Your firewall might be rock solid, but attackers aren't even trying to break it down anymore. Let's be frank: attackers are increasingly sidestepping it for an easier target – your people. And in today’s work-from-anywhere reality, your old concept of a perimeter has dissolved. It's no longer just the office walls; it’s every employee, contractor, and remote device, scattered across countless SaaS apps and home networks. This isn't just an expansion; it's a complete redefinition of your attack surface, all centered on who has access, not just where they are.
It takes just one reused password from that "totally secure" cat photo website, or a single phished login, and those critical identities—the digital keys to your kingdom—can be compromised. These aren't just random bits of data; they're valuable commodities, actively traded like stocks on the bustling, shadowy marketplace of the dark web by everyone from initial access brokers looking to sell entry points, to ransomware gangs eager to deploy their payloads.
The unfortunate truth is, stolen credentials are the universal skeleton key, yet many traditional security playbooks are still playing catch-up to this identity-centric threat. Protecting your organization now means shifting from reactive cleanups to proactive vigilance. It's about spotting those leaked identities before they unlock your doors and execute Order 66 on your systems, not after you’re staring down the barrel of a breach notification and a very long night.
What is the identity perimeter, and why should you care even more now?
Given this distributed reality, think of the identity perimeter as every single digital key that unlocks a door to your company’s assets, wherever those assets or users may be. We're talking user accounts, passwords, API tokens, session cookies – essentially, anything that says "Yep, this person (or thing) is legit, let 'em in." It’s no longer just about who’s on the network but who can authenticate into your systems, from literally anywhere on the planet.
The identity perimeter is everything that grants someone—or something—access to your systems. We're talking about user accounts, credentials, and access tokens that act as digital keys to your environment. It's no longer just about who’s on the network, but who can get in, from anywhere.
This includes:
- Your tireless employees (navigating work from home, coffee shops, and everywhere in between).
- The ever-growing list of contractors and third-party vendors (often accessing systems remotely).
- Those sneaky service accounts that run in the background (connecting various cloud services).
- Every remote device – laptops, phones, tablets – each a potential entry point.
