Navigating the uncharted territory of deployment of a 1:1 device technology program in a K-12 school district is not easy, but it comes with great rewards. In today’s educational landscape, one-to-one technology programs have emerged as catalysts for transformative learning experiences.
By lending students with learning devices, school districts empower them to access a vast array of other educational technology resources, collaborate with peers, and engage in personalized learning.
However, alongside the benefits of developing and integrating these programs, it’s a voyage with numerous questions - How can we ensure the security of these devices? What happens if a student forgets or loses their device? How can we handle the constant need for software upgrades and bug fixes? Additionally, some financial aid packages may include provisions for technology expenses like laptops, making it easier for students to participate in these programs.
In this article, we will guide you through the turbulence and ensure a smooth journey to your destination: to help you establish a functional, productive, and secure 1:1 technology program. Be sure to contact your school's financial aid office to check for available options and any limitations on spending the money.
What is 1 to 1 device program in schools?
One-to-one computing, also known as the 1:1 device program, equips each student with a personal learning device like a tablet, laptop, or Chromebook. It's a learning model where each student is given a digital device to foster an enhanced learning environment, blending traditional teaching methods with technological ones.
A 1:1 device program doesn't merely mean providing a digital device to students. It includes easy device enrollment, device management, device tracking, and device security processes. Schools often leverage Mobile Device Management solutions to oversee these processes effectively and maintain the security and utility of these devices. The idea is to make the transition from traditional learning methods to digital smooth and seamless.
Key advantages of implementing a 1:1 device strategy
Imagine a teaching environment where every student has their own device. With this scenario, the learning experience extends beyond the walls of the classroom, providing endless opportunities for deeper understanding and engagement. This is the power of the 1:1 device program in K-12 education. Rather than just being a tool, technology becomes an integral part of the learning process. Adopting a 1:1 device strategy brings a host of benefits, including:
- Personalized learning. Each student has unique learning styles and capabilities, and the 1:1 device program allows for individualized instruction that caters specifically to these needs. Students can progress at their own pace, use tools that best suit their learning, and access content that matches their skill level.
- Increased interaction and collaboration. Classrooms are imbued with a new dynamic wherein students can collaborate on projects in real time or teachers can provide instant feedback. This constant exchange of ideas fosters a more interactive, hands-on learning experience.
- Preparation for the future. Students become familiar with the technology that plays an exponential role in the professional world. This early adaptability imparts valuable digital literacy skills, ensuring students are workforce-ready.
- Democratizing technology use. 1:1 device programs are gradually breaking down the digital divide, a major hurdle to uniform education. By providing the same technology to students from varied backgrounds, these initiatives create a level playing field within educational settings for the vast majority of students and ensure every student has an opportunity to succeed.
Additionally, 1:1 programs can offer financial benefits by facilitating access to discounted laptops and student discounts on technology, ensuring students can access high-performing technology without exceeding their budget.
Challenges of managing a 1:1 device program
Managing student 1:1 device programs can be a daunting task. This is especially true considering the unique set of challenges that come with it. Below are some challenges that institutions may face when managing student laptop loans:
1:1 Rollout Cost
The price of starting a 1:1 program changes a lot based on the size of the school, the kind of technology, and the location. If your school or district has a small budget, it might need more money. This can be expensive at first, but if done right, it can stop schools from having to pay again and again for old textbooks and other materials. Students should also explore options for financial aid, as the financial aid office may offer assistance to help cover the costs of technology programs.
Lack of Physical Oversight
Without students physically present, ensuring the proper use and care of loaned laptops becomes challenging. To address this, establish clear guidelines and expectations for laptop usage, including responsible handling and regular maintenance checks.
Timely Return and Tracking
Remote learning can make it difficult to enforce return deadlines and track the whereabouts of loaned laptops. Implement a system that includes automated reminders for return dates and utilizes tracking software to monitor device locations.
