directly or by buying an encryption product that embeds the keys in its functionality. Encryption slows down processes like emailing and data processing.
File encryption is a practical way to protect individual files, whether they are stored on local devices or in the cloud. For cases where the original data format must be maintained, such as phone numbers, format preserving encryption is available and is often used in cloud management software like Google Cloud and AWS.
It makes sense to be selective about encryption. You should encrypt data that is sensitive data that would have a negative impact on you or your business if it were breached, blocked by ransomware, or corrupted.
How to encrypt your data
You might wonder about actionable steps for basic data encryption on your devices. The good news is that many solutions are available at low or no cost. Android phones have full-device encryption if they run Android Gingerbread (2.3.x) or later. On Pixel Phones and Nexus 5+, encryption is by default.
You have to turn it on on earlier versions of Android, but it’s there. Setting up encryption on an Android device involves configuring a lock screen PIN, pattern, or password. Then in Settings/App Settings, you choose Security & Location. Where it says “Encryption” on this screen, select “Encrypt Phone.” That’s all it takes. You can do this process in reverse-to-end encryption.
For your computer, you can encrypt your data at rest with solutions from companies like Symantec, Kaspersky, Sophos, and ESET. You can also get encrypted USB drives. In addition, email can be encrypted through products like DataMotion SecureMail software, Proofpoint Email Encryption, and Symantec Desktop Email Encryption.
Data encryption best practices
Protect your encryption key
Although it should be very clear, it's possible to make mistakes that give unauthorized people access to your data. For instance, there is a considerable risk that someone may uncover your encryption key and cause havoc if you leave it in an unencrypted file on your computer. A few alternatives include:
- Keeping the keys distinct from the data
- Separating user roles and access restrictions
- Rotating your keys periodically.
Evaluate data encryption
Making your data unreadable to unauthorized parties is only one aspect of effective data encryption; another is doing so in a way that makes good use of the available resources. Consider using a new algorithm or playing with the parameters in your data encryption tools if encrypting your data takes too long or uses too much CPU and memory.
Encrypt all sensitive data types
This should also be obvious, but if you read the headlines about IT security, you are aware that many reputable businesses have been compromised simply because they left sensitive data unencrypted and allowed someone else to access it. Encrypting your data makes it much more difficult for someone who can hack into your systems to do bad things.
Key management and security
The security of encrypted data depends not only on the strength of the encryption algorithms but also on how well encryption keys are managed. Key management encompasses the secure generation, distribution, storage, and rotation of encryption keys, ensuring that only authorized users can decrypt data.
Both symmetric encryption and asymmetric encryption methods require careful key management—symmetric encryption relies on the same key for both encryption and decryption, while asymmetric encryption uses a public and private key pair. Secure key storage is essential to prevent unauthorized access, and regular key rotation helps minimize the risk of keys being compromised over time.
Additionally, organizations must have reliable backup and recovery processes in place to avoid data loss in the event of a disaster. By prioritizing robust key management practices, organizations can maintain the integrity and confidentiality of their sensitive data, ensuring that only those with the correct decryption key can access protected information.
Cloud-based data security
As more organizations move their operations to the cloud, cloud-based data security has become a top priority. Cloud storage providers offer a range of data encryption solutions designed to protect sensitive data both at rest and in transit. These solutions often include features such as access controls, auditing, and automated encryption processes.
One of the key benefits of cloud-based data encryption is scalability—organizations can easily adjust their security measures as their data storage needs grow. However, it’s crucial for organizations to maintain control over their encryption keys and ensure that their cloud provider complies with relevant data protection regulations.
By implementing cloud-based data encryption solutions and maintaining strong key management practices, organizations can protect sensitive data, achieve regulatory compliance, and benefit from the flexibility and cost-effectiveness of cloud storage.
Can encrypted data be hacked?
Encrypted data can indeed be hacked or cracked. Still, the feasibility and difficulty of doing so depend on several factors, including the strength of the encryption algorithm, the length and complexity of the encryption key, and the resources available to the attacker.