The massive shift to SaaS apps further scatters your control points across the cloud. Add remote and hybrid work, and the number of identities and devices just explodes. It's a headache, we get it. And while Multi-Factor Authentication (MFA) is your best friend here (seriously, use it everywhere), leaked credentials can still find ways to bypass controls or provide attackers with that crucial first foothold into your dispersed environment.
How the Dark Web powers identity attacks
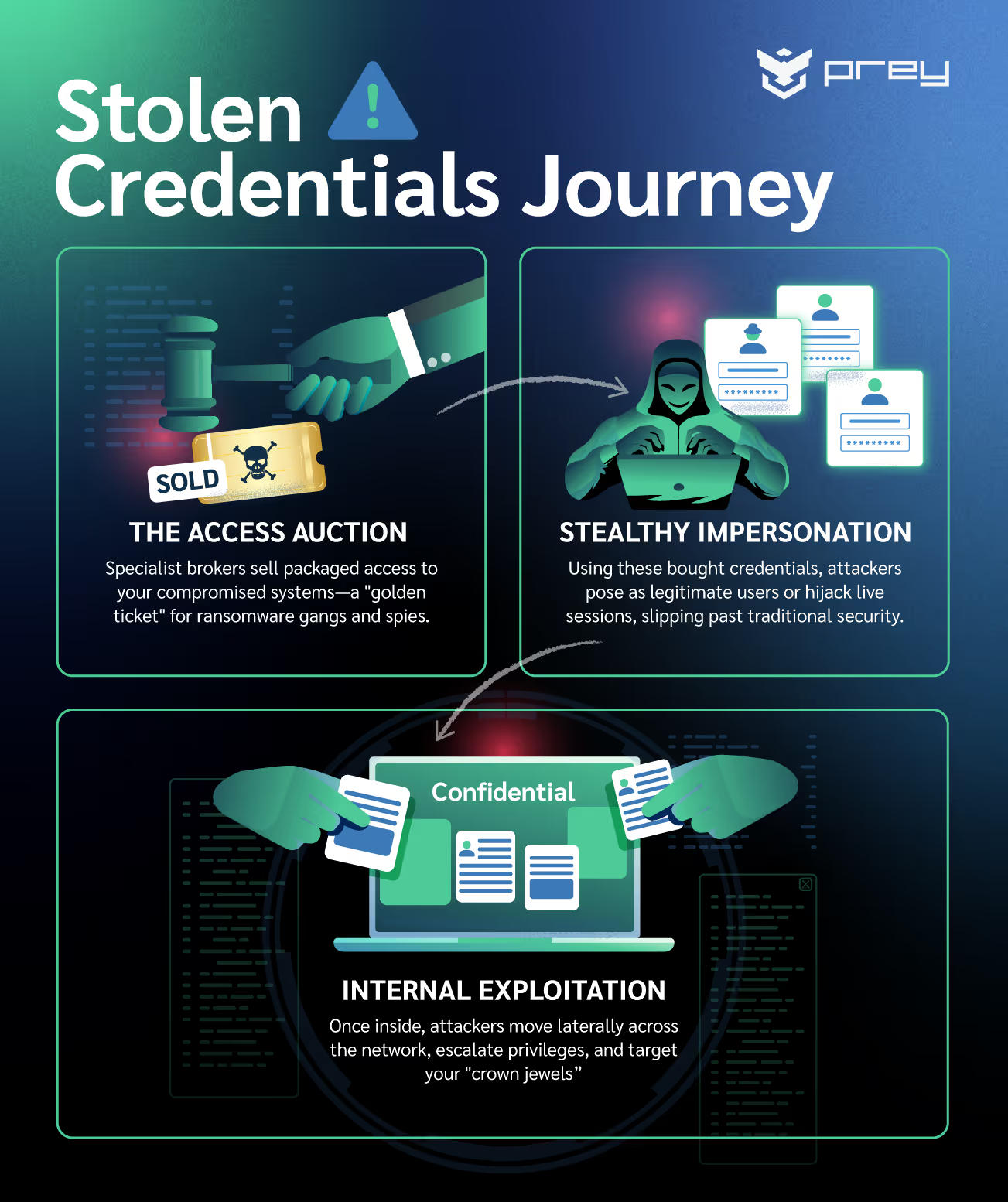
The dark web isn’t just a shady corner of the internet: It’s a full-blown marketplace for stolen credentials. Usernames and passwords, session cookies, admin tokens, everything’s up for grabs. Once your access is out there, it’s only a matter of time before someone picks it up and uses it against you.
According to the 2025 Verizon Data Breach Investigations Report, stolen credentials remain a prevalent initial access vector, accounting for 22% of breaches. Additionally, 88% of basic web application attacks involved the use of stolen credentials, highlighting the critical need for robust identity protection measures.
Here’s the typical lifecycle of those stolen goods:
- Initial access brokers: These aren't your script kiddies. These access brokers are specialists in cracking the outer shell of organizations. Once they're in, they don't stick around; they package up that access and sell it to the highest bidder. Your compromised login could be the golden ticket for a ransomware operator or a state-sponsored group.
- Phishing & session hijacking: Credentials harvested from phishing campaigns or info-stealing malware are gold. Attackers can reuse them to waltz into active sessions or impersonate legitimate users, often flying under the radar of traditional security tools.
- Lateral movement & privilege escalation: Once inside, it’s like a game of hide-and-seek, but not fun. Attackers use internal accounts, often moving from a low-privilege user to eventually snagging domain admin rights. They’re looking for the crown jewels – your sensitive data, financial systems, or the launch button for ransomware. And they’ll do it quietly if they can.
The real-world fallout of reused logins
The Colonial Pipeline attack is a textbook case. Attackers didn’t need zero-days or brute-force tactics—just a single reused password tied to an inactive VPN account. No MFA, no alerts, just open access. That one set of credentials led to a massive ransomware incident and fuel shortages that rippled across the U.S. East Coast.
In another example, 23andMe was hit by a credential stuffing attack in 2023. Bad actors reused leaked usernames and passwords from other breaches to break into user accounts. The fallout? Sensitive personal and genetic data from over five million users exposed. That’s the real cost of treating credential reuse like a low-risk issue.