Limited Device Visibility
Remote learning may limit visibility into how students are using loaned laptops, making it harder to identify potential misuse or unauthorized access. Promote digital citizenship and educate students about responsible online behavior to minimize risks. Additionally, consider using monitoring software that respects student privacy while providing insights into device usage patterns.
Device Damage and Maintenance
Without physical supervision, it's harder to prevent damage or address maintenance issues that may arise during remote learning. Encourage students to handle devices with care and provide resources for basic troubleshooting. Consider offering remote technical support to address maintenance concerns promptly.
To support and overcome these challenges, educational organizations can implement solutions Like Prey to regain control of campus, and mitigate the difficulties of managing student laptop loans during remote learning.
Partnering with Prey: the perfect solution for your 1:1 technology program
Prey allows educators and administrators to get full visibility and control of loaned devices. Prey helps educational institutions navigate the remote learning landscape more confidently, ensuring the safe and efficient management of student laptop loans.
With the ever-growing number of devices in use, the responsibility of maintaining the safety of business and educational fleets and adhering to regulations becomes a challenging task. This is where Prey's Device Suite steps in as a powerful solution.
Additionally, Prey can assist in the management and security of devices provided through free laptop programs offered by educational institutions, enhancing access to technology for online learning.
Effective device tracking & monitoring
Educational organizations can reap numerous benefits from Prey's advanced device tracking and monitoring capabilities. By leveraging Prey's tracking technology, institutions gain real-time visibility into the whereabouts of their devices, ensuring their safety and preventing loss or theft. Through GPS, Wi-Fi triangulation, and geo-IP, Prey enables the creation of geofences and alerts, allowing educational institutions to set virtual boundaries and receive notifications when devices enter or exit specific areas.
With Prey, managing device location becomes a breeze, providing a layer of protection that benefits both students and educational organizations. Prey's tracking capabilities can be an essential feature for educational institutions that offer loan laptops.
By leveraging Prey's tracking and geofencing technologies, educational organizations can effortlessly manage loans, reduce the risk of loss or theft, and maintain the safety of their valuable assets. Prey offers a wide range of security benefits that go beyond a mere tracking tool:
- Loss Prevention
Devices tend to grow legs and often go on unexpected adventures. However, IT admins can swiftly locate missing, stolen, or rogue devices that fail to comply with persistent tracking tool capabilities. This minimizes losses and ensures that valuable resources are not misplaced. - Prevent Unauthorized Use
When a security incident happens, uninvited guests attempting to access school devices can pose a significant threat. Prey allows IT schools to detect and lock the device to prevent unauthorized access, protect student data, and maintain a secure learning environment. - Identifying location and usage Patterns
Prey offers insights into device location and activity patterns that seem off and can potentially lead to security policy breaches. IT teams can identify trends and understand student device behavior. - Maintenance and Support
Devices require regular maintenance and occasional troubleshooting. Prey offer valuable HW information, enabling IT teams to proactively address maintenance needs, provide timely support, and minimize disruptions to the learning process.
Device loan manager for your 1:1 college student program
Prey offers an excellent solution for educational organizations looking to implement a Device Loan Manager for their 1:1 student programs. This comprehensive tool allows institutions to track and manage the distribution and return of devices easily.
With Prey's Device Loan Manager, schools can set loan periods, send automatic reminders to borrowers, and receive notifications when loans are overdue. This streamlines the loan process, ensuring accountability and enabling efficient management of device loans within the educational ecosystem.
Additionally, Prey's Device Loan Manager is an effective tool for managing free laptop programs, supporting colleges in providing essential technology to students.