There are two main types of attacks that can be used to attempt to compromise encrypted data:
- Brute Force Attacks: In a brute force attack, an attacker systematically tries all possible combinations of encryption keys until the correct one is found. The effectiveness of a brute force attack depends on the length and complexity of the encryption key. The longer and more complex the key, the more difficult it becomes to crack the encryption using brute force. Modern encryption algorithms often use long keys designed to withstand brute-force attacks.
- Cryptanalysis Attacks: Cryptanalysis involves analyzing the encryption algorithm itself to discover vulnerabilities that can be exploited to decrypt the data without the encryption key. If a weakness is found in the algorithm, it may become possible to decrypt the data more efficiently than by brute force. This is why it's crucial to use well-vetted and widely accepted encryption algorithms.
Data security trends
The field of data security is rapidly evolving, driven by new technologies and emerging threats. One major trend is the widespread adoption of cloud-based services, which has increased the need for robust data encryption and advanced encryption algorithms. Organizations are also facing a growing threat from brute force attacks, making it essential to use strong encryption methods and regularly update their security protocols.
The use of advanced encryption algorithms, such as elliptic curve cryptography, is becoming more common, offering enhanced protection for sensitive data with greater efficiency. End-to-end encryption is also gaining traction, ensuring that data remains secure throughout its entire lifecycle. To maintain data integrity and protect against data breaches, organizations must stay informed about the latest data security trends and continuously improve their encryption and data protection strategies. By doing so, they can safeguard their sensitive data and ensure the ongoing security of their operations.
In practice, strong encryption algorithms with sufficiently long and complex keys are extremely difficult to crack using these methods. However, there have been cases where encryption has been compromised due to implementation flaws, key management issues, or advances in computational power.
It's important to note that the security of encrypted data also depends on factors such as the protection of encryption keys, proper implementation of encryption protocols, and safeguarding against side-channel attacks (where information is leaked through unintended channels like power consumption or timing).
As technology advances, it's important to stay informed about encryption best practices and to regularly update encryption methods to stay ahead of potential threats.
The future of data encryption
Data encryption and data security are constantly evolving to keep up with a worsening threat environment. While brute force decryption may be hard, hackers can still steal keys or attack places where encryption is suspended in the data management chain. For example, data is almost always encrypted through a computer’s Central Processing Unit (CPU). This is changing now, with chip makers like Intel introducing encryption tools for their CPUs.
The future of data encryption promises more innovations. These include encryption algorithms that incorporate biometrics and voice recognition—a sort of unique personal key. The industry is also introducing “Honey Encryption” traps that show a fake but plausible plaintext when a hacker guesses at the decryption key. Blockchain, which is not, strictly speaking, a form of encryption, makes use of encryption-like algorithms to ensure the integrity of data that is stored using a blockchain framework. There is likely to be a lot more of this kind coming in the future.
Using Prey to encrypt your data
Using the Prey Control Panel, you can control BitLocker for disk encryption on Windows 10 Professional, Enterprise, or Education editions, as long as a physical Trusted Platform Module (TPM) is installed and active. This feature lets you choose the specific disk you want to encrypt, monitor the encryption progress, and select your desired security standard from options such as AES128 and XTS_AES128. Simplifying disk encryption management, Prey empowers you to enhance the security of your Windows system effortlessly.
Conclusion
In conclusion, data encryption is a vital protection for sensitive information, ensuring data security. Throughout this article, we have dived into the intricacies of data encryption, emphasizing the need to protect confidential data.
While data encryption may require advanced technology, the availability of user-friendly solutions has made it more accessible, particularly for consumers. Encryption is seamlessly integrated into certain systems like iOS, strengthening data protection without user intervention.
For every organization, encryption should be an integral component of their security framework, preserving the integrity of business-sensitive data. Data encryption is an essential tool in your cybersecurity arsenal, and its adoption should be a priority.