Identity exposure risk factors
If you want to stay ahead of attackers, you need to know where you're vulnerable—before they figure it out for you. Most breaches don’t start with sophisticated exploits; they start with something simple that got overlooked. When it comes to the identity perimeter, small gaps can lead to big consequences. Knowing where you're vulnerable is the first step to locking things down.
Here are some common identity risk factors—and why they matter:
- Poor password hygiene: We know, users hate complex passwords. But reusing "Password123!" across twenty services, including their corporate login? That's just asking for trouble. One leak, and the dominoes fall.
- Dormant accounts left active: Oh, the ghosts of employees past. Those accounts from ex-staff or old vendors are often forgotten, unmonitored, and perfect, silent backdoors for attackers. This is an audit point waiting to happen.
- Lack of credential leak monitoring: If you’re not actively looking for your company’s credentials on the dark web, you’re essentially relying on luck. Attackers are looking. You should be too. This isn't about paranoia; it's about proactive defense.
- No real-time alerting on key identity assets: If a high-privilege account suddenly logs in from a new country at 3 AM, you want to know now, not next week. Delayed alerts mean more dwell time for attackers.
- Weak onboarding/offboarding processes: When someone joins, do they get just the access they need (hello, principle of least privilege!)? When they leave, is all access revoked promptly and thoroughly? Gaps here are common and dangerous.
Defending the identity perimeter — A multi-layered strategy
Protecting your network used to mean building a strong perimeter. Now, it means securing who has access, not just where they’re coming from. When identities are the entry point, you need more than one line of defense. A layered approach helps close the gaps, reduce exposure, and stay ahead of threats trying to walk in with valid credentials.
Here’s how to build that defense:
IAM best practices are your bedrock:
- Principle of Least Privilege (PoLP): Seriously, only give users the access they absolutely need to do their job. No more, no less.
- Single Sign-On (SSO): Streamlines access, improves user experience, and gives you a central point of control.
- Role-Based Access Control (RBAC): Defines permissions based on roles, making it easier to manage and audit.
- Regular Access Reviews: Don't "set it and forget it." Periodically review who has access to what, especially for critical systems. This is key for compliance too (think SOX, HIPAA).
MFA everywhere (Yes, really everywhere):
- It’s not just for email and cloud apps. Your VPNs, internal admin dashboards, legacy systems (where possible) – all need MFA. Every additional factor is another hurdle for an attacker with stolen creds. This is a non-negotiable in today's world.
Champion credential hygiene:
- Encourage (or mandate) password managers.
- Enforce strong, unique passwords. Create policies that make reuse difficult or impossible.
- User training is good, but technical controls that prevent bad practices are better.
Proactive Dark Web Monitoring (This is where you turn the tables)
- You can’t stop what you can’t see. Monitoring for leaked credentials lets you act before attackers do. Tools like Prey can surface compromised logins, trigger remote actions on affected devices, and help contain a breach faster—without waiting for alerts from someone else’s SOC.
- This isn't just about finding a needle in a haystack; it's about getting an alert when the needle first appears, giving you time to act. This helps with compliance (e.g., GDPR's requirement for timely breach notification/mitigation) and significantly reduces potential damage and recovery costs.
Incident Response for Identity (Have a plan, practice it):
- When things go wrong—and they will—you need to move fast. That means having playbooks and tooling ready to lock users, wipe or quarantine devices, reset credentials, and rotate keys without hesitation.
- Ensure your tools allow for rapid response. Being able to remotely lock or wipe a device tied to a compromised credential can be a game-changer.
Learn more about how to add Dark Web monitoring to your Incident Response Plan
Own your identity perimeter before attackers do
You can’t always control where your data ends up—but you can decide who gets through the door. Identity-first security means getting ahead of threats, not reacting once the damage is done. If you’re not watching for exposed credentials on the dark web, there’s a good chance someone else is—and they’re not doing it to help you**.**
Ready to stop credential-based attacks before they escalate?
Prey’s Breach Monitoring, integrated with our leading device tracking and security platform, gives you the early warning and rapid response capabilities you need.
- Discover if your company's credentials are on the dark web.
- Pinpoint affected users and devices instantly.
- Act fast to lock down accounts and secure endpoints.
- Reduce your risk and strengthen your compliance posture.
Check your dark web exposure and see how Prey helps you take control of your identity perimeter.