Visibility and inventory of refurbished laptops assigned to faculty and students
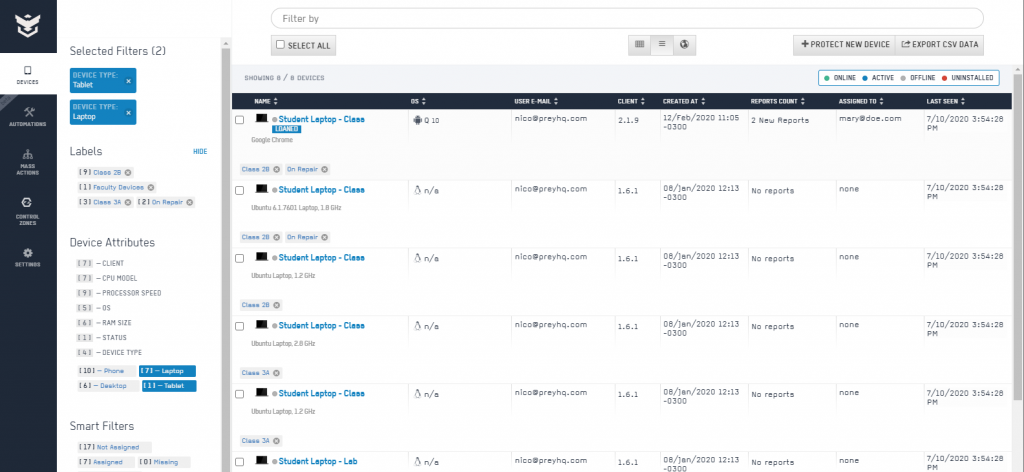
Educational organizations can greatly benefit from Prey's visibility and inventory management features. Prey allows institutions to maintain an organized inventory of laptops assigned to both faculty and students. With customizable labels and filters, it becomes effortless to group and locate devices based on their assigned users, technical attributes, or other customized criteria. This level of visibility enables efficient tracking, easy identification of devices, and streamlined device management for educational institutions.
How can Prey help with this:
- Organized Device Inventory
Prey enables educational institutions to maintain a centralized inventory of laptops assigned to both faculty and students, ensuring easy access and tracking. - Customizable Labels and Filters
Institutions can categorize devices based on assigned users, technical attributes, or other customized criteria, allowing for efficient sorting and identification of laptops. - Quick Device Location
With enhanced visibility, administrators can easily locate laptops assigned to specific individuals or departments, reducing search time and streamlining device management. - Tracking Device Utilization:
Prey's inventory management features provide insights into device utilization patterns, allowing educational organizations to optimize their resources and plan future investments.
Accountability and management of laptop loans
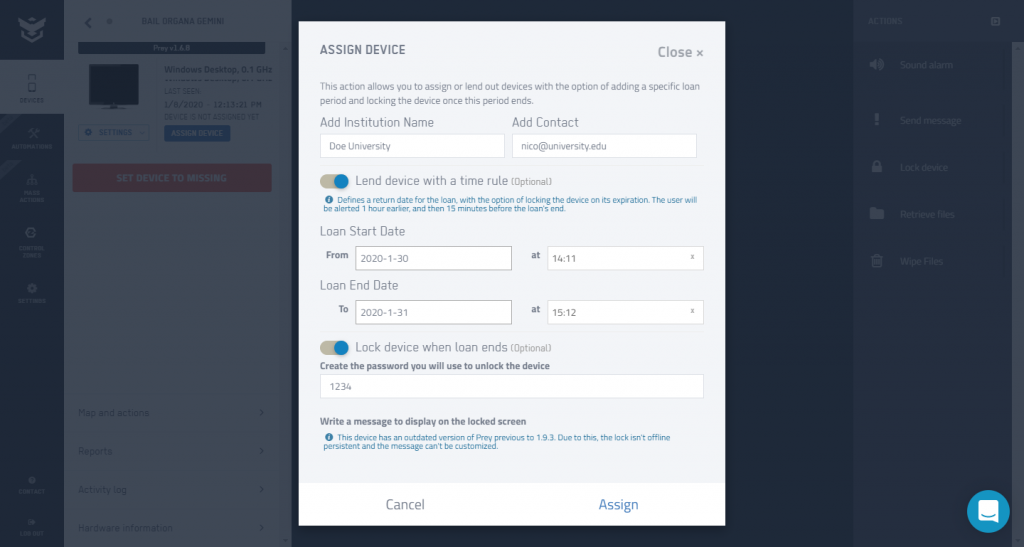
Prey's comprehensive suite of features empowers educational organizations to establish accountability and effectively manage laptop loans. With the ability to assign users, set return dates, and activate security measures when loans are overdue, Prey ensures that devices are properly accounted for and returned on time. By automating loan management processes and providing timely notifications, Prey simplifies the administrative burden and enhances the overall efficiency of laptop loan programs.
How can Prey help with this:
- User Assignment
Prey allows educational institutions to assign laptops to specific users, ensuring clear accountability and ownership of devices. - Return Date Alerts
Administrators can set return dates for loaned laptops, and Prey sends notifications to borrowers as the deadline approaches, facilitating timely returns. - Overdue Loan Security Actions
In cases of overdue loans, Prey enables administrators to activate security measures like remote locking, wiping, or sending alert messages to the devices to ensure compliance with loan policies and protect the institution's assets.
Incident response action
Implementing an incident response action plan is crucial for educational organizations, and Prey offers a robust solution in this regard. With Prey, institutions can swiftly respond to incidents like loss, theft, or even rogued devices. Through features like remote locking, alarming, and message alerts, administrators can take immediate action to locate and secure the devices.
Prey's incident response capabilities enable educational organizations to mitigate risks and ensure the safety of their devices and sensitive data.
How can Prey help with this:
- Remote Locking
In case of loss or theft, Prey allows administrators to lock laptops remotely, preventing unauthorized access to sensitive data and protecting the institution's information. - Alarming and Message Alerts
Prey enables the activation of alarms and message alerts on lost or stolen laptops, increasing the chances of their recovery and discouraging theft. - Geolocation Tracking
With GPS and Wi-Fi triangulation, Prey helps educational organizations locate misplaced or stolen devices, aiding in their recovery. - Data Protection
By implementing incident response actions, institutions can protect student and faculty data stored on laptops through Prey’s Remote Wipe feature, mitigating the potential impact of a security breach.
Prey-tecting the future: safeguarding student laptop loans
Prey's ability to address the unique challenges of remote learning, such as limited oversight and device protection in compliance with FERPA regulations, makes it an invaluable tool for educational institutions. With its robust features, Prey streamlines loan tracking, enhances device security, and simplifies inventory management. It's like having a virtual guardian angel for your laptops, ensuring they stay safe and sound.
By providing remote tracking, location services, and incident response actions, we can equip IT administrators with the necessary tools to protect their institution's assets and safeguard student and faculty data. With Prey, educational organizations can have peace of mind, knowing that their student laptop loans are well-managed and protected in the remote learning environment.
Frequently Asked Questions
What percentage of schools have 1 1 devices?
Approximately 63% of schools in America have 1:1 device programs, with an increasing trend expected to continue. This indicates a growing adoption of such programs per school day.
What is a 1 1 device program?
A 1:1 device program is an educational initiative where schools provide each student with their own personal computer or learning device. This program is also known as one-to-one technology or one-to-one computing.
How do 1:1 device programs benefit student learning?
1:1 device programs benefit student learning by increasing engagement, supporting personalized learning, and bridging the digital divide to ensure equal access to technology for all students. This ultimately leads to improved learning outcomes and student success.
What role do teachers play in a 1:1 device environment?
In a 1:1 device environment, teachers play a crucial role in facilitating individualized learning experiences, guiding students, tracking progress, setting goals, and fostering peer collaboration. This helps transition from traditional instruction in classes to a more personalized approach.
How can schools fund and sustain a 1:1 device program?
Schools can allocate budget for the full cost of ownership and seek extra funding through grants, partnerships, and federal programs to sustain 1:1 device programs. This will help to cover both initial and ongoing expenses without overburdening the teacher or school budget.






